New Spiderman phishing kit lets hackers instantly spoof banking sites to steal passwords and take over accounts — how to stay safe
Your friendly neighborhood hacker has a new tool to catch you in their web

Heading to a fake site and entering your username and password is one of the easiest ways for hackers to take over your online accounts. Creating fake sites that perfectly mimic legitimate ones used to take considerable time and effort but that’s no longer the case thanks to a new tool.
As reported by BleepingComputer, a new phishing kit called Spiderman is quickly gaining popularity among cybercriminals on the dark web. With it they can easily launch complex phishing campaigns designed to capture victims’ login credentials, two-factor authentication (2FA) codes, credit card data and other personal info.
What makes this phishing kit particularly dangerous is that it acts as an all-in-one platform for hackers to launch attacks targeting users in multiple countries with significantly less effort. For instance, instead of studying a bank’s legitimate website and trying to copy it to create a phishing site, this entire process is now automated and can be done with just a few clicks.
Here’s everything you need to know about the Spiderman phishing kit, how hackers are using it in their attacks and what you need to look out for to stay safe from this new threat.
A modular threat
The Spiderman phishing kit is currently being used to create pixel-perfect replicas of European banking and crypto services. However, because of its modular design, the tool could easily be adapted to target financial institutions in other countries like the U.S., Canada, and Australia.
In a new report, researchers at the data security firm Varonis provided further insights on the Spiderman phishing kit and its current capabilities. Right now, it’s being used to target Deutsche Bank, ING, Comdirect, Blau, O2, CaixaBank, Volksbank, and Commerzbank but it can also be used to spoof the online portals of Karna and PayPal as well as steal seed phrases for cryptocurrency wallets like Ledger, Metamask and Exodus.
The big thing that sets Spiderman apart from previous phishing kits is its modular nature. This allows the cybercriminals behind it to add new banks, portals and authentication methods to the tool so that it doesn’t become outdated.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
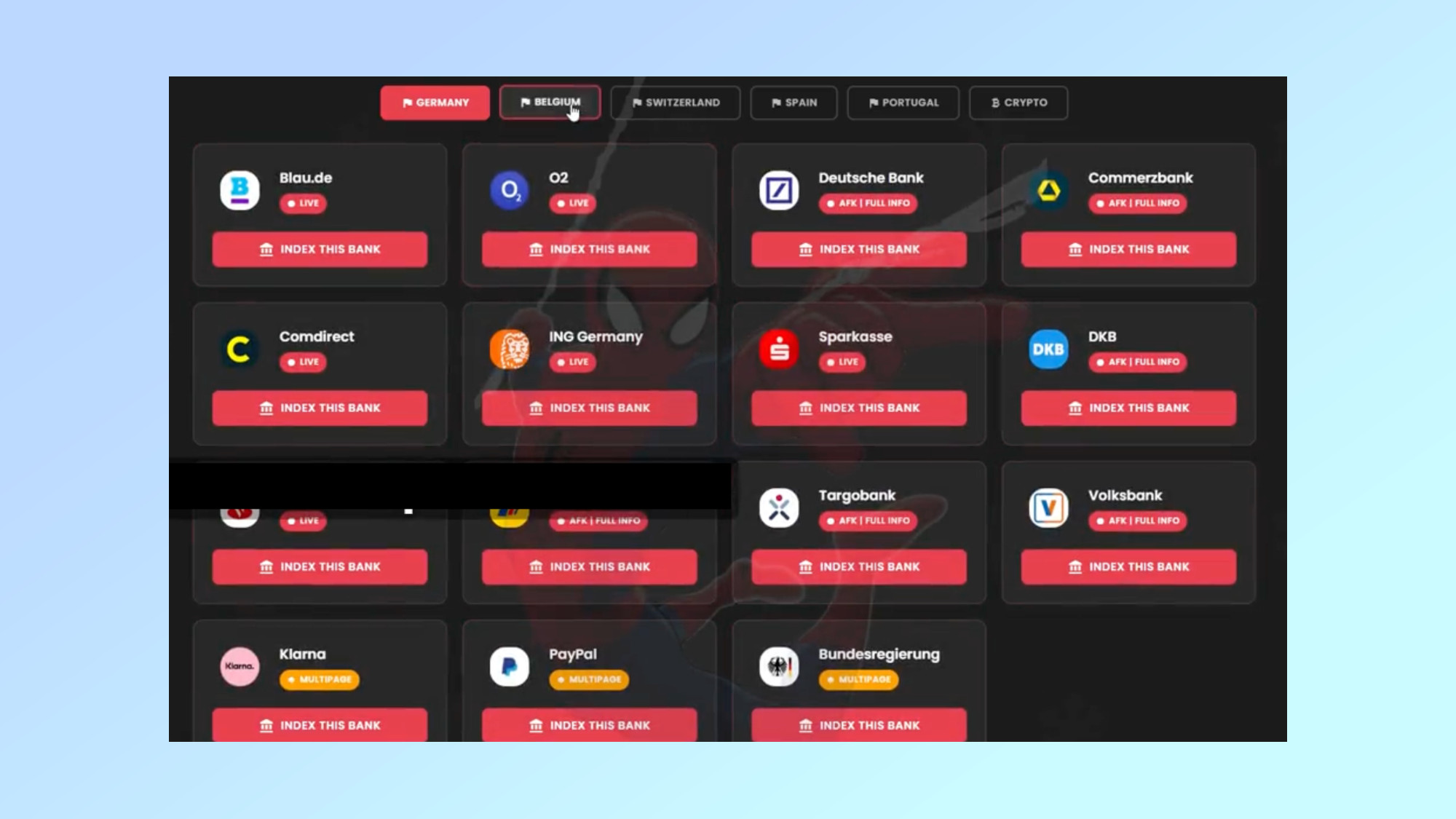
Like other online tools, hackers access the kit from a dashboard where they are able to view victim sessions in real time, capture their credentials, export the data they’ve stolen, harvest credit card details and intercept one-time pass codes including PhotoTAN ones. For those unfamiliar, PhotoTan is a one-time pass code system used by many European banks that displays a colored mosaic image during login or while approving transactions. To continue, users need to scan this image with a bank’s app which decodes the mosaic and displays a one-time pass code which then needs to be entered onto a bank’s site.
Another thing that sets Spiderman apart is its detailed access-control module. This allows hackers to restrict who can load their phishing pages. For instance, they can prevent users from unsupported countries or those on a particular device from loading a phishing page. Unwanted visitors are then sent to Google or another page that isn’t malicious. This selective targeting makes it easier for cybercriminals to evade detection and avoid collecting data on users whose accounts they wouldn't be able to steal.
If a user whose bank is currently supported by Spiderman stumbles onto a phishing page and tries to log in with their username and password, the phishing kit can then collect additional data including their full name, phone number, date of birth, credit card details, IP address and more. With all of this data in hand, hackers using the tool can then take over accounts, launch SIM-swapping attacks, commit credit fraud or even identity theft.
How to stay safe from phishing attacks

Phishing sites may look identical to real ones but a URL with small errors like spelling mistakes or a different top-level domain — like .tv instead of .com — are a dead giveaway.
Besides installing a malicious app, heading to a phishing page and entering your login details is one of the easiest ways to fall victim to a cyberattack. This is why it’s so important to be able to recognize the signs of a phishing attack and to carefully scrutinize the webpages you visit on your phone or computer.
One of the most common ways that hackers carry out their phishing attacks is through unsolicited messages. Whether you get an email, a text message or even a phone call from someone you don’t know out of the blue, you need to be extremely careful. You absolutely shouldn’t click on any links in the message or download any attachments.
At the same time, you also want to manually check the domain name for sites you visit by looking in your browser’s address bar. Phishing sites may look identical to real ones but a URL with small errors like spelling mistakes or a different top-level domain — like .tv instead of .com — are a dead giveaway. Likewise, when it comes to one-time passcodes or 2FA codes, you should never enter one on a website if you didn’t try to login or perform a transaction yourself.
I know not clicking on links or responding to these types of messages sounds easy enough but cybercriminals use a number of different tactics to trick you into letting your guard down and doing things you normally wouldn’t. One of their favorite tactics is to instil a sense of urgency in their phishing emails and messages. For instance, if you think someone you know is in danger or that one of your accounts might be cancelled if you don’t take action immediately, you’re more likely to take action.
This is why I always recommend that you stop and think before interacting or responding to suspicious messages or emails. From there, you want to head directly to the service or reach out to the person in question to independently confirm whether or not a message is true. For example, a hacker might tell you your bank account will be cancelled if you don’t respond in 24 hours. In that scenario, instead of letting your emotions get the best of you, you should reach out to your bank directly on the phone and have them look into the matter for you. When you find out your account isn’t at risk, you should then delete the email or message.
While installing the best antivirus software is always recommended, given the risk of identity theft and financial fraud from phishing kits like Spiderman, signing up for one of the best identity theft protection services makes more sense. These services not only help you recover your identity if it's stolen but can also assist you in recovering funds lost to online scams.
Cybersecurity is often like a game of cat and mouse. Hackers come up with new attack methods or ways to automate their attacks such as using this new Spiderman phishing kit and then from there, companies and security researchers find out ways to stop them. On your end though, the best thing you can do is to improve your cyber hygiene by avoiding risky websites and using security software while educating yourself about the latest threats.
Follow Tom's Guide on Google News and add us as a preferred source to get our up-to-date news, analysis, and reviews in your feeds.
More from Tom's Guide
- New malware turns trusted banking apps into phone hijacking tools — how to stay safe
- Petco data breach — SSNs, credit card info and drivers' licenses exposed
- 4.3 billion job documents left unsecured online — names, emails, phone numbers and LinkedIn data exposed

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits





