Internet
Latest about Internet
-
-

6 million hit in major airline data breach — everything you need to know
By Amber Bouman Published
-
 Updated
UpdatedThe best VPN in 2025: our top 5 picks
By Mo Harber-Lamond Last updated
-

Experts warn Q-Day may arrive in less than 2 years – but how vulnerable is our data?
By George Phillips Published
-
 VPN
VPNBest iPhone VPN for iOS in 2025
By Olivia Powell Last updated
-

Nord Security’s 2024 Impact Report shines a light on the company’s carbon footprint
By Michael Simon Published
-

X was down for thousands — live updates on outage
By Tom Pritchard Last updated
-
This VPN will pay for your next Amazon order
By Mo Harber-Lamond Published
-
Explore Internet
Browsers
-
-
Move over, OpenAI! Opera Neon is a new AI browser that can surf the web and even build games while you sleep
By Jason England Published
-

Google will finally stop this 20-year Chrome bug from leaking your browsing history to other websites — here’s how
By Anthony Spadafora Published
-

Your iPhone has a custom voice command feature — here's how to use it
By David Crookes Published
-

You can change your iPhone's default browser — here's how
By David Crookes Published
-

How to stop your personal data from appearing in Google searches
By Kaycee Hill Last updated
-

I just tested the world’s first mindful browser — it’s calmly convinced me to ditch Google Chrome
By Jason England Published
-

Google Chrome just got three new modes — and it's a game changer for performance
By Josh Render Last updated
-

Google Calendar just got the dark mode we’ve been waiting for — here’s how to activate it
By Scott Younker Published
-

This new Google Chrome upgrade made me say 'whoa' out loud — and it's a game changer
By Alex Wawro Last updated
-
Cloud Storage
-
-

One of our favorite cloud storage services is taking 70% for 4th of July
By Louis Ramirez Published
-

Best cloud storage in 2025
By Richard Sutherland Last updated
-

The best cloud storage for photos and pictures in 2025
By Richard Sutherland Last updated
-

Google Photos vs. iCloud: Which should you use for your photos?
By Michael Graw Published
-

Google Photos vs. Amazon Photos: Which should you pick?
By Michael Graw Published
-

Dropbox vs. Google Drive: Which is right for you?
By Michael Graw Published
-

Dropbox vs. Box: Which is best for you?
By Michael Graw Published
-

Dropbox was down — live updates on short outage
By Scott Younker Last updated
-
 Review
ReviewiCloud review: Seamless cloud storage for Apple
By Nikshep Myle Last updated
-
-
-

Gmail’s new ‘Manage Subscriptions’ feature might help me finally get my inbox under control
By Tom Pritchard Published
-
Exclusive: Notion Mail boss on shaking up email, building apps with 'Lego' and new platforms
By Lloyd Coombes Published
-

I just tested Notion Mail to see if it can shake up my inbox — here's how it went
By Lloyd Coombes Published
-

Need a hand? Gmail’s ‘Help me write’ comes to web users — everything you need to know
By Josh Render Published
-

Microsoft Outlook went down — what to do if it's not working for you
By Anthony Spadafora Last updated
-

How to create a new Gmail account
By Alan Martin Last updated
-

Google is deleting inactive Gmail accounts — here's how to save yours
By Kaycee Hill Last updated
-

Yahoo Mail is the latest service to get in on the AI craze
By Scott Younker Published
-

One inbox to rule them all — how to transfer emails between Gmail accounts
By Kaycee Hill Published
-
Instant Messengers
-
-

The best encrypted messaging apps in 2025
By Amber Bouman Last updated
-

The best WhatsApp alternatives in 2025
By Tom Pritchard Last updated
-

8 TikTok alternatives — where to go if the app gets banned
By Kaycee Hill Last updated
-

New WhatsApp green screen bug is making the app unusable
By Alyse Stanley Published
-

