I found a phishing email in my inbox and a malicious app in my news feed — here’s how I knew they were scams
From my inbox to your eyes: real examples to help you learn how to spot a scam

When you write about the worst online scams and how to avoid them everyday like I do, it’s easy to start seeing plenty of examples in the real world.
While it’s one thing to tell you what to look out for when malicious apps are making the rounds online or after a major data breach, it’s another to show you. That’s why I’ve started taking screenshots of all of the various hacking attempts and potential cyberattacks I come across online.
Given that I’ve written about hackers for over a decade now, I’ve seen all of their tricks and the various tactics they use to get you to click on malicious links or to willingly hand over your personal information. This time instead of telling you about the latest cyberattack, I’m going to walk you through two hacking attempts I encountered last week and explain exactly why I didn’t click on or download anything.
Here’s everything you need to know along with some more general tips and tricks I use to keep myself and my family safe online.
Not a normal email but a trap

As someone with a publicly available work email address, I get around 100 emails each day. While many are from trusted contacts I work with directly or indirectly as part of my job, the odd suspicious email does manage to bypass my inbox’s built-in security measures from time to time.
That’s exactly what happened with the email below. However, there were several red flags that I noticed almost immediately. Can you spot them too? Take a quick look before reading my explanation to see if you caught them all.
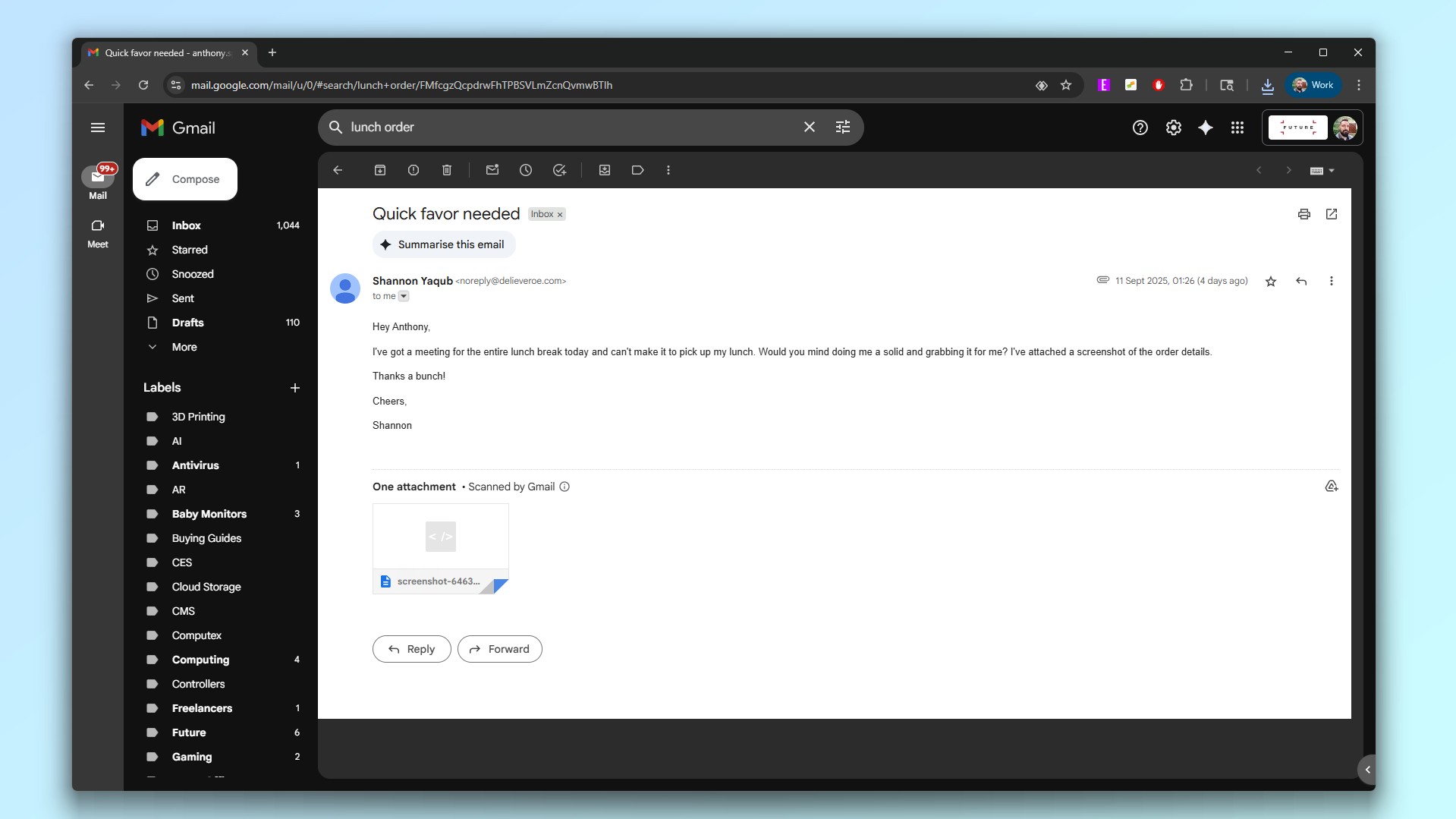
Let’s start with the subject header which reads “Quick favor needed.” This is an immediate red flag as hackers and scammers also try to instill a sense of urgency in their phishing emails to get you to open and interact with them.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The request itself is quite simple: pick up lunch for a co-worker who can’t do so herself because she’s at a meeting. However, I work from home and have never heard of this person before. Now if the scammer behind this message wanted to take things up a notch, they would have searched for one of my real co-workers’ names to make their message appear more legitimate. They didn’t though, which shows this is a less sophisticated attack and that no social engineering techniques were used to make this phishing email appear more legitimate.
