Update Your LastPass Browser Plugin: Here's Why
LastPass is vulnerable to a serious bug that could allow remote users to not only view your passwords, but run malicious code on machines.

[UPDATE Tuesday April 4: LastPass has patched this vulnerability. All LastPass browser users should update their extensions to version 4.1.44 or later to receive the fix.]
Generally speaking, you’re better off using a password manager than a string of simple (or, horrors, identical) passwords for all of your online accounts.
However, there’s an inherent risk to keeping all of your passwords in one place, as a new LastPass flaw demonstrates. The password-management service is vulnerable to a serious bug that could allow remote users to not only view your passwords, but run malicious code on your machine.
LastPass has posted a blog post with a brief explanation of the bug's existence, and how users should protect themselves. The company's main recommendation is to avoid using the desktop browser plugin to log into websites. Instead, users should log into their accounts on the LastPass website with their master passwords, then use the links in their password "vaults" to open desired websites.
We at Tom's Guide will go further and recommend uninstalling LastPass browser extensions entirely, or at least disabling the extensions, for reasons detailed below. Users who do so will still be able to log into their accounts on the LastPass website. (LastPass confirmed to Tom's Guide that LastPass mobile apps are not affected by this flaw.)
MORE: Best Password Managers
Tavis Ormandy, a security researcher from Google’s Project Zero team, discovered the bug this past weekend, and let users know about the vulnerability on his Twitter feed. He also explained a few salient details about how the flaw could be exploited in the replies to his initial post. The insight into the flaw came to him, as great ideas often do, while in the shower.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.
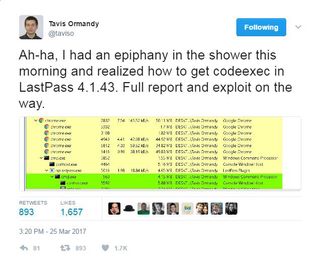
"It will take a long time to fix this properly," Ormandy tweeted. "It's a major architectural problem."
Ormandy has created a proof-of-concept exploit of the vulnerability, although for obvious reasons, he hasn’t shared it with anyone but LastPass yet.
Briefly, here’s what the flaw affects: LastPass offers browser extensions for Mozilla Firefox, Google Chrome, Opera, Maxthon, Microsoft Internet Explorer, Apple Safari and Microsoft Edge. Linux and ChromeOS users don’t get off easy; Ormandy confirmed that the bug affects those operating systems as well as Windows and macOS/OS X.
In most cases, the browser plugin is a binary file, i.e. a small application of its own. "Non-binary" LastPass plugins are available for Chrome, Opera and Safari, but the default LastPass installation tool puts binary plugins in all browsers installed on a machine.
When the binary plugin is running, a remote user could exploit an undisclosed flaw in the binary to implement malicious code on a user’s machine. When the binary is not running, but nevertheless installed in the browser as an extension, a remote user could still access a user’s entire list of passwords.
It may be that even the non-binary plugins allow password theft -- Ormandy vaguely said on Twitter that "code execution if you use the binary component, otherwise can steal passwords." We'll have to wait for further disclosure to know for sure how deep this goes, but for now, you'll probably want to uninstall, or at least disable, all LastPass plugins.
LastPass doesn’t want to share any technical details about the flaw just yet, but it does have three recommendations for users. The first is to use the LastPass Vault (on the company’s website) to access your accounts rather than the browser plugin. The vulnerability doesn’t affect the LastPass site itself.
Second, activate two-factor authentication on any service that allows it (including LastPass itself). This will prevent remote users from accessing your accounts, even if they acquire your passwords.
Finally, LastPass advises users to beware of phishing scams, as the publicity surrounding this flaw will encourage scammers to try to entice LastPass master passwords out of scared users.
Ormandy has given the company 90 days to release a patch before he reveals technical details, which is standard practice among security researchers.
"No need to scramble,” Ormandy pointed out on his Twitter feed.
LastPass is probably becoming more familiar than it would like with Ormandy’s epiphanies. Last week, Ormandy discovered two other vulnerabilities in LastPass, which the company quickly patched.
Perhaps LastPass will patch the current vulnerability as quickly, although if it’s as big as Ormandy suggests, it will probably take a bit longer. At least once it’s all over, there will be a very interesting post-mortem on the LastPass website.
Marshall Honorof is a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.

