VPN Glossary: key terms explained
Kill switches, DNS, geo-spoofing – what does it all mean?

Virtual Private Networks (VPNs) are, undeniably, handy pieces of kit for anyone who values their digital privacy. They can put a stop to snooping cybercriminals, invasive ads, and ISP (internet service provider) throttling that can grind your streaming sessions to a halt.
Unfortunately, the language used on provider sites can be super-techy and obscure.
If you've ever wondered just what encryption is, exactly, or the difference between a DNS leak and an IP leak, you’re not alone – and I'm here to help.
I've picked out the terms you're likely to come across when shopping around for the best VPN in the business. I've summed up each one with a jargon-free explanation that'll help you wrap your head around the key VPN concepts – whether you're totally new to the tech or have some experience under your belt.
We rate NordVPN as the best VPN for most people. Its fast, great for streaming, boasts excellent privacy and security, and has a load of extra features. All plans grant you VPN protection for 10 devices.
The two-year plan starts at $3.09 per month ($83.43 up front pre-tax). You'll also get an extra 3 months free and a 30-day money-back guarantee.
Advanced Encryption Standard (AES)
Advanced Encryption Standard (AES) is an encryption cipher that determines how data is encrypted and decrypted.
AES is an industry's gold standard, and you'll often find it described alongside the key length. AES-128 uses a 128-bit key, for example, whereas AES-256 encryption uses a 256-bit key. The more bits, the stronger the encryption, and AES encryption is virtually uncrackable (even when tested by brute force attacks).
Despite the introduction of post-quantum encryption. Many VPN providers still utilise AES-256.
Auto-Renewal
For almost all VPNs, your subscription will auto-renew unless you disable this action.
Renewal prices tend to be far more expensive than the attractive offers first advertised to you as a new customer. Our research saw price increases of up to 300%.
We recommend disabling auto-renew and cancelling your subscription once it expires. You can then re-subscribe at the cheaper price you first signed up with.
Black box
Auditors use a "black box" testing technique to check out VPN services from the point of view of an everyday user – like you and me.