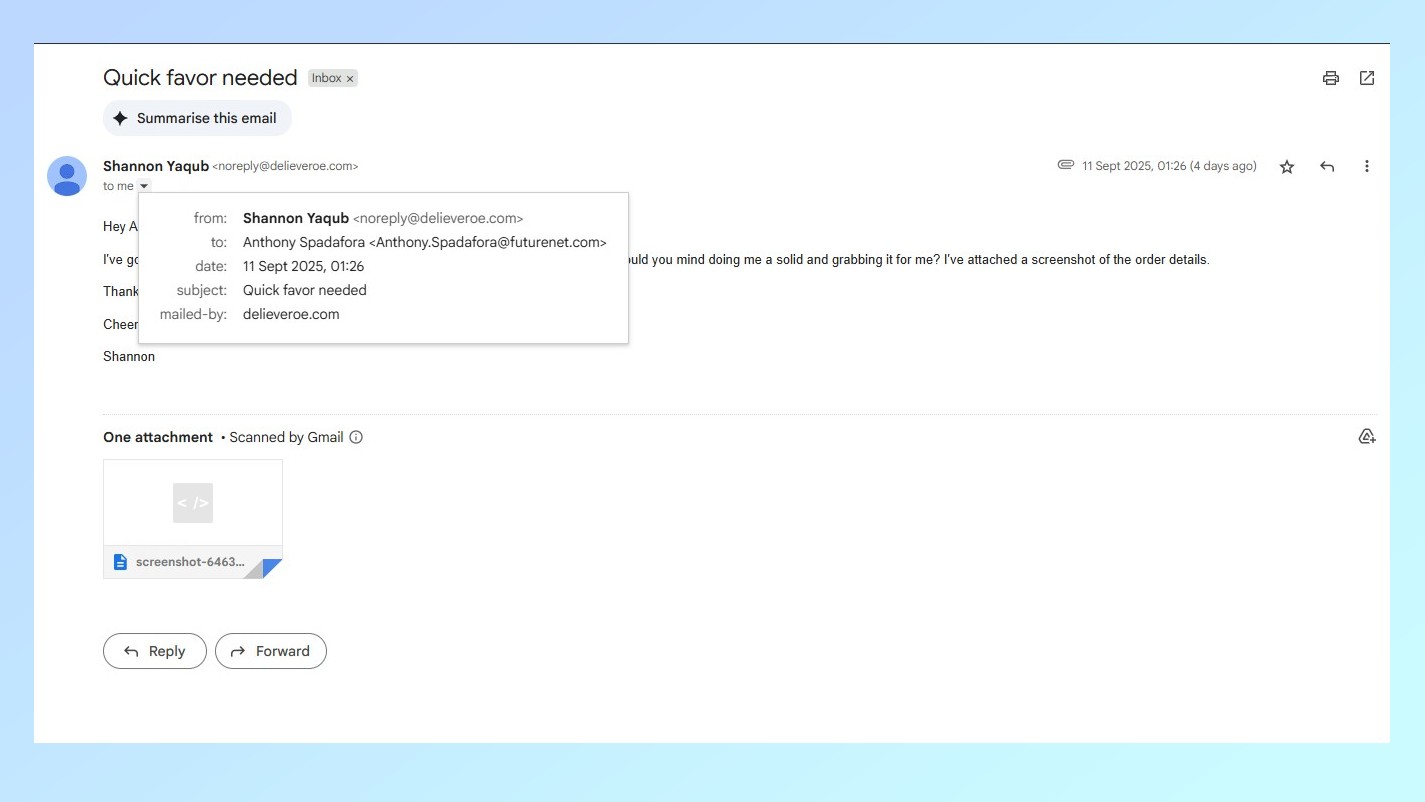
Although I didn’t recognize the sender’s name which already had my spidey senses tingling, I still clicked on the arrow underneath it to further inspect their email address. Instead of being tied to their name, the email listed above uses the name of a popular food delivery company to make it appear more legitimate but there’s just one problem. The company the scammer is trying to impersonate is likely Deliveroo, but the name in the email address is spelled wrong.