Telegram: What it is and how to use it
By Anthony Spadafora Last updated
-

WhatsApp starts rolling out Events planning feature for group chants — here’s how it works
By Scott Younker Published
-

WhatsApp looking to add AirDrop-esque feature to iPhones — what we know
By Scott Younker Published
-

WhatsApp drops surprise design update — it's rounder and darker now
By Scott Younker Published
-

How to rejoin a group chat on WhatsApp
By Emma Street Published
-
Online Security
-
-

6 million hit in major airline data breach — everything you need to know
By Amber Bouman Published
-

Over half a million people impacted by major data breach — full names, SSNs, financial data and more exposed
By Anthony Spadafora Published
-

FBI warns scammers are posing as fraud investigators to steal sensitive healthcare info — what you need to know
By Anthony Spadafora Published
-

Xfinity just added Wi-Fi-powered motion tracking to its routers — here's why it could be a privacy nightmare
By Amber Bouman Published
-

61 million Verizon records reportedly for sale — including date of birth, tax ID and phone numbers
By Josh Render Published
-

Popular TikTok video editor used in phishing scam – here’s how to stay safe
By Amber Bouman Published
-

Major security flaw exposes Sony, JBL and Bose headphones to hijacking threat — how to stay safe
By Darragh Murphy Published
-

These 5 macOS settings are a security risk and you should turn them off now
By Amber Bouman Published
-

We asked cybersecurity experts to build a privacy toolbox for $10 per month – here's what they came up with, and more
By George Phillips Published
-
Search Engines
-
-

Bring back Google’s old-school search results with this one simple hack
By Kaycee Hill Last updated
-

Google is refusing to comply with upcoming EU fact-checking laws — what we know
By Tom Pritchard Published
-

Microsoft accused of making Bing look just like Google search — and Google fires back
By Dave LeClair Published
-

You can limit your Google searches to a single website — here's how
By David Crookes Published
-

DOJ will reportedly force Google to sell Chrome — what you need to know
By Scott Younker Last updated
-
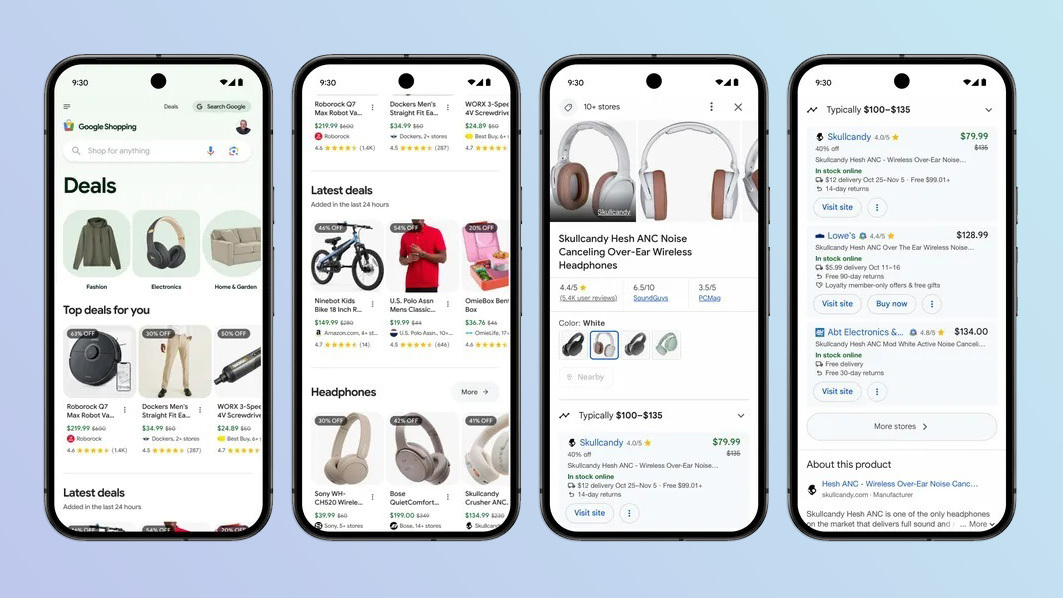
Google gives Google Shopping an AI makeover — here's what's new
By Scott Younker Published
-