While black box testing lets the auditor install and run the VPN, it doesn't allow them to comb through the service's app and server source code. That requires a "white box" test.
Catapult Hydra
A proprietary VPN protocol developed by Hotspot Shield. It uses TLS 1.2-based security and is based on the OpenVPN protocol.
Cipher
Ciphers contain rules for data encryption and decryption. They transform your data from readable (plaintext) to unreadable (ciphertext). A secret key is used when encrypting data and only by using the correct key can you decrypt the data.
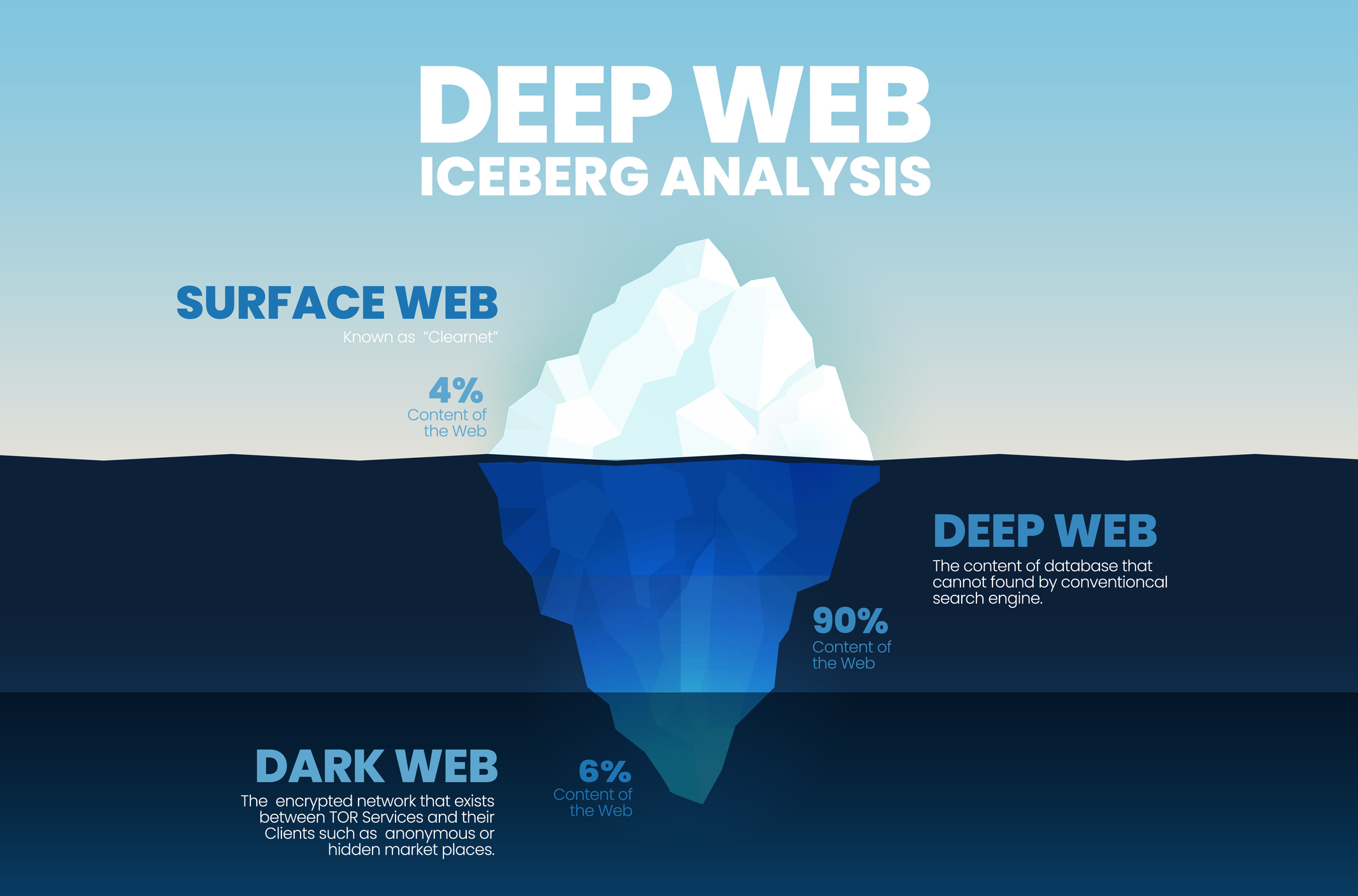
Dark web
Web content that lives on darknets, which are only accessible to savvy users with specific software. The TOR network is the most popular of these.
DCO
Data Channel Offload (DCO) is designed for the OpenVPN protocol and aims to improve its speed and performance.
OpenVPN runs entirely on software and this includes the intensive encryption and decryption process. A DCO moves this process from the software to a kernel in your device's operating system.
This streamlines encryption and improves OpenVPN performance while maintaining security.
Dedicated IP
When you connect to a VPN server, you'll receive a VPN IP address and this is often shared with multiple users.
Dedicated IP grants you a unique, location fixed IP that only you can use. Using one can improve performance and reduce CAPTCHAs.
Many leading providers – Proton VPN being the biggest exception – offer Dedicated IP as a paid add-on. ExpressVPN includes Dedicated IP in its new ExpressVPN Pro plan.
Deep Web
Similar (but not the same as) the dark web, the deep web is any site that isn't indexed by search engines – think Google, Bing, etc. You can access these deep web sites via a direct URL or IP address, but you might need an additional password to view content.
Deep web sites are used for online banking, email providers, and forums where you'll need an account to join the conversation and check out content.
DD-WRT
Firmware you can use to improve your wireless router's performance: better speed, more features, and extended functionality. You'll need to "flash" your router to do this, however, which can be risky. Lots of VPNs are compatible with DD-WRT (including ExpressVPN and NordVPN), meaning you can set them up on a range of wireless routers.