To help me pick up their order, my ‘co-worker’ also included a picture of their order as an attachment in their email. However, while the message says they’ve “attached a screenshot”, this attachment isn’t a picture at all. Instead it’s an HTML file disguised as a picture with the word “screenshot” in the file name to make it appear legitimate.
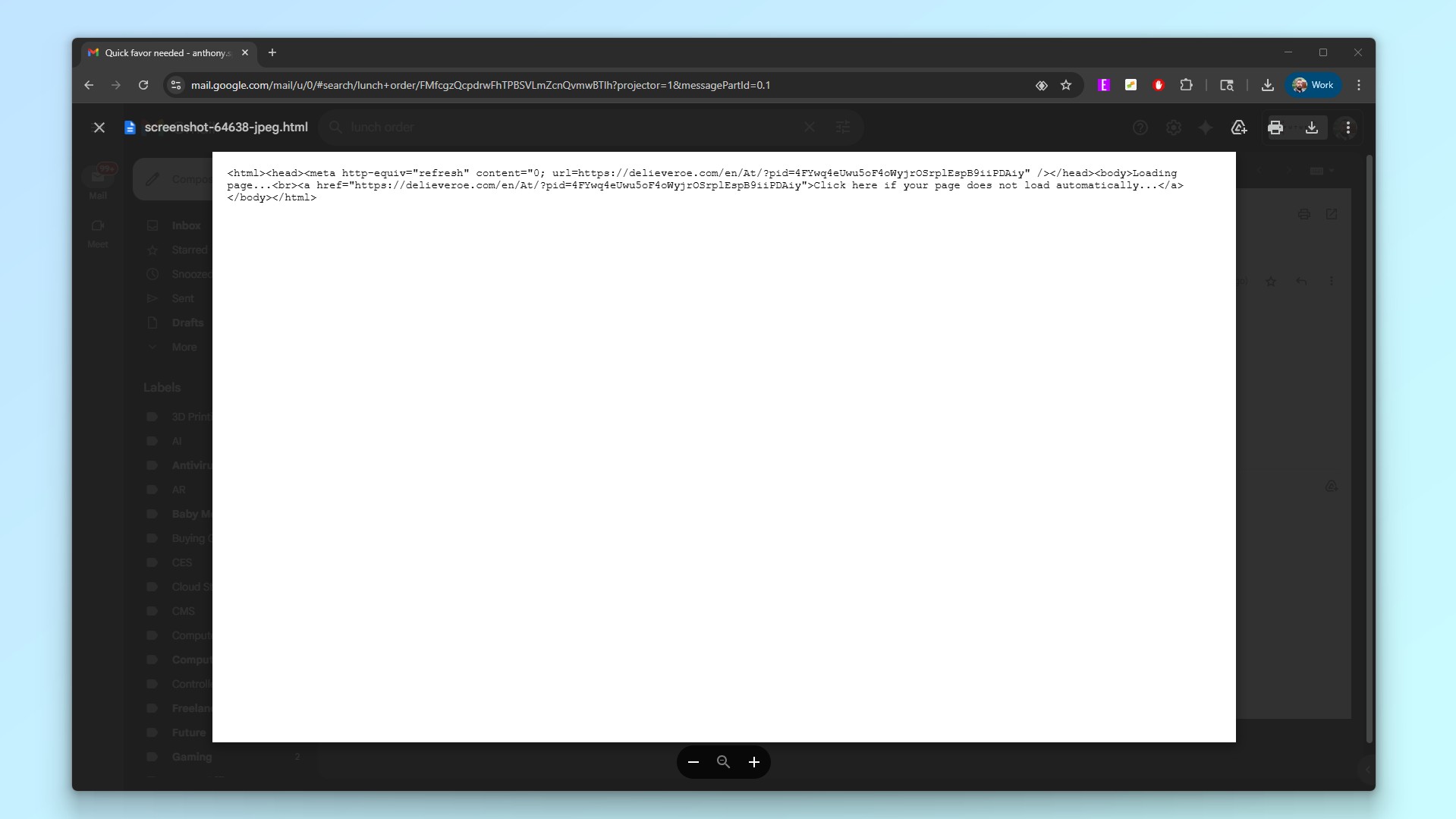
Now I wouldn’t recommend that you do what I did but in this case, I clicked on the preview to give you a better idea of the code contained in the attachment. As you can see in the screenshot above, it points to a fake site impersonating Deliveroo with text on the page that indicates it’s loading which appears when you navigate to it. On this fake site, there’s also a button that reads “Click here if your page does not load automatically.”
Even though I didn’t actually download this attachment or try to open it, clicking that button on the page it was trying to lead me to likely would have taken me to a malicious site designed to infect my computer with a virus.
This email has all the hallmarks of a phishing email from a sense of urgency to an attachment that isn’t what it claims to be. In fact, the only thing it’s missing are spelling and grammatical errors. Besides that though, this is a textbook example of a phishing email and if you see anything like this in your own inbox, avoid responding to it or downloading the aforementioned attachment at all costs.
Malware hiding on my news feed
Even before I wrote about cybersecurity for a living, I was an avid news hound. That’s why whether it’s on my phone or my tablet, you’ll often find me scrolling through Google Discover looking for interesting stories. Well, I was doing just that the other day when I came across a fake story designed to trick me into installing a malicious app, let me explain.
While I should know, I’m still not quite sure when daylight savings time ends. That’s why when I saw a story on the subject pop up on my news feed, I gave it a quick tap.
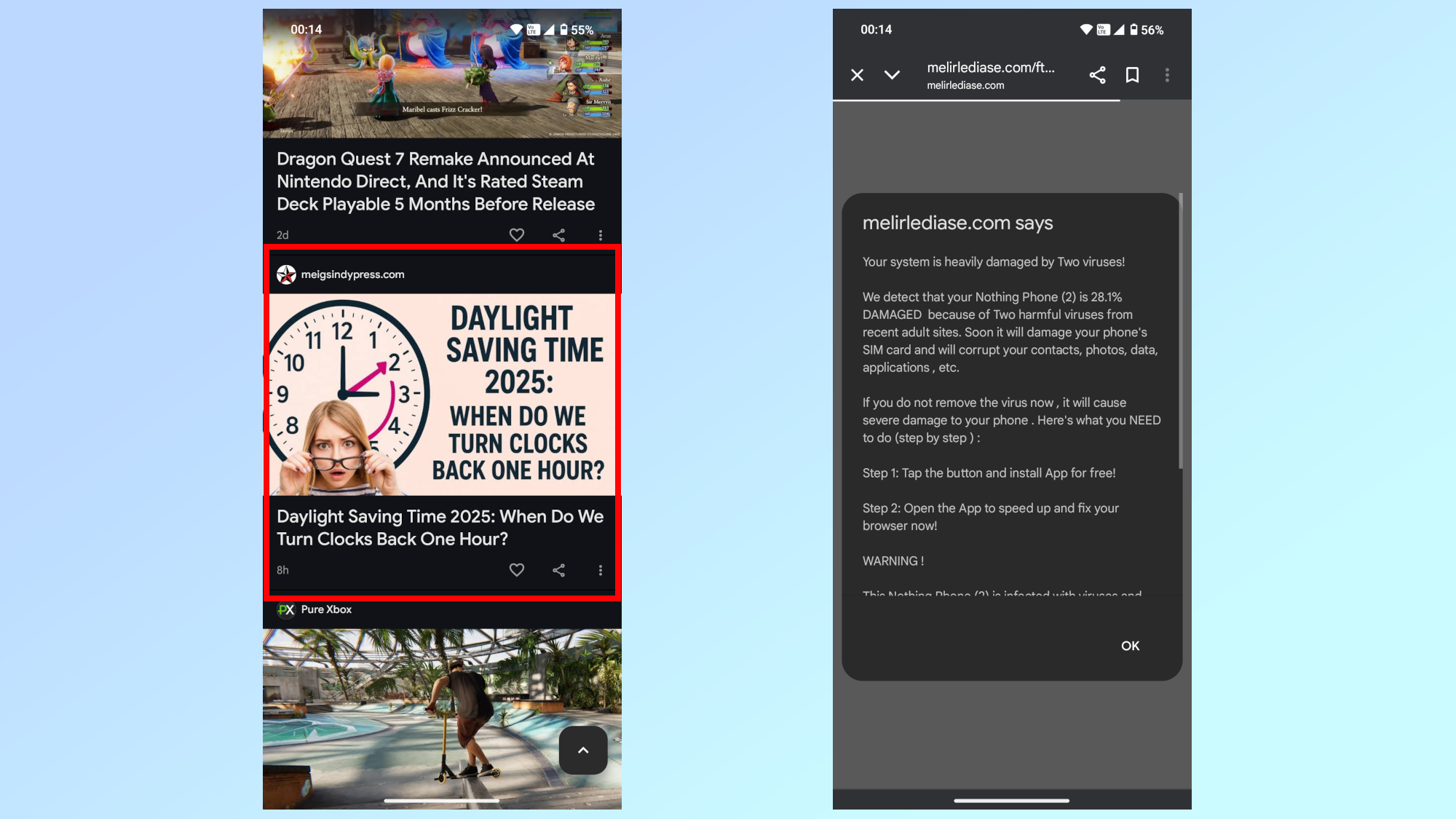
In the screenshot above, you can see the story I clicked on the left side and the pop-up I was greeted with immediately after doing so on the right. As a result of recent algorithm changes, Google Discover has started surfacing more personal blogs in addition to news stories from trusted sources. While this is a good thing for smaller outlets and creators, it also gives cybercriminals a chance to more easily prey on avid news readers like myself.
Instead of finding out when daylight savings time ends this year, I saw a pop-up telling me that my Nothing Phone 2 was infected with not one but “two harmful viruses.” The cybercriminals behind this malicious pop-up took things a step further by claiming these so-called viruses came from “recent adult sites.” Then, to get me to follow their instructions, they used the threat that my phone’s SIM card would be damaged and that my contacts, photos, data, apps and more would be corrupted if I didn’t download the app in question.
Now I didn’t scroll all the way down and try to download what was almost certainly a malicious app, but here’s what would have likely happened if I did. Instead of taking me to the Google Play Store or another official app store, the link at the bottom of this message would have taken me to a third-party site where I could download this app as an APK file. From there, I would need to sideload it onto my Android phone (something Google is getting rid of in the next version of Android). To get access to all of my data, the app likely would have asked for a number of unnecessary permissions either to abuse Android’s Accessibility services or to download a fake update that was actually dangerous Android malware.
I’ve seen this type of thing too many times before to go through with it but this is the first time I’ve seen a fake news article trying to spread malware pop up on my Google Discover feed. This is a great warning though about how hackers can create blog posts or even buy ad space as a way to lure in potential victims.
How I stay safe from cyberattacks

When it comes to protecting myself and my friends and family from cyberattacks, the first and most important thing I recommend is not to let your emotions get the best of you. Hackers know all too well how to elicit an emotional response which is necessary to get unsuspecting users to fall for their phishing emails and other scams.
This is why I always suggest that people try to keep a level head when checking their inbox or their messages. From emails warning you about copyright strikes to ones that say one of your accounts is suspended or will soon be closed, hackers want to get you to act and to do so quickly without thinking. That way, you're more likely to make a mistake. By the time you’ve logged into your online accounts on a fake login portal or sent over sensitive personal data and realized something is amiss, it’s too late.
For this reason, you want to keep the signs of a phishing email or message in mind when going through your inbox or messages. Does the message try to convey a sense of urgency? Are there spelling and grammar errors? Is there a suspicious attachment or link included in the message? These are all questions that when answered with a yes are cause for concern.
From there, I use one of the best password managers to not only help me create strong and unique passwords for all of my accounts but also to securely store and autofill them when need be. I also use the best antivirus software on my computer and one of the best Android antivirus apps on my phone. While your computer comes with built-in security software in either in the form of Windows Defender on PC or XProtect on Mac and your Android phone comes with Google Play Protect, using a paid antivirus alongside it will also usually give you access to some useful extras like a VPN to protect your privacy online or a hardened browser which can be useful when banking online or handling other sensitive data.
At the end of the day though, the most important thing I do is to educate myself on the latest cyberattacks and scams. Hackers have a wide arsenal of tricks and techniques that they reuse across their attacks which is why knowing how to spot a scam or a fake email or website is so important.
These are just the two most recent hacking attempts I’ve come across but if you’d like me to share more of them and explain how they work, let me know in the comments below.
Follow Tom's Guide on Google News and add us as a preferred source to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button!
More from Tom's Guide
- This new Android banking trojan can automatically transfer money off your phone to hackers
- 7 iPhone security settings you should enable right now to lock down your smartphone
- Those urgent text messages aren't from your motor vehicle department — here's how to tell they're fake

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits





