Windows 10's antivirus can download malware — Microsoft responds
Security tool built into Windows 10 can undermine security
UPDATE: As of Sept. 18, Microsoft has removed this feature, according to Bleeping Computer.
Well, here's a fine mess: The latest version of Windows Defender Antivirus for Windows 10 can be used to download malware.
That's according to Bleeping Computer, which noticed a Twitter thread from security researcher Mohammad Askar in which Askar detailed how the Windows Defender command-line tool MpCmdRun.exe can be used to download any file from the internet.
- The best antivirus software to keep your system clean
- Watch out, Zoom: Microsoft Teams is getting a killer new feature
- Latest: Nvidia GeForce RTX 3080 revealed: Date, price, specs, pre-order
So, of course, Askar used it to download a (safe) piece of threat-emulation software called Cobalt Strike, which is used to detect security holes in large local computer networks. Bleeping Computer went a step further and used the Windows Defender tool to download a sample of actual ransomware.
We ourselves, after a bit of command-line fiddling, used the tool to download an image from the Tom's Guide website. That was done using administrative privileges, which you'd figure would be required to go into Windows Defender and use a command-line tool to download any file.
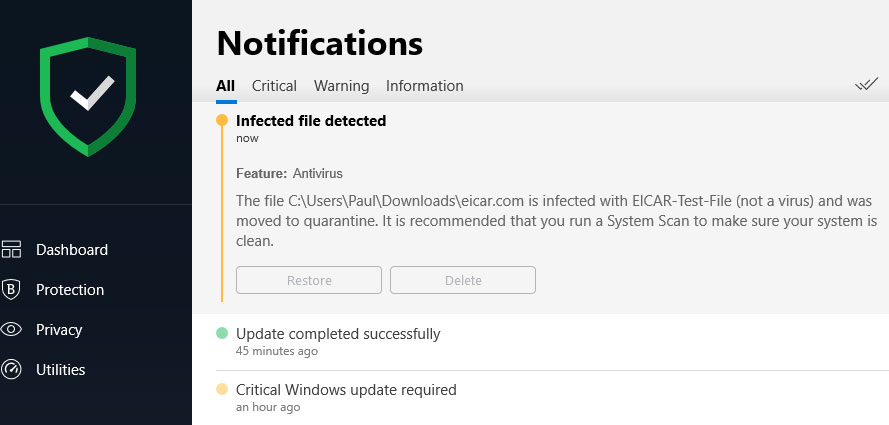
Just to see how far we could go with this, we switched back to our regular limited-user mode. Then we used the same tool to download the EICAR test file -- a well-known piece of simulated malware -- to our own limited-user download folder. No administrative privileges were required.
Microsoft responds
Microsoft responded to our request for comment with this statement, in full:
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
"Despite these reports, Microsoft Defender antivirus and Microsoft Defender ATP will still protect customers from malware. These programs detect malicious files downloaded to the system through the antivirus file download feature."
A Microsoft spokesperson clarified that the statement also applies to Windows Defender Antivirus, the antivirus software that comes bundled into Windows 10 Home.
Oh the irony
This means that any piece of decently functioning malware that infects even a limited-user account will be able to use Windows Defender itself to download any file from the internet.
There were a couple of saving graces. We were not able to download the EICAR test file to another user's download folder or to directories to which we weren't entitled to write to or hadn't created ourselves -- even when logged in as an administrator.
That conforms to the Windows user parameters and indicates that this Windows Defender download tool can't be used to escalate privileges. In other words, malware can't use it to easily seize system control.
Also, our Bitdefender antivirus software spotted and quarantined the EICAR test file right away every time. We don't use Windows Defender ourselves as our default antivirus software, but Windows Defender would almost certainly have also spotted and defanged the EICAR test file as well.
So in those respects, the Windows Defender download tool can't be used to do anything worse than any malware that successfully infected your system could normally be permitted to do, such as downloading a file through a web browser.
But there's always stuff that AV software won't detect. And of course Windows Defender is still present on every Windows 10 PC, whether or not you use third-party antivirus software. That's normally a good thing.
We've reached out to Microsoft for comment and will update this story when we receive a reply.
You can try this at home (but most people shouldn’t)
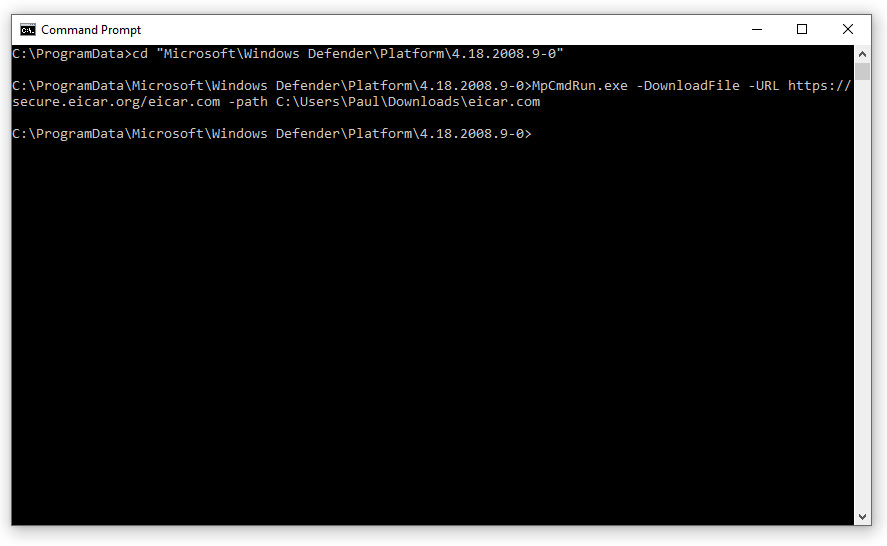
If you're wondering how to do this, here's the filepath and commands. But make sure you know what you're doing:
C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2008.9-0\MpCmdRun.exe -DownloadFile -URL <url> -path <local-path>
"<url>" is the URL you're downloading from, and it has to include the filename you want, such as "https://www.example.com/example/foobar.txt."
"<local-path>" is where you want the file to go, and you have to include the filename there as well: "C:\Users\You\Downloads\foobar.txt".
We found it easiest to just change directories to C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2008.9-0\ and then proceed from there. Your mileage may vary.
Update: Microsoft response
Microsoft responded to our request for comment with this statement, in full:
"Despite these reports, Microsoft Defender antivirus and Microsoft Defender ATP will still protect customers from malware. These programs detect malicious files downloaded to the system through the antivirus file download feature."
A Microsoft spokesperson clarified that the statement also applies to Windows Defender Antivirus, the antivirus software that comes bundled into Windows 10 Home.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
 Club Benefits
Club Benefits





