Fake Chrome extension ‘breaks’ your computer before it hits you with malware — how to stay safe
From ad blocker to new "CrashFix" campaign

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
You can never be too careful when downloading new software — whether that be an app or a browser extension — onto your computer. Case in point: when trying to download an ad blocker for their browser, a user ended up installing a fake extension that ‘broke’ their computer before offering up a malware-filled fix instead.
As reported by BleepingComputer, the browser extension in question is called NexShield. Despite being fake, it’s promoted as a privacy-first, high-performance and lightweight ad blocker. To make the extension appear legitimate, the cybercriminals who created it impersonated the original developer of uBlock Origin, Raymond Hill.
Unfortunately, besides not blocking ads, NexShield breaks your computer before offering to help you repair it to carry out a new ClickFix-style attack. Here’s everything you need to know about this new malicious extension, the malware it infects unsuspecting users with and how to stay safe from this highly successful new tactic being employed by hackers and other cybercriminals.
Breaking your browser to hack you with a fix
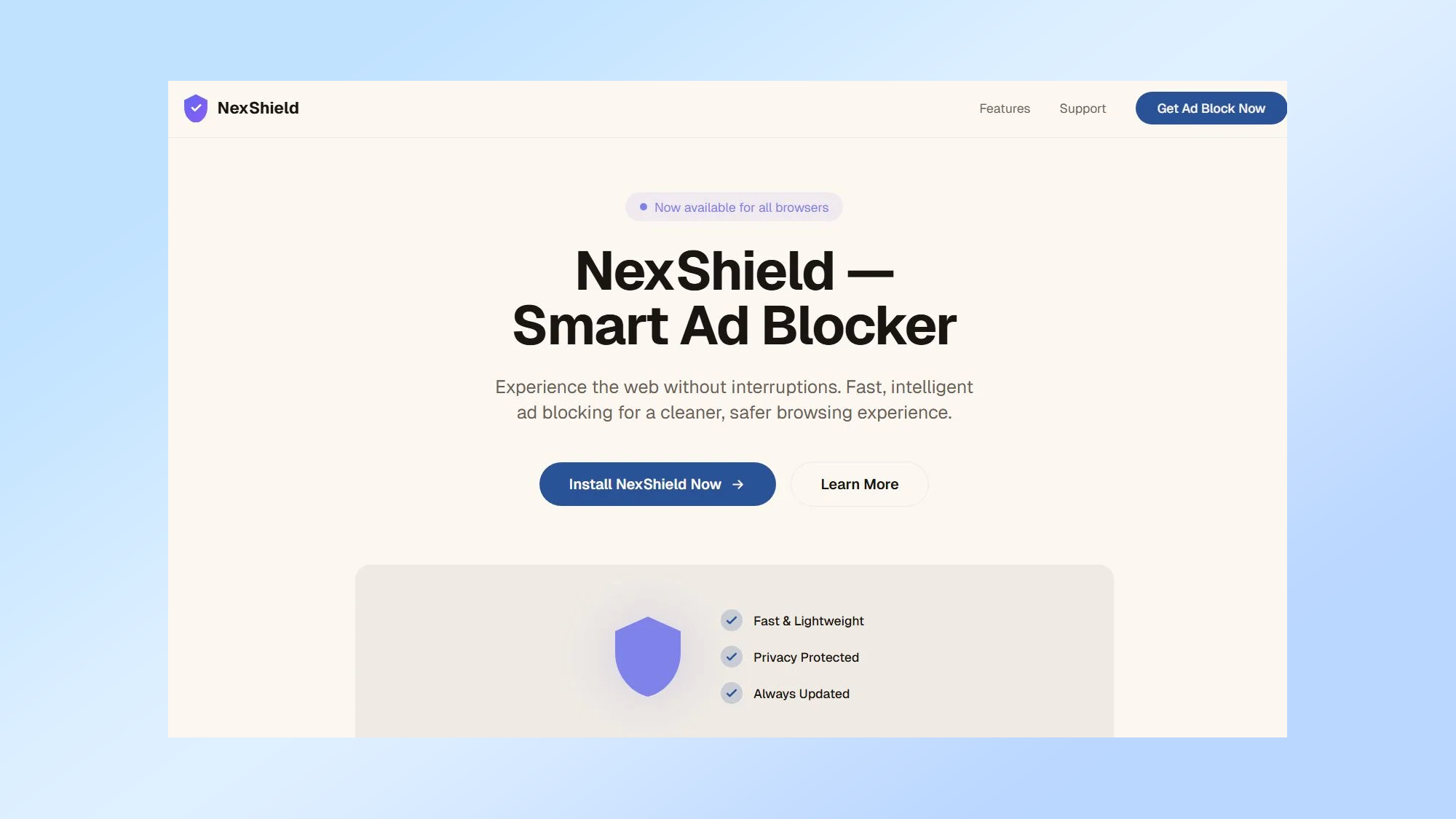
The cybercriminals behind this campaign have gone to great lengths to trick unsuspecting users. Not only have they created a fake extension, but they’ve also made a landing page for this so-called ad blocker and are running malicious ads to promote it.
According to a blog post from the cybersecurity firm Huntress, the NexShield extension can create a denial-of-service (DoS) condition in Google Chrome by making numerous ‘chrome.runtime’ port connections in an infinite loop, which exhausts a targeted computer’s memory. From your point of view as a Chrome or Edge user, you’d see frozen tabs, increased CPU and RAM usage and an unresponsive browser.
Once Chrome or Edge crashes and you restart your browser, NexShield shows a pop-up with a fake warning and suggests that it scans your PC to find the problem. Clicking on the “Run Scan” button opens a new window with yet another fake warning about security issues detected on your system. There are also instructions on how to fix the problem, but as you may have guessed, following them leads to a ClickFix-style attack security researchers at Huntress have dubbed CrashFix.
ClickFix attacks are very popular with hackers right now because, by copying and pasting malicious commands into a Windows command prompt, you’re actually doing the hard work for them. The command in question here triggers a hidden PowerShell script over a remote connection, which then downloads and executes a malicious script.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
What’s different from other CickFix attacks, though, is that the malicious activity doesn’t occur until an hour after the NexShield extension is installed. This helps the hackers behind this campaign avoid detection while confusing victims, since many won’t know why their computer is suddenly acting funny.
How to stay safe from fake extensions and malware

With this particular attack, the cybercriminals are targeting business users as opposed to normal home users. When someone on a corporate network downloads NexShield and applies the ‘fix’, the ModeloRAT malware is downloaded onto their computer. However, when an ordinary person does, they’re just met with a “TEST PAYLOAD!!!” message according to Huntress’ security researchers.
Fortunately, Google has since removed this fake NexShield extension from the Chrome Web Store. If you have it installed, though, you should remove it immediately.
Even though your computer didn’t get infected with malware from the NexShield extension, this should be a wake-up call. In the example shared by Huntress, the victim in question never should have clicked on the ad that popped up in their browser when looking for an ad blocker. Then, instead of following the extension’s instructions, they should have immediately deleted it and run a full scan of their computer using the best antivirus software.
Just like you and me, hackers can also buy ad space on Google and other search engines, which looks to be what happened here. This is why I highly recommend going right to the store itself — in this case, the Chrome Web Store — instead of clicking on advertisements in your browser, as they could be malicious ads posing as legitimate ones.
Likewise, when looking for new browser extensions, always check their rating, read reviews, and do your own external research before downloading anything. Our browsers handle everything from email to social media and even online banking, so you don’t want to risk having a malicious extension getting access to that data. Just like with the apps on your phone, you want to limit the number of browser extensions you have installed. Before downloading any new ones, first, always ask yourself if you actually need it.
From there, you should never follow instructions to fix a problem that involves copying commands and pasting them into a command prompt. This is a major red flag and doing so is exactly how countless ClickFix victims have infected their own machines with malware.
ClickFix and now CrashFix attacks have been highly effective for cybercriminals, and as such, I don’t think this tactic will disappear anytime soon. Instead, it’s up to you to do your research and be extra careful when installing new browser extensions.
Follow Tom's Guide on Google News and add us as a preferred source to get our up-to-date news, analysis, and reviews in your feeds.
More from Tom's Guide

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits










