Explore Internet
Latest about Internet

VPN Deal of the Week: The new F1 season is here – and our exclusive IPVanish deal lets you watch from anywhere
By Mo Harber-Lamond published
This week's VPN Deal of the Week comes from IPVanish. It's great value, and Tom's Guide

The best free VPN in 2026
By Mo Harber-Lamond last updated
Most free VPNs are useless – but there are a few that are worth considering. This is our tested and ranked guide to the only free VPN services we recommend.

PureVPN's huge server upgrade adds 40+ new locations worldwide
By George Phillips published
PureVPN has added a whopping 40+ new locations to its server network. The upgrade is in response to growing online restrictions and aims to improve VPN performance

AOC and NordVPN clash with lawmakers over online age verification rules
By Aleksandar Stevanović published
Alexandria Ocasio-Cortez and NordVPN have criticized new age verification proposals, warning they could lead to widespread online surveillance and technical problems.

The best VPN in 2026: our top 5 picks
By Mo Harber-Lamond last updated
We've tested and reviewed dozens of VPN. On this page we've ranked the five best VPNs we've used, and delve into the details of why they're so good.
How to get a free trial to Surfshark VPN
By Luke Edwards published
Sponsored by Surfshark
You can try Surfshark — one of the planet's fastest, most versatile VPNs — without paying a single dollar for the privilege. Here's how.
Big Norton VPN update addresses a key problem for streaming fans
By George Phillips published
Norton VPN launches two significant platform updates. Fire TV is now supported, while WireGuard has come to Mac. Here's what you need to know.
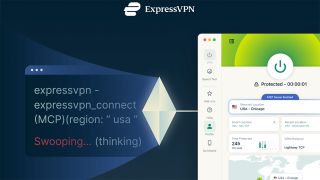
ExpressVPN launches an AI-powered MCP Server in an industry first
By Aleksandar Stevanović published
ExpressVPN has launched a beta MCP server that lets AI tools securely read VPN status and change connection settings from inside development workflows.
AdGuard is the latest VPN to bring ad blocking and VPN protection to Meta Quest VR browsers – and here's how to get it
By Aleksandar Stevanović published
AdGuard has launched new ad-blocking and VPN browser extensions for Meta Quest, bringing cleaner browsing and privacy protection to virtual reality headsets.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
 Club Benefits
Club Benefits