Google Search has a new trick up its sleeve — and it might save you from fake AI images
By Scott Younker Published
-

Wayback Machine links are now are part of Google Search — here's what's new
By Scott Younker Published
-

Yelp files antitrust suit against Google — what's next
By Scott Younker Last updated
-
Social Media
-
-

X was down for thousands — live updates on outage
By Tom Pritchard Last updated
-

Trump just gave TikTok an extension on ban — here's what we know
By Scott Younker Published
-

I'm glad Threads is adding features to protect us from spoilers — but I wish it wasn't necessary
By Tom Pritchard Published
-

Reddit was down — live updates on latest outage
By Scott Younker Last updated
-

X (Twitter) was down — what happened during major outage that stretched into weekend
By Scott Younker Last updated
-

TikTok is giving teenage users a bed time — no more scrolling after 10pm
By Tom Pritchard Published
-

TikTok ban delayed again — live updates on deadline extension and what's happening right now
By Jeff Parsons Last updated
-

X was down again — live updates on major outage
By Scott Younker Last updated
-

Instagram was down — live updates on the quick outage
By Dave LeClair Last updated
-
VPNs
-
-
 Updated
UpdatedThe best VPN in 2025: our top 5 picks
By Mo Harber-Lamond Last updated
-

Experts warn Q-Day may arrive in less than 2 years – but how vulnerable is our data?
By George Phillips Published
-
 VPN
VPNBest iPhone VPN for iOS in 2025
By Olivia Powell Last updated
-

Nord Security’s 2024 Impact Report shines a light on the company’s carbon footprint
By Michael Simon Published
-

This VPN will pay for your next Amazon order
By Mo Harber-Lamond Published
-

Best VPN deals in July 2025
By Mo Harber-Lamond Last updated
-
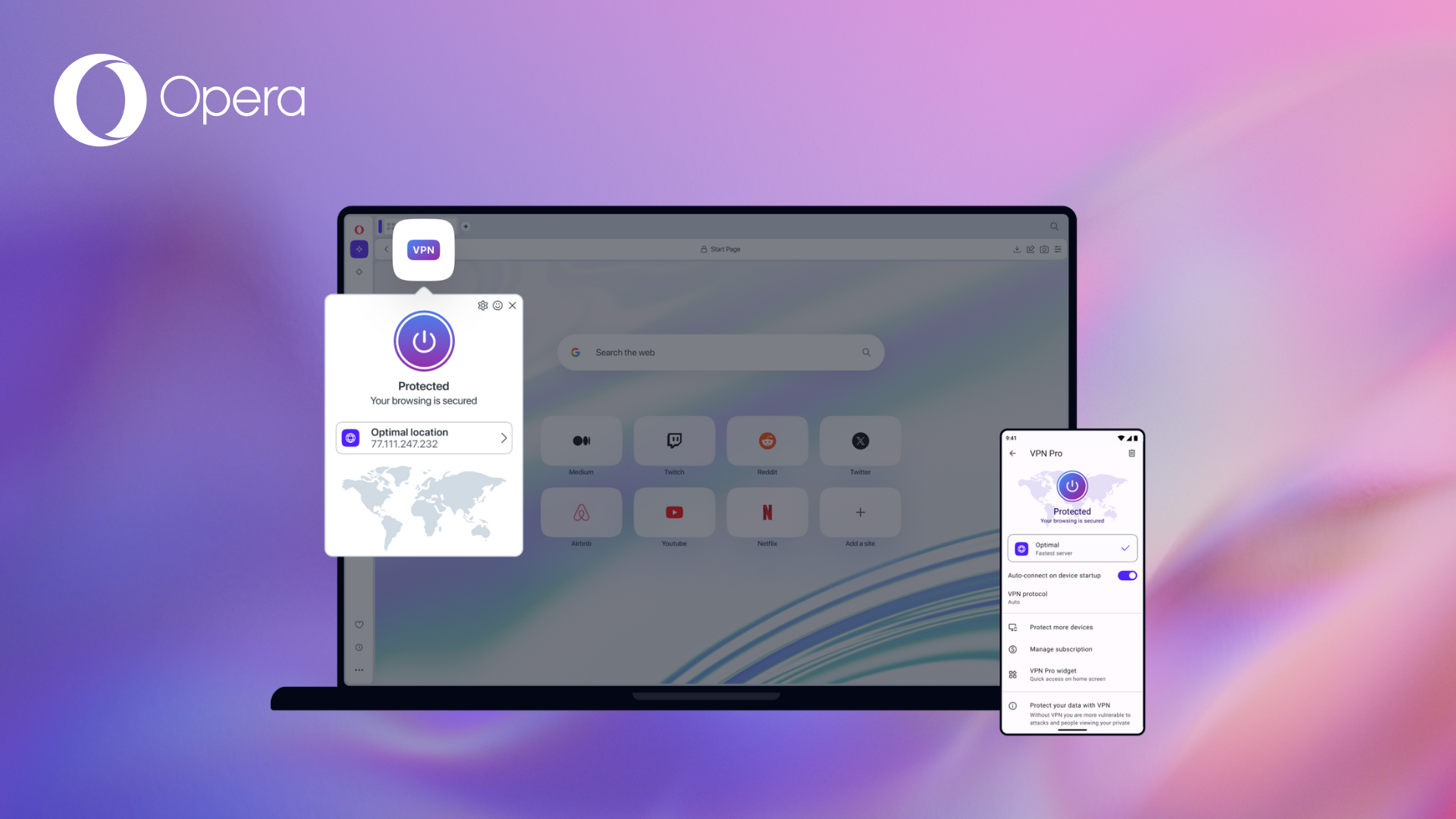
Opera VPN Pro update adds new locations and ExpressVPN’s Lightway protocol
By Michael Simon Published
-

NordVPN price and plans – costs and deals in 2025
By Mo Harber-Lamond Last updated
-

Most NordVPN users are making the same mistake – don't be one of them
By George Phillips Published
-
Video Conferencing
-
-

HP unveils its 65-inch Google Beam display — here's how much the 3D video conference setup costs
By Philip Michaels Published
-

Google Beam brings 3D to video chat — here's how it works
By Philip Michaels Published
-

Skype is shutting down after 22 years — here's the 7 best alternatives
By Scott Younker Published
-

I used Skype for years, and Teams is a poor replacement for the video calling service that started it all
By Anthony Spadafora Published
-

Best video chat apps in 2025
By Tom Pritchard Last updated
-
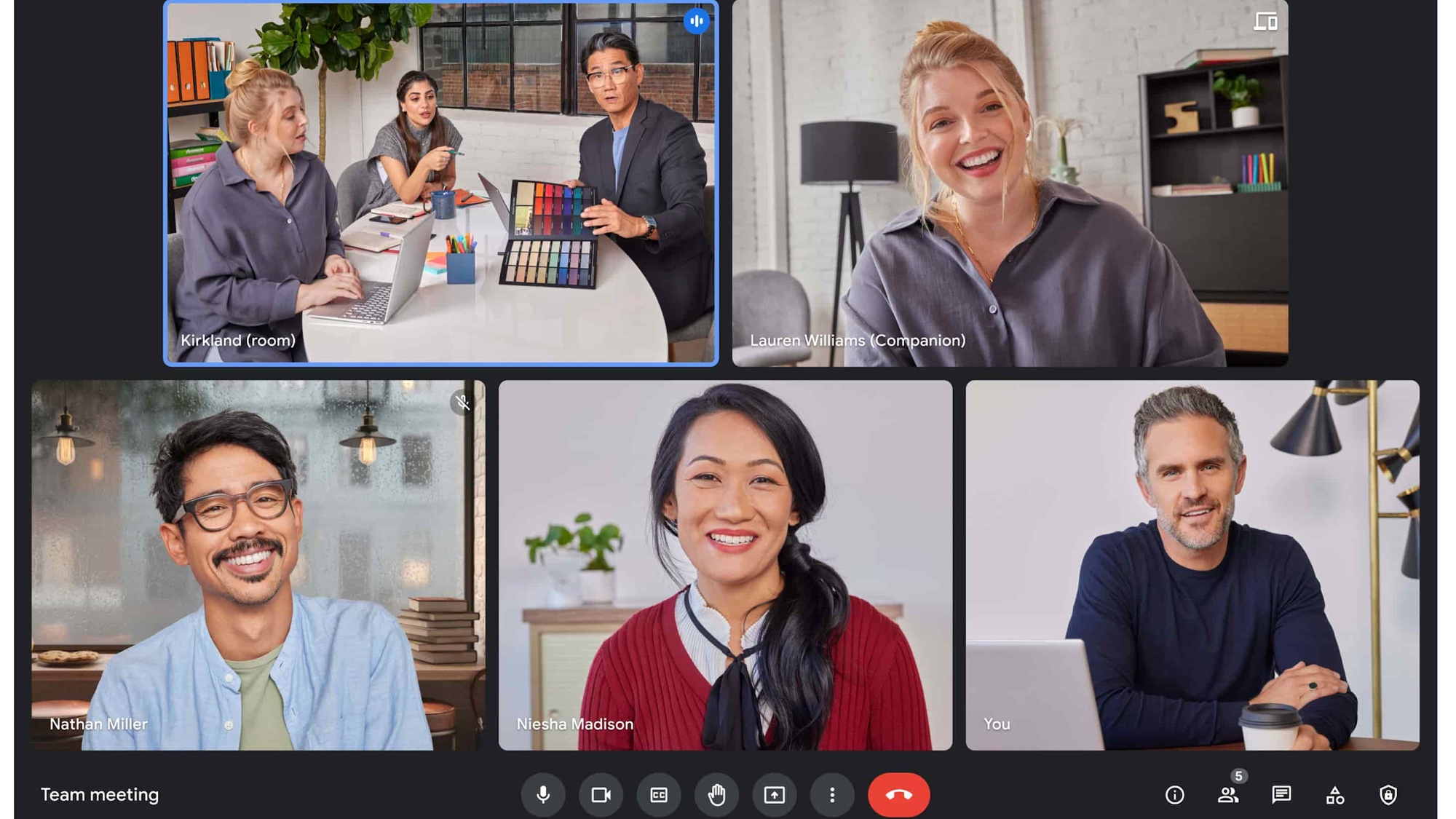
Google Meet is getting a very handy automatic picture-in-picture mode — what you need to know
By Tom Pritchard Published
-

How to stop Microsoft Teams from opening on startup
By Tony Polanco Last updated
-

I just tried Google’s 3D video conferencing tool launching next year — here’s what Project Starline is like
By Philip Michaels Published
-

Best Zoom alternatives for video calling
By Anthony Spadafora Last updated
-
Website Builders & Hosting
-
-

The best free web hosting in 2025
By Richard Sutherland Last updated
-

The best website builders in 2025
By Richard Sutherland Last updated
-

The best web hosting services in 2025
By Richard Sutherland Last updated
-

The best Windows hosting services in 2025
By Richard Sutherland Last updated
-
 Review
ReviewBluehost web hosting review
By Richard Sutherland Last updated
-

How to host a website
By Jennifer Allen Published
-

How to make a website accessible
By Jennifer Allen Published
-

6 ways to get free website content legally and without fuss
By Michael Graw Published
-

9 tips for buying a web hosting service
By Michael Graw Published
-