Computing
Explore Computing
Latest about Computing

Obscura VPN passes first independent audit
By Aleksandar Stevanović published
Obscura VPN has cleared its first independent security audit, with no major flaws found in its macOS app or core protocol

RAM price crisis LIVE — latest updates on global memory shortage, expert advice and more
By Darragh Murphy last updated
Here's everything you need to know about the ongoing RAM price crisis, along with the latest updates and our expert advice on current prices on phones, tablets, laptops and more.

Last chance before the holidays! 9 Kindle deals I'd shop in Amazon's sale
By Millie Davis-Williams last updated
Amazon is slashing prices on Kindle e-readers, so now's the time to grab a new slate for the perfect holiday gift.

'Comply with the law' – UK Government takes aim at VPNs during Online Safety Act debate
By George Phillips published
A debate over the UK's Online Safety Act has seen VPNs come under fire. MPs have called for VPNs to be examined further, implement age checks, and collect user data.

Best MacBook deals in December 2025
By Louis Ramirez last updated
Cheap MacBook sales are easy to find if you know where to look. Here are today's best MacBook deals.

Massive Apple leak reveals over 30 upcoming products — iPhone Fold, cheap MacBook, smart glasses, AirTag 2 and more
By Jason England published
An unreleased build of iOS 26 has leaked over 30 new Apple products that are being worked on — including AirTag 2, iPhone Fold and Apple smart glasses.

Best gaming laptops that I personally recommend after years of testing and thousands of hours of play
By Alex Wawro last updated
Our best gaming laptops list includes great budget options as well as huge, premium powerhouses. These are the best of the best, based on hours of testing and hands-on reviews.
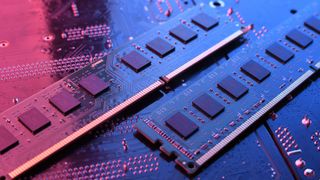
Samsung reportedly raises DDR5 RAM prices by 100% with 'no stock' left
By Darragh Murphy published
Samsung has reportedly raised the contract price of its DDR5 RAM by 100%, with the cause expected to be "no stock" left, and it will lead to the cost of devices seeing a sharp rise in 2026.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!


