Some of these seemingly independent VPNs are all connected – and they pose a threat to your data
A new study has revealed hidden links between the apps

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
An academic study has revealed hidden links between a number of VPNs, with apps sharing ownership and even security flaws.
These apps can in no way be considered some of the best VPNs, but they are popular. The combined Google Play Store downloads of them exceed 900 million.
Earlier this year, we reported on VPNs having links to the Chinese military. Investigations were carried out by the Tech Transparency Project (TTP) and this study builds upon the TTP's work.
Many apps uncovered by the TTP appear in the new study and can be grouped into "families" – sharing developers, code, and vulnerabilities.
Many of these VPNs are free or have free versions. Here at Tom's Guide, we always recommend subscribing to a paid VPN over a free one. You get more features, faster speeds, and an all-around better VPN experience.
However, certain free VPNs are a safe option for those who don't want to pay or can't pay. But you should always choose a reputable provider, and our best free VPN guide can help you make that choice.
18 apps have hidden links
The study was titled "Hidden Links: Analyzing Secret Families of VPN Apps" and researchers investigated the top 100 most downloaded apps, according to SensorTower and AppMagic.
This was then filtered down to 50 after excluding apps US-based providers. Information was then collected from the apps Google Play page, website, GitHub, and social media. The app's Android Package Kit (APK), DNS records, and wider code was also investigated in a security analysis.
The researchers goals were to identify VPN-specific security threats and "uncover deception via provider linkage."
VPN server IP addresses, proxy traffic, API connections, VPN protocols, and layers of code were all examined, with 18 VPN apps being sorted into three groups – Families A, B, and C.
Family A:
App | Developer | No. of downloads |
Turbo VPN | Innovative Connecting | 100 million+ |
Turbo VPN – Lite | Innovative Connecting | 50 million+ |
VPN Monster | Innovative Connecting | 10 million+ |
VPN Proxy Master | Lemon Clove | 100 million+ |
VPN Proxy Master – Lite | Lemon Clove | 10 million+ |
Snap VPN | Autumn Breeze | 50 million+ |
Robot VPN | Autumn Breeze | 10 million+ |
SuperNet VPN | Autumn Breeze | 1 million+ |
Family A was made up of eight apps, from three providers. Other research has linked all these providers to the holding company Lemon Seed, which is in itself linked to Qihoo 360 and the Chinese military.
All these apps shared code, APKs, infrastructure, signatures, and weak encryption.
Family B:
App | Developer | No. of downloads |
Global VPN | MATRIX MOBILE PTE LTD | 10 million+ |
XY VPN | MATRIX MOBILE PTE LTD | 100 million+ |
Super Z VPN | Super Z VPN (Privacy & Proxy) | 10 million+ |
Touch VPN – Stable & Secure | The Tool Tech | 50 million+ |
VPN ProMaster–Secure your net | Fruit Security Studios | 50 million+ |
3X VPN – Smooth Browsing | Fruit Security Studios | 100 million+ |
VPN Inf | WILDLOOK TECH PTE. LTD. | 10 million+ |
Melon VPN – Secure Proxy VPN | WILDLOOK TECH PTE. LTD. | 50 million+ |
These apps were found to use the same IP address, from the same hosting company. Two of these app's privacy policies also mentioned Innovative Connecting. Similar code structures and weak encryption was also found.
Family C:
App | Developer | No. of downloads |
X-VPN | FreeConnectedLimited | 50 million+ |
Fast Potato VPN | Fast Potato ptd ltd | 10 million+ |
Fast Potato was found to have no business filings according to OpenCorporates. The code of these two VPNs was found to be "structurally and functionally similar" and included the same custom VPN protocol.
Other:
App | Developer | No. of downloads |
Tetra VPN | Miczon LLC | 1 million+ |
VPN – Super Unlimited Proxy | Super VPN Inc | 100 million+ |
Secure VPN Safer Internet | Secure Signal Inc | 100 million+ |
Three apps were grouped into an "Other" category as they weren't found to share any links. We still consider them potentially unsafe and we'd recommend you avoid them.
Secure VPN Safer Internet says it doesn't record any of your personal information. However its privacy policy states it collects system data and metadata. It says it retains non-personal information for as long as needed, unless instructed otherwise. However its Google Play Store page states you can't request deletion of this data. There's also no indication of a no-logs audit.
VPN Super Unlimited Proxy's privacy policy says it collects a variety of data including IP address and device information but does not store your IP address or VPN browsing activity. However this policy has not been independently audited. Its free VPN versions allow third-parties to collect information including device specific information and your IP address.
Despite having over 100 million downloads, VPN Super Unlimited Proxy's X account appears to have 34 followers and was created in June 2025. The profile also states that the app has over 1 billion downloads.
As for Tetra VPN - Fast Proxy by Miczon LLC, it appears that the app has been pulled from Google Play.
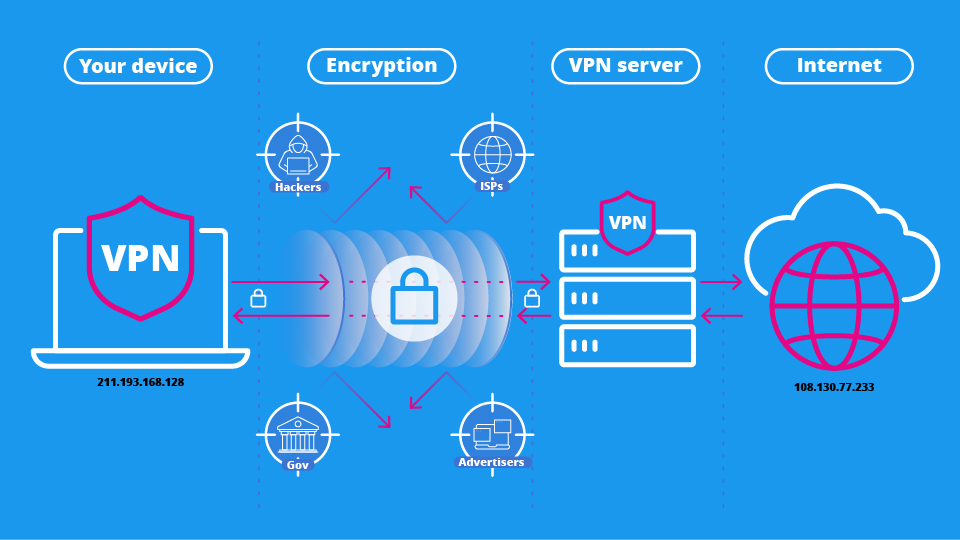
How to stay safe
We have highlighted some of these VPN apps and developers before and strongly advise against downloading any of them.
Your personal data may be at risk and the apparent murkiness of their ownership and development leaves us asking who can and can't see your data.
Reputable VPN providers pride themselves on upholding the highest standards of privacy and security and operating strict no-logs policies.
Many of the VPNs analyzed in this study fail to adhere to these security standards and researchers were able to decrypt information.
These weaknesses stem from the use of Shadowsocks, a proxy used to circumvent the Great Firewall of China. Shadowsocks isn't designed to protect privacy, merely bypass censorship.
This research highlights the dangers posed by unchecked VPNs and reinforces how important it is to download reputable VPNs.
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.

George is a Staff Writer at Tom's Guide, covering VPN, privacy, and cybersecurity news. He is especially interested in digital rights and censorship, and its interplay with politics. Outside of work, George is passionate about music, Star Wars, and Karate.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits










