News
Explore News
Latest News

TikTok USA is not working — live updates on the massive 'disruption' after ownership transition
By Jason England last updated
TikTok USA is experiencing severe disruptions that started just hours after the deal was signed to transition it into America. Here's what is happening.
This Walmart TV brand is 'emerging as Samsung's strongest competitor in North America'
By Nick Pino published
Onn. and Vizio now control 5% of the global TV market and much more in the US — here's what that could mean for you when shopping for your next big-screen TV.

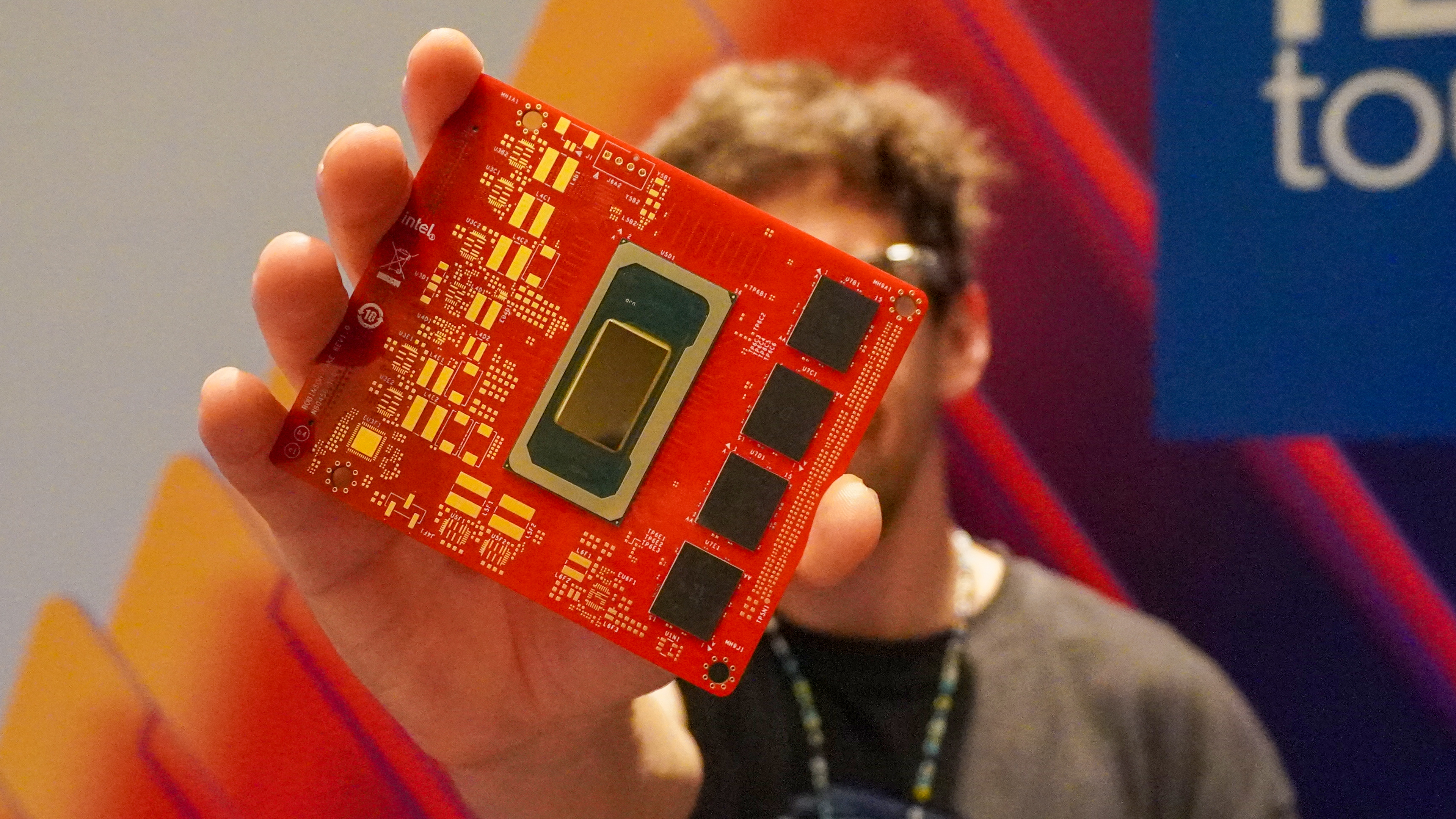
We just benchmarked the Intel Core Ultra X9 388H — AMD is officially on notice
By Tony Polanco published
Intel isn't messing around with its flagship laptop processor

How to watch Australian Open 2026: FREE live streams from anywhere, Day 10 order of play, preview
By Aatif Sulleyman last updated
How to watch Australian Open 2026 live streams for free, with Aryna Sabalenka, Coco Gauff, Carlos Alcaraz and Iva Jovic in action at Melbourne Park on Day 10.

Independent audit confirms Surfshark's infrastructure 'aligns with the highest security standards'
By George Phillips published
An independent audit has confirmed Surfshark's infrastructure maintains high security standards. Here's everything you need to know about SecuRing's assessment.

How to watch ICC Men's T20 World Cup 2026: FREE live streams, preview, schedule
By Aatif Sulleyman last updated
How to watch Men's T20 World Cup 2026 live streams for free, with Australia, England and reigning champions and co-hosts India amongst the favorites.

Apple AirTag 2 just announced with ’50% louder’ speaker, longer Bluetooth range and better Precision Finding
By John Velasco published
Apple just announced the AirTag 2, with new hardware upgrades like an ultra wideband chip, 2x louder speaker, expanded Bluetooth range, and more

Apple's new Gemini-powered Siri is finally coming in February — everything you need to know
By Richard Priday last updated
Apple should finally launch its Siri 2.0 features in iOS 26.4 next month, but Bloomberg's Mark Gurman says even more is coming to Siri this summer as a result of Apple and Google's AI deal.

ChatGPT’s traffic share hits lowest point since 2023 as Gemini surges — new report exposes pressure on OpenAI
By Amanda Caswell published
ChatGPT’s share of AI web traffic has fallen to its lowest point since 2023 while Google’s Gemini continues to surge, according to new Similarweb data.

I’m benchmarking an Intel Core Ultra X9 388H laptop right now — what would you like me to test?
By Jason England last updated
I've just started testing the new Asus Zenbook Duo — the first ever Intel Core Ultra X9 388H laptop. For Tom's Guide's first ever live Q&A, I have one simple question: what do you want me to test?
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
 Club Benefits
Club Benefits