New ZeroDayRAT spyware gives hackers total control over your iPhone or Android — and it all starts with a text
From hijacking your accounts to tracking your every move in real-time

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
Whether you use an iPhone or an Android phone, hackers have a brand new tool that’s capable of completely hijacking it to steal your data, track your location, log your keystrokes, intercept your 2FA codes and more. The worst part? The tool is sold on the dark web with full customer support in case they run into any problems.
As reported by BleepingComputer, the new ZeroDayRAT malware is a commercial mobile spyware platform that’s currently being advertised to cybercriminals on Telegram. Thanks to its very detailed dashboard, any hacker that deploys this malware in their attacks is easily able to manage infected devices while stealing all of their data and tracking them in real-time.
Here’s everything you need to know about this new mobile threat along with what it’s capable of, along with some tips on how to stay safe so you can recognize a potential infection before it takes over your phone.
Full access to your device, location and more
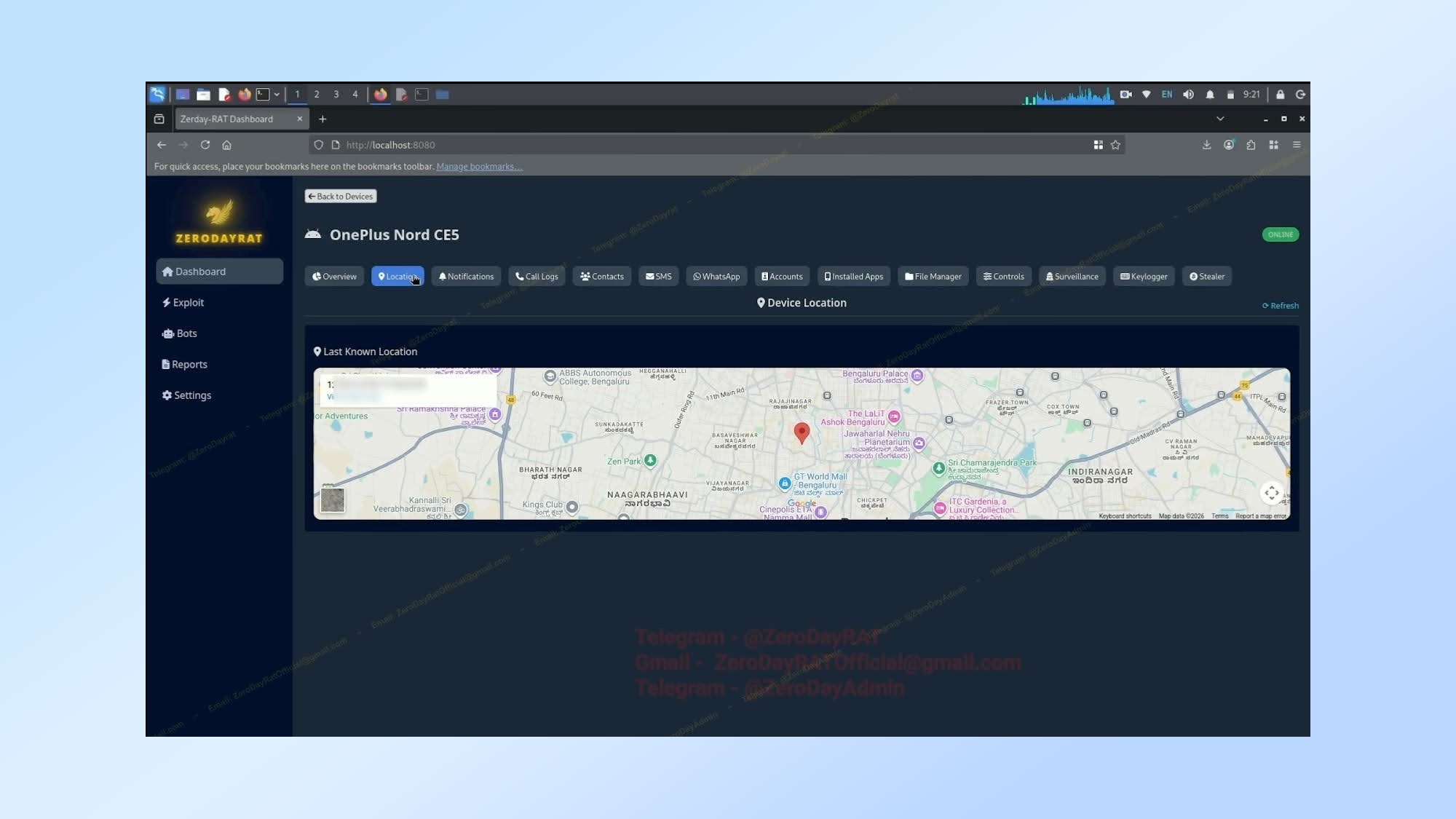
ZeroDayRAT acts like a one-stop shop for hackers when it comes to the sensitive data, login info and crypto stored on one of the best iPhones or best Android phones. And to make matters worse, it can allegedly infect devices running the latest software, whether that be iOS 26 or Android 16.
In a new report, researchers at iVerify explain that they first discovered ZeroDayRAT after seeing it openly sold on Telegram at the start of this month. In addition to customer support, the malware’s developer also provides regular updates so it will remain a viable tool in a hacker’s arsenal for even longer.
A hacker can also use ZeroDayRAT to activate a phone’s front and rear cameras and microphone to spy on victims. From there, GPS access gives them the ability to track a victim’s location in real time.
ZeroDayRAT is quite sophisticated on its own with the ability to glean all kinds of useful information from an infected device. Besides a phone’s make and model, operating system version, battery life, SIM details, country of origin and lock state, the malware can also log a victim’s app usage, their text messages, notifications and more. Likewise, a hacker can also use ZeroDayRAT to activate a phone’s front and rear cameras as well as its microphone to spy on victims in real-time.
From there, GPS access gives them the ability to track a victim’s location in real time and even see their current position on Google Maps. Then with SMS access, ZeroDayRAT can capture one-time passwords to bypass two-factor authentication (2FA) which lets an attacker take over a victim’s social media and banking accounts.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
If that wasn’t enough, the malware even features a cryptocurrency stealer module that scans an infected device to look for wallet IDs and balances from Coinbase, Binance, MetaMask and Trust Wallet. As we’ve seen with other malware in the past, ZeroDayRAT also uses overlay attacks to steal online banking logins as well as credentials for Apple Pay, Google Pay and PayPal.
Perhaps the most surprising thing about ZeroDayRAT for me though is its online dashboard. Right from their browser, hackers have all the info they need from devices they’ve infected with the malware to launch additional attacks and keep tabs on any that are currently underway. It’s clear a lot of work went into creating this new spyware platform and depending on how much it costs, ZeroDayRAT could become a household name among cybercriminals.
How to stay safe from spyware

As iVerify points out in its report, a ZeroDayRAT infection begins by getting a malicious binary onto a targeted device: either as an APK for Android or a payload for iOS. While we don’t know exactly how cybercriminals are spreading this spyware yet, the firm’s security researchers believe that SMS phishing or smishing is likely the easiest infection method.
Whether you have an iPhone or an Android device, you want to be on the lookout for text messages from unknown senders containing a link that try to coerce you into downloading an app. They might use a sense of urgency or other common tactics to do so. While fake text messages are one probable delivery method, phishing emails, fake app stores and links on WhatsApp or Telegram are other ways the ZeroDayRAT spyware can be distributed too.
To stay safe from this new mobile threat, your best bet is to avoid clicking on any links sent to you via text messages, emails or through social media. It’s always best to avoid clicking on anything sent from an unknown sender but I’d also recommend being wary of links sent from friends or even acquaintances that you haven’t spoken with in a while. Once hackers take over one person’s accounts, they often use them in other attacks. A message from an old friend on social media about a new app that’s changed their life or made a common task a lot easier is the kind of lure that I could easily see unsuspecting users falling for.
In order to stay safe from the latest threats, you should be using the best antivirus software on your PC or the best Mac antivirus software on your Apple computer. On mobile, the best Android antivirus apps can keep your phone safe from malware but due to Apple’s own restrictions, there aren’t any antivirus apps for iPhone. However, many antivirus makers do offer protection for iOS through their main software suites. For instance, Intego’s Mac antivirus can scan an iPhone or iPad for malware but only when it’s connected to a Mac via a USB cable.
While we haven’t heard about any major attacks carried out using the ZeroDayRAT yet, chances are, we likely will soon. I’ll be keeping a close eye on this new mobile spyware platform just in case. In the meantime though, by practicing good cyber hygiene and being careful where you click or tap, you should be able to avoid falling victim to the ZeroDayRAT and other mobile malware.
Follow Tom's Guide on Google News and add us as a preferred source to get our up-to-date news, analysis, and reviews in your feeds.
More from Tom's Guide
- 149 million logins and passwords exposed for Gmail, Facebook, Instagram and more — everything you need to know
- Total phone hijack: New Hugging Face malware grants hackers full remote access
- Massive government tech data breach expands to more than 25 million more Americans a year after it was discovered

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits










