Experts warn Q-Day may arrive in less than 2 years – but how vulnerable is our data?
Adopting post-quantum cryptography is more important than ever

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
Encryption is what protects your data from hackers and third-parties. It keeps your data hidden, safe, and decryption is required to read it.
All the best VPNs utilise AES-256 bit encryption or similar – but a growing number have adopted post-quantum encryption.
The eventual widespread adoption of quantum computers will make all standard encryption redundant. There is currently no danger of your data being compromised, but post-quantum encryption will be needed sooner rather than later.
However, there is a worry that the day current encryption standards can be broken – known as Q-Day – will arrive sooner than expected and we'll be left unprepared.
Post-quantum encryption is what can keep our data safe. It's being implemented but it's not yet the norm. Do we need to panic or is there still time to protect our data?
Current encryption standards
AES-256 has been the industry standard for a long time and secures large parts of the internet and various networks. It's used primarily with the OpenVPN protocol, and it's fast, effective at protecting large quantities of data, and can currently withstand all known attacks.
ChaCha20 is a similarly tough encryption cipher that's used by the modern WireGuard protocol. It's 256-bit, making is roughly as secure as AES-256, and is generally a little faster on everyday devices.
RSA encryption is another popular encryption type, and has been around since 1977. It's mainly used to encrypt the keys used in AES-256, and isn't tough enough to be used alone.
However, we know that technology never stands still. The invention, and inevitable widespread adoption, of quantum computers mean that these forms of encryption will become breakable and a new post-quantum encryption standard is needed.

In August 2024, after years of research, the US National Institute of Standards and Technology (NIST) released its first three finalized post-quantum encryption standards:
- Module-Lattice-Based Key-Encapsulation Mechanism Standard (ML-KEM)
- Module-Lattice-Based Digital Signature Standard (ML-DSA)
- Stateless Hash-Based Digital Signature Standard (SLH-DSA)
Q-Day is the name given to the point in time when quantum computers become widely available and are strong enough to break all existing encryption standards. It will represent a fundamental altering of the cryptography landscape.
This has been predicted to be anytime between 2030 and 2050. But recent quantum computing advances in China have led some experts to warn that Q-Day may arrive sooner than we think – and that some encryption standards will be broken in less than two years.
What has caused experts to worry?
News from China has left some experts hypothesizing that Q-Day may occur sooner than we think.
Using a quantum computer built by D-Wave, researchers at Shanghai University successfully cracked 22-bit RSA encryption.
RSA is tough but generally weaker than AES-256 bit encryption, and production-grade RSA is also much larger than 22-bit.
An 829-bit RSA key is currently the largest ever cracked with traditional, non-quantum methods – it took weeks of supercomputer power.
However, what is concerning experts is the speed at which researchers jumped from 19-bit to 22-bit RSA. So how long will it now take a quantum computer to crack an 829-bit RSA key or higher? How long until it AES-256 is under threat?
We might be overreacting, but we can't predict the rate at which quantum computing will develop and that's why it's important post-quantum cryptography is widely implemented.
David Carvalho, founder and CEO of decentralized post-quantum infrastructure Naoris Protocol commented on the news:
"The quantum threat is getting very real, very fast," he said, and described the speed of progression from 19-bit to 22-bit encryption cracking as "terrifying."
"It’s clearly only a matter of time until quantum computers can break highly secure algorithms, and that time is quickly running out."
"It’s complacent to assume we even have five years left before RSA encryption can be broken – it’s more like 24-36 months."
Carvalho said that other experts believe there's a one-in-seven chance of that occurring next year.
"To be safe, companies looking to protect encrypted data or digital assets must already transition to post-quantum cryptography this year – this is a recommendation from the National Institute of Standards and Technology (NIST) itself," he added.
"Every single day this is delayed, cybercriminals are getting closer to hacking every system that matters, and once hacked, what’s lost can never be recovered. It’s getting far too close for comfort now."
What does this mean for VPNs?
Back in April, we asked if post-quantum VPNs were necessary now or a premature move. Every VPN should be adopting post-quantum encryption, it's just a matter of when.
Combining post-quantum encryption with existing VPN protocols is tricky, and could be a major reason as to why we've not seen more VPNs implement it.
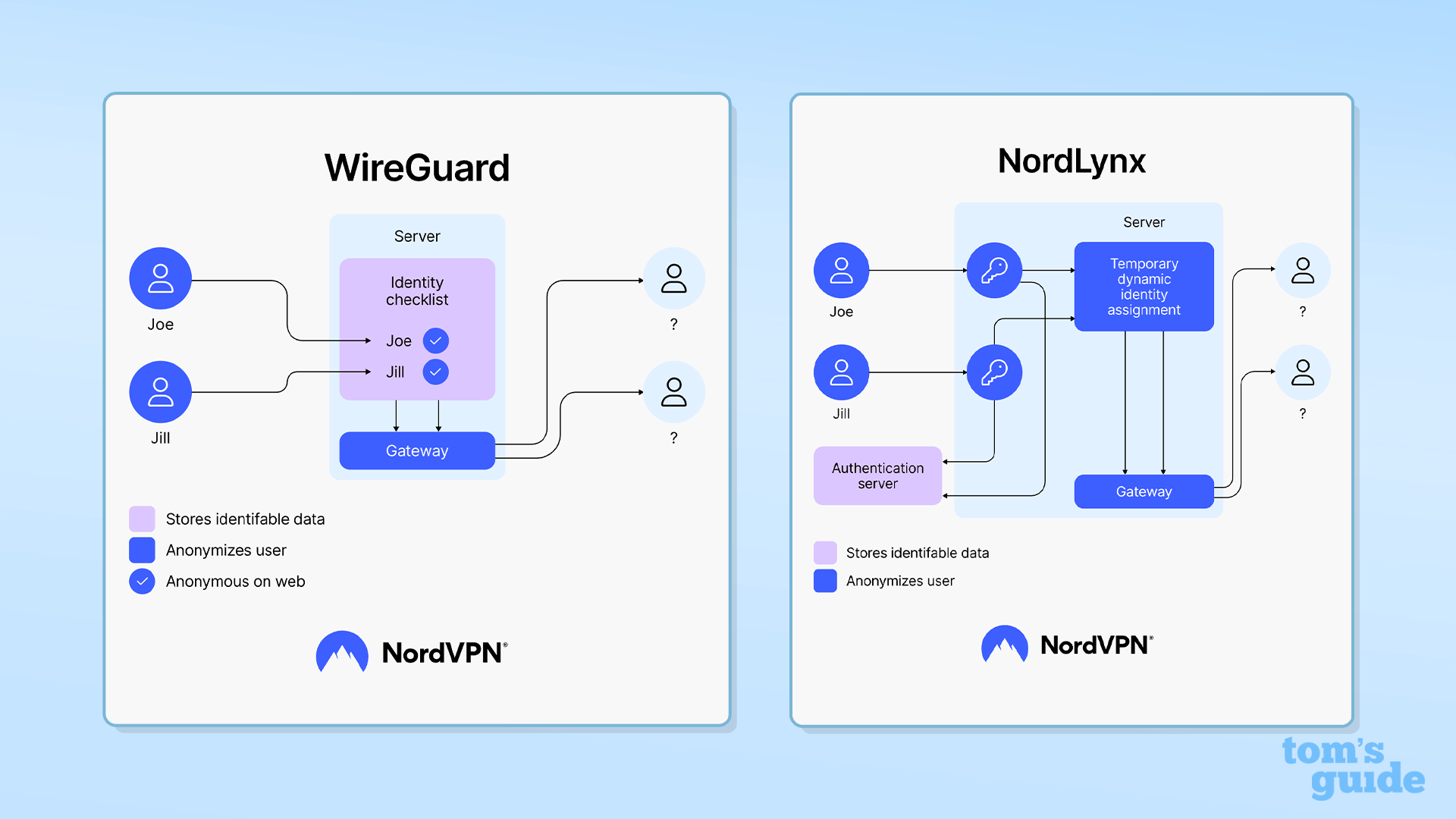
For example, WireGuard – the most popular VPN protocol – isn't fully quantum secure by default. WireGuard admits this limitation and suggests running a post-quantum "handshake" on top of WireGuard.
NordVPN and ExpressVPN both offer post-quantum encryption across the board. However, they both do this via their own unique, WireGuard-inspired protocols NordLynx and Lightway.
ExpressVPN was the first leading VPN to introduce post-quantum encryption across the board. At the time, Chief Engineering Officer Pete Membrey said "ML-KEM delivers stronger, future-proof encryption to keep you secure against the challenges of tomorrow."
NordVPN introduced full post-quantum support earlier this year. Marijus Briedis, CTO at NordVPN said: "By integrating PQE into our VPN infrastructure, we're taking a proactive step to ensure long-term confidentiality and resilience for our customers' data, both now and in a post-quantum future."
There is an argument that post-quantum encryption can't be fully tested yet, due to the lack of real-world quantum threats. Some VPNs, like Proton VPN and Surfshark, want to guarantee its effectiveness and ensure they can launch full post-quantum encryption support in one go.
Speaking to Tom's Guide in April, David Peterson, General Manager of Proton VPN said Proton VPN "still some way off" from implementing post-quantum encryption.
"Developing post-quantum encrypted technologies is a marathon, not a sprint, and we want to prepare properly so that these technologies only need to be deployed once across the whole Proton ecosystem," Peterson explained.
He added that "we need to battle-test these quantum-resistant algorithms, and to make sure they are standardised."
It remains to be seen how many VPNs will have adopted post-quantum encryption by the end of 2025.
Selected VPNs with post-quantum encryption support
- NordVPN
- ExpressVPN
- Mullvad
- Windscribe
- PureVPN
Selected VPNs yet to support post-quantum encryption
- Surfshark
- Proton VPN
- IPVanish
- Private Internet Access
(All of these providers are currently working towards implementing post-quantum encryption standards).
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.

George is a Staff Writer at Tom's Guide, covering VPN, privacy, and cybersecurity news. He is especially interested in digital rights and censorship, and its interplay with politics. Outside of work, George is passionate about music, Star Wars, and Karate.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits










