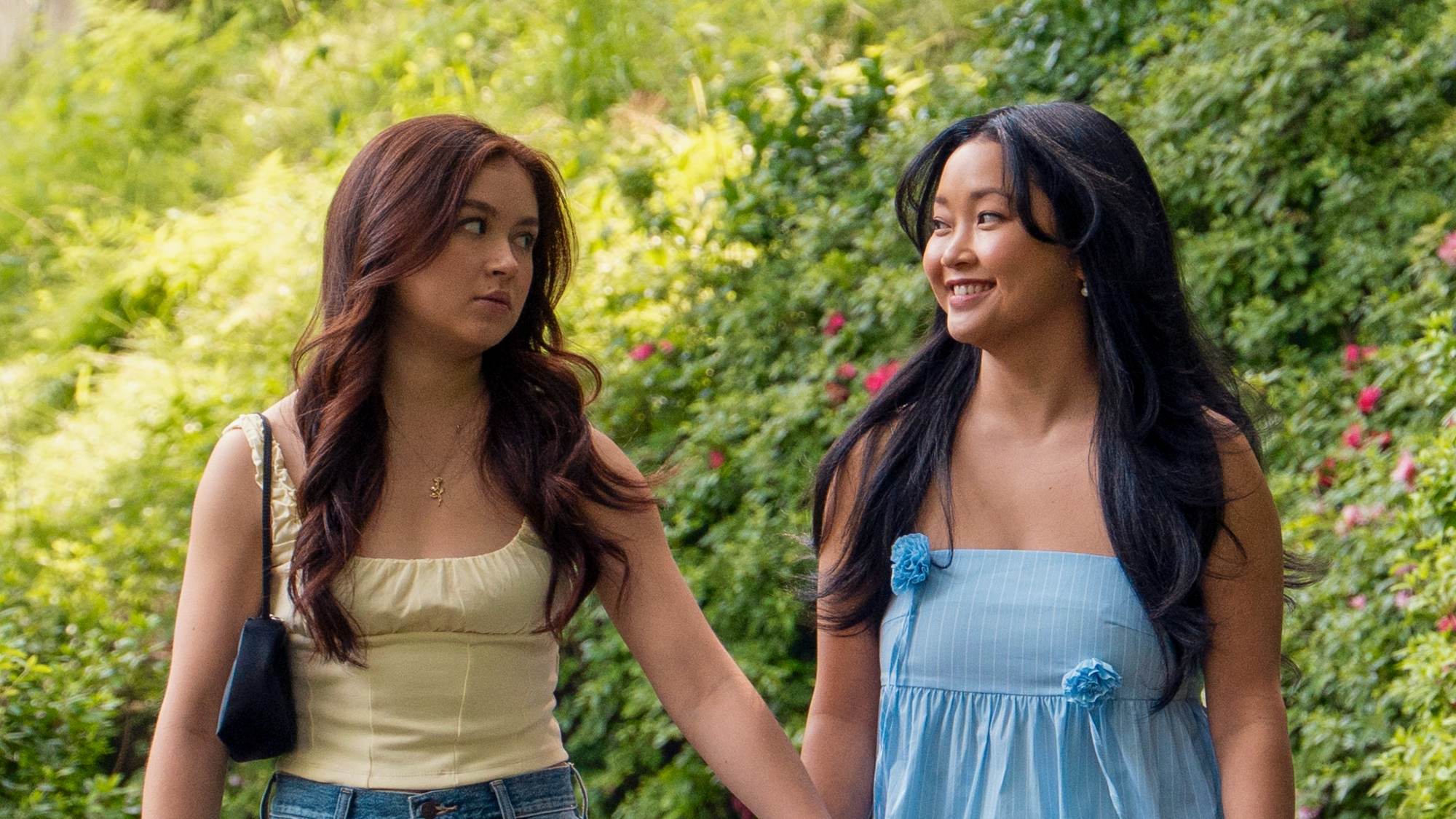News
Explore News
Latest News
'XO, Kitty' season 3 is finally bringing on Lana Condor's Lara Jean Covey — watch a first look
By Christina Izzo published
Lana Condor will reprise her role as Lara Jean Covey in the third season of the Netflix rom-com series "XO, Kitty" season 3, the streamer teases

How to watch 'Sort Your Life Out' with Stacey Solomon online from anywhere
By Caroline Preece published
'Sort Your Life Out with Stacey Solomon' returns for its sixth season in March after a year-long hiatus

'Rooster' episode release schedule: When do new episodes stream on HBO Max?
By Martin Shore published
Want to watch HBO's new Steve Carell-led comedy series? Here's when new episodes of Bill Lawrence's "Rooster" premiere on HBO and HBO Max.

IPVanish has a serious security flaw on Mac – and OpenVPN users need to take note
By Sam Dawson last updated
A critical flaw in IPVanish’s Mac app lets attackers run malicious code with full admin access – here's what you need to know to stay safe.

Potentially risky VPNs are surging in Australian app stores
By George Phillips published
VPNs – including a number of potentially risky ones – are surging up the Australian Apple App Store and Google Play Store. These are the VPNs to choose and avoid.

Sleep Awareness Week 2026 is here — our guide to the best tips, tech and advice to help you sleep better
By Claire Davies last updated
Presented by Helix Sleep
Our guide to Sleep Awareness Week 2026 features expert interviews, the latest longevity science, and the top-rated tech to help you sleep better.

How to watch Big Ten tournament 2026: live stream NCAA college basketball online from anywhere
By Aatif Sulleyman published
All the ways to watch Big Ten tournament live streams online, with the champion set to receive an automatic bid to the NCAA Division I basketball tournament.

When is Disney Pixar's 'Hoppers' coming to streaming? Here's our best guess
By Martin Shore published
Waiting to stream "Hoppers" at home? Here's when I think Disney Pixar's latest animated adventure might come to Disney+ and Premium Video-on-Demand storefronts.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
 Club Benefits
Club Benefits