10 Easy-to-Use Security and Privacy Tools
These 10 security and privacy tools are both effective and user-friendly.


For a long time, people thought that technologies couldn't be both secure and easy to use.
But that's changing: These 10 tools are not only intuitive and simple; they also maintain your security and privacy. Whether you're an activist, a businessperson, a traveler in a foreign country, or you simply want to feel a bit more secure in your Internet use and communications, these tools are for you.
TextSecure
Why you can trust Tom's Guide
Many companies claim that their instant-messaging mobile apps are secure, but a good number of them fail to deliver on that promise. (We're looking at you, Snapchat.) Even the more secure ones won't work unless the people you want to talk to are using the same app.
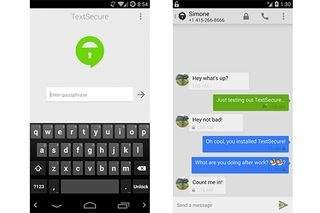
That's why we like free Android app TextSecure. With TextSecure installed, when you send SMS and MMS messages to other TextSecure users, your messages will have end-to-end encryption. The app doesn't work when you text non-TextSecure users, however; in that case your messages transmit as usual, without the encryption. Either way, you can keep texting the way you're used to doing.
MORE: How to Use TextSecure to Send Encrypted Text Messages
Wickr
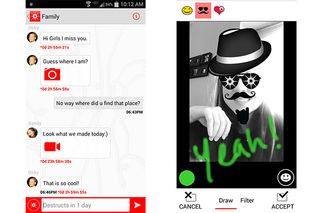
If you're really serious about secure mobile messaging, you'll want to check out Wickr, a free messaging app for Android and iOS that encrypts your messages right on your mobile device. People you communicate with also need to have Wickr installed, but all the data that passes through Wickr's servers is encrypted with a temporary key so that even Wickr can't read your messages.
MORE: How to Use Wickr Privacy App
Aviator
To paraphrase Melisandre from Game of Thrones, the Internet is dark and full of perils. To make your Internet browsing a little safer, we recommend the free Aviator browser from WhiteHat Security.
Aviator looks similar to Google Chrome (it's based on the same open-source Chromium browser), but it comes with tough security settings enabled by default. For example, it blocks cookie tracking, ads and JavaScript (you'll have to manually start each YouTube video) and doesn't store search history or passwords.
MORE: Aviator: Hands-On with the Most Secure Web Browser
Antivirus programs
This one's a no-brainer. If you haven't installed one of the best antivirus software programs on your computer, you're missing out on the easiest way to keep your computer safe.
Most paid antivirus programs for PCs have very intuitive interfaces and easy setups, and can be set to automatically scan for and remove malicious programs from your computer.
When it comes to free PC programs, the usability isn't quite as good. You probably won't be getting the same caliber of protection, but they're still relatively easy to set up.
MORE: Best Free Antivirus Software
Antivirus programs for Macs vary wildly in quality, but for the best Mac antivirus software, offering a balance of usability and interface, you may want to look at offerings from Avast, Sophos or Intego.
And don't forget to get protection for your Android device -- check out our list of the best Android antivirus apps. (But please read our explainer on why iPhones don't need antivirus software.)
Cryptocat
Cryptocat is an option for people who need to communicate securely from a variety of devices. This open-source encrypted chat service works in the Chrome, Firefox, Safari and Opera Web browsers, as well as natively on OS X and iPhone. (There's currently no Android version.)
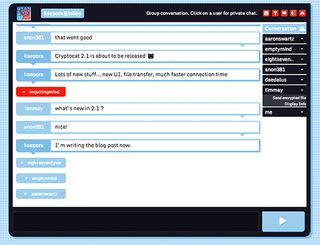
Though Cryptocat did have a few problems with security several years ago, many security experts agree that Cryptocat has turned itself around and become a trusted messaging service. Now, like Wickr, Cryptocat's encryption is designed so that even Cryptocat's creator can't read the messages transmitted through its servers.
If you want to securely send instant messages from your computer as you work, Cryptocat may be the service for you.
Smartphone encryption
Text messages, emails, Web search histories, shopping history and financial data — your smartphone contains a lot of sensitive information. That's why many smartphones now come with a means of encryption — in other words, formatting the device so some or all of your data is stored in a scrambled form. This will make it more difficult for phone thieves, cybercriminals and investigators to read your data.
For Apple users: All iOS devices, from the iPhone 3GS and up, come with some level of hardware-level encryption baked into the phone's circuits. The unique encryption keys (to decrypt your data so you can read and interact with it) are also stored on your device.
To complete this protection, all you have to do is set a passcode on your iOS device's lock screen. This passcode will restrict people from accessing your phone's encryption keys.
MORE: How to Encrypt Files on iOS
On Android phones and tablets, it's a little trickier for now. Unlike iOS, Android doesn't automatically encrypt a device when a password is set, but if your device is running Android Gingerbread 2.3.4 or higher, you can easily enable it. This, too, will require you to set a passcode for your device's lock screen.
MORE: How to Encrypt Your Android Phone or Tablet
The latest versions of both mobile operating systems improve encryption even further. Whereas iOS previously encrypted only some of the files on a device, the newly released iOS 8 encrypts them all. The next major update to Android, already available for software developers and dubbed "L" until an official name is chosen, will also fully encrypt a device when a passcode is enabled.
Two-factor authentication
Now that major data breaches seem to be disclosed every week, using two-factor authentication (also called two-step verification or two-factor verification) is essential to online security.
Don't know what that is? You already use two-factor authentication at ATMs. Your bank card is the first factor of authentication; your PIN, which is not on the card, is the second.
Most online accounts can be unlocked with just a password, which is one factor of authentication. But passwords can be lost, forgotten, stolen or covertly reset, which makes them pretty weak lines of defense.
With two-factor authentication enabled on an online account, anyone trying to log in first enters the regular password. He or she is then prompted to enter a second, randomly generated, temporary number that has been texted to the legitimate account holder's personal mobile phone. (A voice call can also be made.)
Not only does this provide double the security of a password, but two-factor authentication relies on two different types of verification information: something you know (a password) and something you have (a cellphone registered to the legitimate account holder). Cyberintruders will need your cellphone as well as your password in order to access your account.
MORE: How to Turn On Two-Step Verification
Most major online services — including Facebook, Google, Microsoft and Twitter — offer two-factor authentication, though some are not as good as others. Apple, for example, recently expanded the range of iCloud features protected by two-factor authentication after it was discovered that data thieves had accessed celebrities' iCloud backups and stolen personal photos even with two-factor authentication turned on.
SpiderOak
Practically everyone uses cloud storage these days. But how secure are the files you store in the cloud?
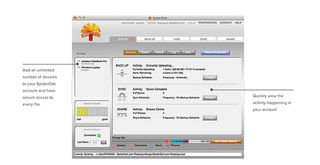
Cloud storage service SpiderOak may not be as easy to use as more widely known systems such as Dropbox or Google Drive; for example, it doesn't have local folder integration as the latter two do.
SpiderOak locally encrypts every document you upload to its systems. Your documents are encrypted before they even leave your machine, and they stay that way, during transmission to SpiderOak's servers and while they're stored there. If anyone were to intercept the transmission or gain access to SpiderOak's servers, all they would be able to see would be the unreadable encrypted versions of your documents.
RedPhone
Ever since the very first leak by Edward Snowden revealed that American telecommunications company Verizon shared telephone-call metadata with the National Security Agency, people have been skeptical of phone communications. If that sounds like you, check out RedPhone, an Android app for making encrypted VoIP (voice over Internet Protocol) calls.
RedPhone, made by the same company that produces TextSecure, also keeps you safe from potential snoops. Anyone listening in to your calls will just hear static, thanks to the app's end-to-end encryption.
But RedPhone makes our list because of its easy-to-use interface. Since you register to RedPhone with your phone's regular number, you can make and receive calls as before. To call another RedPhone user via the encrypted service, just use the app's interface, or dial the person's number with an asterisk at the end. Because RedPhone's calls go over the Internet instead of telephone lines, all calls are completely free.
MORE: How to Use RedPhone for Android
Guest Wi-Fi network
This one isn't a product but rather a useful tool that you can set up with many home wireless routers. To increase your (and your family's) security, set up a second, "guest" Wi-Fi network. This way, you won't be handing out the password to your home network to everyone who stops by.
MORE: How to Secure Your (Easily Hackable) Smart Home
If you have any "smart" appliances, you may want to connect these to a guest network or second network as well, since many smart devices have little to no built-in security. Should these smart appliances become compromised, isolating them on a separate network will keep your other devices safe.
- iOS 8 Adds Serious Security Improvements
- 7 Scariest Security Threats Headed Your Way
- Best PC Anti-Virus Software 2014
Jill Scharr is a staff writer for Tom's Guide, where she regularly covers security, 3D printing and video games. You can follow Jill on Twitter @JillScharr and on Google+. Follow us @tomsguide, on Facebook and on Google+.
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.
Jill Scharr is a creative writer and narrative designer in the videogame industry. She's currently Project Lead Writer at the games studio Harebrained Schemes, and has also worked at Bungie. Prior to that she worked as a Staff Writer for Tom's Guide, covering video games, online security, 3D printing and tech innovation among many subjects.