"DD" is a reference to Dresden, in Germany, where DD-WRT firmware was initially developed. "WRT" means wireless router.
Deep Packet Inspection (DPI)
Filtering technologies that inspect network traffic to understand its purpose. DPI uses pre-defined criteria to check out traffic, find viruses, malware, hackers, spam, and other threats, and block them.
Unfortunately, DPI can also be used by repressive government regimes to monitor its citizens' online activity.
When you connect to a VPN, your traffic is encrypted and much harder for snoopers to inspect with DPI. That means you can go about your browsing with added peace of mind.
Censorship-resistant VPN protocols are specifically designed to evade DPI.
Device Connections
A VPN provider will include device connections in its advertising. This refers to the number of devices you can protect on one VPN plan and the number of devices that can simultaneously connect to your VPN.
Premium VPNs will protect multiple devices on one plan, while the best free VPNs usually only protect one. ExpressVPN can protect anywhere between 10 and 14 devices (depending on your plan), NordVPN and Proton VPN protect 10. Surfshark and Private Internet Access protect an unlimited number of devices.
Surfshark sits at #2 on our best VPN list and is the best cheap VPN out there. You can protect an unlimited number of devices on one plan with high-class privacy and security. It unblocked all streaming sites we tested it with and it has some unique features such as Alternative ID.
Prices start at $1.99 per month ($53.73 up front pre-tax) for 27 months of protection. There's also a 30-day money-back guarantee and even a free trial.
Domain Name System (DNS)
Dubbed "the phonebook of the internet," DNS takes the URL you type into your browser's address bar and turns it into a numeric IP address that your device uses to find the webpage and load it up.
DNS is often thought of as the translation of human inputs (like URLs and domain names) into computer-friendly numeric codes.
Your default DNS provider is usually your ISP (Internet Service Provider). However, connect to a VPN, and your DNS will be provided by the VPN service provider. Surfshark launched its own public DNS service in April 2025.
Double VPN
Double VPN is a feature where your VPN traffic is sent through two VPN servers rather than one. This doubles security but means a loss in speed.
Not every provider offers Double VPN. NordVPN's Double VPN and Proton VPN's Secure Core are two examples. Surfshark also offers Dynamic MultiHop.
Eavesdropping Attack
A form of hacking that targets information as it is transmitted over unencrypted wireless internet connections. Often, these are free Wi-Fi hotspots you find in cafes and airports, and they typically don't require a password.
Eavesdropping attacks are sometimes called "sniffing attacks" or "spoofing attacks".
Encryption
Encryption encodes data, turning it into a random string of unintelligible characters, and prevents it from being read by snoopers and hackers.
An algorithm encrypts your data, and a cipher is used to subsequently decrypt it once it reaches its destination.
The most secure VPNs use a variety of encryption protocols to protect your data. AES (Advanced Encryption Standard) is the most widely used but post-quantum encryption is the new industry standard.
Encryption Key
Encryption keys are made up of random sets of information used to encrypt and decrypt data. You'll often see keys described alongside their size – e.g. 1024 and 2048. The bigger the number, the more variations there are in the encryption process, and the harder it is for attacks to crack the code.
Firewall
Firewalls monitor traffic connecting to the internet and can block unwanted traffic. They can be adopted by government's restricting the internet and imposing censorship – the "Great Firewall of China" being an example.
The ease of bypassing a firewall depends on its level of sophistication. Most obfuscating VPNs can bypass more firewalls. Although those imposed by Russia and China are harder to navigate.
Five Eyes Alliance
An intelligence network made up of the UK, the US, Canada, Australia, and New Zealand. The existence of the Five Eyes Alliance (and the extent of its data harvesting) was unveiled in 2013, by Edward Snowden, and now we recommend sticking to VPN providers who are headquartered outside of the countries listed above.
Extended alliances exist, too – including the Nine Eyes and Fourteen Eyes.
Geo-blocking
Geo-blocks prevent you from accessing web content – and can limit certain sites, services, and apps to specific countries.
The best streaming VPNs can help you get around geo-blocking measures and unlock international Netflix libraries. So, if you're on vacation, traveling for work, or simply interested in what other regions have to offer, a VPN is your best bet.
IP address
Any internet-connecting device has an Internet Protocol (IP) address and it makes sure that the correct data gets routed to the correct computer. A unique string of numbers is used to identify your device. Its information includes approximate location and your ISP.
Connecting to a VPN changes your IP address, spoofing your location and protecting your privacy.

IPv4
IPv4 is what we call the 4th version of the internet's standard protocol, Internet Protocol (IP). IPv4 assigns a unique IP address to every internet-enabled device, allowing them to communicate and connect to the web.
We're rapidly running out of usable IPv4 addresses, however. The protocol is so popular, and there are so many devices connected to the internet, that it became necessary to develop a new standard protocol – IPv6.
IPv6
Internet Protocol version 6 (IPv6 for short) is the newer version of IPv4. Like its predecessor, it defines how IP addresses are dished out to our gadgets and computers, and how they communicate.
IPv6 isn’t as widespread as IPv4, but it's certainly better. It's much quicker, simpler, and has 1,028 times more IP addresses than IPv4. That's good news, too, because we're quickly running out of IPv4 addresses.
IP leak
IP leaks occur when your IP address is visible – even though you're using a VPN.
If you're using your original DNS server, and not the one provided by your VPN, your ISP (internet service provider) can see everything you get up to online. Naturally, this is the last thing you want when using a VPN.
You can visit IPLeak.net, IPLeak.org, or BrowserLeaks.com to check for DNS leaks. Alternatively, lots of VPN providers have their own DNS leak tools – including ExpressVPN's excellent page.
Jurisdiction
The country where a VPN provider's headquarters are located. A VPN provider has to stick to the laws of the jurisdiction – which can vary from country to country.
Generally, we'd advise you to use a VPN headquartered in a country that isn't a part of the Five Eyes alliance – and one without invasive data retention laws.
Key Exchange
A process where two parties securely swap cryptographic keys that can be used to share encrypted data. Anyone who isn't an involved party will be unable to get their hands on a key (or a copy of the key) and, as a result, unable to decrypt the shared data.
Diffie-Hellman is a popular method of key exchange, along with Internet Key Exchange (which you might recognize from the IKEv2 protocol).
Kill switch
One of a VPN's most must-have features. A kill switch cuts your connection to the internet if your VPN connection drops out, and ensures that you don't suffer an IP leak.
Without a kill switch, your identifiable information could become visible to snoopers, and your data could be left unprotected.

Latency
How long it takes for data to journey across a network from its source (usually your device) to its ultimate destination (like a website).
When you connect to a VPN, data leaves the source and is routed through the VPN server before it makes it to its destination. This is an extra step in the process – but an important one, as this is where your data is encrypted – that can increase latency.
However, using a VPN can also improve latency. You can avoid ISP throttling, access quieter servers, and find more direct traffic routes. The best gaming VPNs can help improve your latency when online gaming.

Leak
Whenever a VPN fails to keep your personal information secure and out of the hands of onlookers (including your internet service provider, the website you're on, other network users, or cybercriminals) it's known as a leak.
Common leaks include: IPv4, IPv6, DNS, and WebRTC.
Lightway
A proprietary protocol created by ExpressVPN – based on WireGuard.
Lightway is quicker, connects faster, and has been rebuilt in Rust for additional performance and security improvements.
Lightway is open-source so you can inspect the code yourself. Lightway Turbo is an even faster version of Lightway that is exclusive to Windows. In our testing, Lightway Turbo recorded speeds of a whopping 1,617 Mbps – making ExpressVPN one of the fastest VPNs.
ExpressVPN: the best VPN for beginners
With its simple and easy-to-use apps, ExpressVPN is an ideal VPN for beginners. Its Lightway protocol is super fast and all your data will be protected by post-quantum encryption. Between 10 and 14 devices can be protected, depending on your plan.
ExpressVPN has overhauled its subscription model, with three tiers of plan now available. ExpressVPN Basic starts at $3.49 per month ($97.72 up front pre-tax). You'll get 4 extra months of protection for free and a 30-day money-back guarantee.
Logging
Generally, VPN logs are split into two categories: connection logs and usage logs. Connection logs are usually anonymized, and contain information about which server you're using, how long you've been connected to it, and the device you're using the VPN with. Connection logs help VPN services maintain their server networks and troubleshoot issues as they crop up.
Usage logs, on the other hand, are far more insidious. They can reveal your IP address, the websites and services you've visited, and your download history, which is a massive violation of your digital privacy.
The most private VPNs don't store any logs and have audited no-logs policies. We don't recommend any VPN known to keep usage logs.
Man-in-the-middle attacks
A cyberattack that allows a snooper to listen in to conversations between a user device and the sites they visit – and record login details, financial information, and even credit card numbers.
Armed with this information, the snooper can go on to impersonate the victim or empty their bank account.
No-Logs Policy
A no-logs policy states that a VPN won't keep a record of a user's browsing history, download history, real IP address, DNS queries, or bandwidth usage. Today's top VPNs submit to independent audits of their no-log policies in the name of transparency.
Even with a no-logs policy, VPNs may collect some personal or usage data. The key point is a reputable provider won't log, share, or sell it.
A no-logs policy is different to a zero-logs policy, and we'll explain the latter further down.
NordWhisper
NordWhisper is NordVPN's unique obfuscating VPN protocol. It was first launched in 2025 and navigates internet restrictions by mimicking regular internet traffic.

Obfuscation
Obfuscation makes encrypted VPN traffic look just like ordinary web traffic – so the websites you visit can't tell that you’re using a VPN at all. Obfuscation can help you access streaming platforms and blocked services, and bypass censorship and VPN bans imposed by certain websites or oppressive governments.
OpenVPN
A massively popular VPN protocol. OpenVPN is secure, configurable, and open-source – which means you could take a look at its source code (and pick out potential bugs or weaknesses) if you wanted.
OpenVPN's security and versatility have made the protocol a mainstay in the VPN world, but the WireGuard protocol (and proprietary protocols, like Lightway and NordLynx) are quicker.
Open-Source
Certain VPN providers make their code and apps open-source. This means anyone can inspect it and confirm for themselves the VPN is doing what it says it does.
Proton VPN, ExpressVPN, Private Internet Access, and Mullvad VPN are all open-source.
Perfect Forward Secrecy
A method of encryption that frequently swaps the encryption keys that a VPN uses to encrypt and decrypt data. The constant switch-ups ensure that only a small percentage of data is exposed if a bad actor hacks a key.
Ping
A measurement of latency; how long it takes for data to travel along a network, from one device to the next, and come back with a response.
When you connect to a VPN, your traffic is routed through a VPN server after it leaves your device and before it reaches its ultimate destination. This extra step can result in increased ping.
Post-Quantum Encryption
Post-quantum encryption (PQE) is the new industry standard of encryption and is designed to withstand attacks from quantum computers. It's still in its infancy and there is debate over whether VPNs should adopt it right away.
ExpressVPN, NordVPN, and Mullvad VPN are examples of providers who have implemented PQE. Surfshark, Proton VPN, and Private Internet Access haven't yet.
Proprietary Protocol
A proprietary protocol is a unique VPN protocol developed by a VPN provider. These protocols are often, but not always, inspired by or built from WireGuard.
Stealth (Proton VPN), NordLynx & NordWhisper (NordVPN), and Lightway (ExpressVPN) are all examples of proprietary protocols.

Protocol
Rules that dictate how data is transmitted between your device and the VPN's server, and how the VPN creates a secure connection between the two.
The protocols you'll see most often include OpenVPN, WireGuard, and IKEv2. But many VPN providers also have their own unique protocols.
Proxy
Proxies can help bypass geo-restrictions that block access to region-specific services or websites. By masking your original IP address and replacing it with one of the proxy's IP addresses, you can avoid restrictions.
However, proxies aren't usually encrypted, so they're often thought of as unblocking tools rather than a full privacy-enhancing security suite (like a VPN).
Public Wi-Fi
The free wireless connections offered by hotels, airports, cafes, and other public places. Anyone can connect to these public Wi-Fi hotspots – you won't need a password.
However, because of this (and because public Wi-Fi hotspots are unencrypted), they're a notorious hotspot for hackers. Users are at risk unless they have a VPN to encrypt data transmitted to and from their devices.
P2P
Peer-to-peer (P2P) networks allow users to connect without the need of a third-party. It operates a decentralized structure and is often used to share files or torrent.
Devices connect to each other and both act as a server and client, with no central server involved. Private Internet Access, Proton VPN, and NordVPN all have dedicated P2P servers but many more VPNs support it.
Q-Day
Q-Day is the name given to point when quantum computers are able to crack all existing encryption methods.
It's not a specific day, more a point of no return, but is expected to take place sometime between 2030 and 2050 – although some experts believe it will happen sooner.
Post-quantum encryption is specifically designed to defend against quantum computer attacks and we're still a way off widespread quantum computer availability – but preparation is key.
Split tunneling
A feature offered by some VPNs that allows you to send some of your traffic through the VPN, and some not.
If an app isn't working properly with your VPN (a streaming service that blocks access if it detects that you're connected to a VPN server overseas, for example), you can set up split tunneling and direct app traffic through your original internet connection to avoid the problem in the future.
Stealth
Stealth is Proton VPN's unique protocol. It can bypass most firewalls and blocking methods, making it one of Proton VPN's dedicated anti-censorship features.
Stealth can also refer to Windscribe's obfuscating protocol of the same name. Windscribe's version is an OpenVPN tunnel masked as regular internet traffic.

strongSwan
An open-source VPN app. You can use it on Windows, Mac, Android, and iOS, and it's compatible with most VPNs on the market.
Although strongSwan isn't packed with features, you can use it in place of a VPN provider's app if you're having trouble with it.
Threat Protection
Threat protection helps protect your device against malware and scams. It may warn you about suspicious links or monitor the web for data leaks.
Not every VPN provider includes threat protection as standard and its effectiveness varies. NordVPN's Threat Protection Pro is our favorite but others include Proton VPN's NetShield and ExpressVPN's Advanced Protection.
Throttling
Internet throttling is a mode of digital traffic management that reduces connection speeds. Your internet service provider (ISP) might decide to throttle your connection if you're in the middle of a data-intensive activity (think HD streaming, online gaming, torrenting) to alleviate bandwidth demand.
A VPN prevents throttling by hiding your activity from your ISP – meaning it won't know what you're up to and won't know to throttle you.
Tor
The Tor Network (also known as The Onion Router) is an open-source project that enables secure and anonymous online communication. Tor achieves this by encrypting data multiple times and passing it through randomly selected volunteer-run services (or "nodes").
Although Tor and VPNs aren't the same, they can both mask your IP address and boost your digital privacy – and some VPNs are compatible with Tor. NordVPN offers an Onion over VPN feature which lets users access the Tor Network.
Tunnel
The encrypted connection that links your device and another network. A VPN, for example, creates a secure tunnel between your device and the internet.
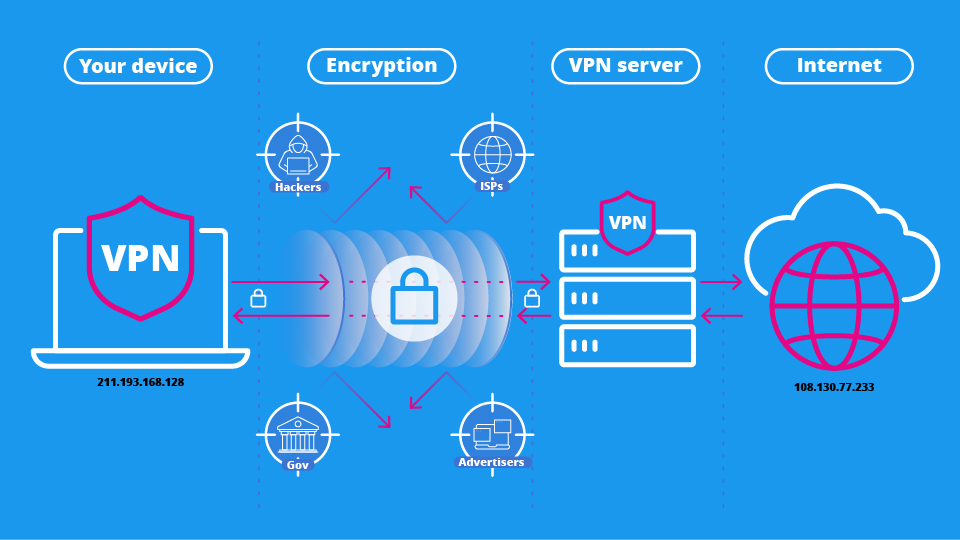
VPN Client
The VPN client is the device owned (or used) by you, the VPN user. This device connects to the VPN server via the encrypted tunnel and can be a PC, laptop, smartphone, tablet, games console, TV, or even a router.
VPN Server
Servers run and maintained by the VPN provider that connect to the internet. All VPN servers are encrypted and many offer speciality servers which provide extra security but often at the expense of speed.
Leading VPNs have thousands of servers worldwide. However, server count doesn't always matter and quality is better than quantity.
VPN Service
A service or company that provides VPN servers. These servers are scattered around the world and enable VPN users to connect to the internet via the secure encrypted tunnel.
Warrant canary
A document that subtly informs VPN users that a VPN provider has been ordered to reveal identifiable information about its users. Warrant canaries let users know that a VPN provider hasn't been lumped with a warrant or subpoena, up to a certain date. So, if the warrant canary is wildly out of date or removed altogether, VPN users can typically assume that the provider has come under investigation.
WebRTC
Created by Google, Web Real-Time Communications (WebRTC) is an open-source technology allowing web browsers (and other apps) to support audio, video, and other communications.
However, WebRTC can inform websites about the original IP address of a user, even if they have a VPN, which is known as a WebRTC leak.
White box
An in-depth method of software testing where auditors have access to apps and their source code.
White box VPN audits result in more detailed findings than black box tests, where auditors only have access to the same information as end users – meaning they can test apps, but can’t comb through the source code.
WireGuard
Upon its release, WireGuard was seen as the next generation of VPN protocol – and the successor to OpenVPN in terms of popularity. WireGuard is easy to set up by design, contains fewer lines of code than OpenVPN, and often results in improved speed – making it a favorite of avid streamers and gamers.
Zero-Logs Policy
A zero-logs policy is when a VPN provider collects little to nothing about you or your browsing activity.
Sign-up information such as an email address may not be needed and you might also have the option to pay in cash or cryptocurrency – Mullvad VPN does both of these.
New VPN on the block Obscura VPN claims to be "private by design" and would be classed as a zero-logs VPN. Its founder Carl Dong said the only data stored is your account expiry date and number of registered devices. This is yet to be confirmed via an independent audit but Obscura's source code is available to view.
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.

River is a Tech Software Editor and VPN expert, helping take care of cybersecurity content on Tom's Guide, ranging from reviews, buying guides, and must-have VPN deals. River's expertise in the cybersecurity field opened their eyes to the startling amount of online snooping we accept into our daily lives. Now, River is committed to fighting for your right to digital privacy by shining a light on its biggest threats – and helping readers safeguard their data with the help of a VPN. Surfshark is River's favorite VPN, and they use it every day to keep their most sensitive details out of the hands of third-party trackers.
- George PhillipsStaff Writer
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits








