What to Do If You're Infected by Ransomware
If ransomware hits your computer, don't panic. Here are several things you can do.
Ransomware infection can be pretty scary. If you see a note appear on your computer screen telling you that the computer is locked, or that your files are encrypted, don't panic. Instead, take a deep breath, sit down and consider your options.

There are a number of steps you can take to try to regain control of your Windows system and files before you need to decide whether you'll pay a ransom.
Find out what kind of ransomware you have
First, you'll need to determine whether you've been hit by encrypting ransomware, screen-locking ransomware or something that's just pretending to be ransomware. See whether you can access files or folders, such as the items on the desktop or in the My Documents folder.
If you can't get past the ransom note you see on your screen, you're likely infected by screen-locking ransomware, which is not so bad. If you see a notice claiming to be from the police, the FBI or the IRS that says you've been caught looking at pornography or filing false taxes and must pay a "fine," that's usually screen-locking ransomware, too.
MORE: Best Antivirus
If you can browse through directories or apps but you can't open your regular office files, movies, photographs or emails, then you have encrypting ransomware, which is far worse.
If you can both navigate the system and read most files, then you're probably seeing something fake that's just trying to scare you into paying. You can ignore the ransom note. Try closing your web browser. If you can't, then hit the Control, Shift and Esc keys at the same time to open Task Manager, choose the Application tab, right click the browser application and select End Task
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Should you pay the ransom?
Most security experts, as well as Microsoft itself, advise against paying any ransoms. There's no guarantee you'll get your files back if you pay, and paying just encourages more ransomware attacks. (Don't pay the ransom for screen-locking ransomware, because you can almost always get around it.)
However, when you need to recover legal, medical or business records, precious family photos or other important files, paying $300 or so looks like a viable option — and most ransomware criminals do unlock the files after ransoms have been paid. So we'd rather stay neutral on the subject of whether paying ransoms is advisable or morally acceptable.
How to deal with encrypting ransomware
Because encrypting ransomware is the most common and most harmful kind, we'll deal with that first. Perform each of these steps in order, even if you know you've recently backed up your files. Stop when you've succeeded in recovering your files.
1. Disconnect your machine from any others, and from any external drives. If you're on a network, go offline. You don't want the ransomware to spread to other devices on your local network or to file-syncing services such as Dropbox.
2. Use a smartphone or a camera to take a photograph of the ransom note presented on your screen. If you can take a screenshot, do so as well. You'll want to file a police report later, after you go through all these steps.
3. Use antivirus or anti-malware software to clean the ransomware from the machine, but only do so if you are determined not to pay the ransom. (Otherwise, wait until you've recovered your files.) You may have to reboot into Safe Mode by pressing the power button and the S key on the keyboard at the same time.
Removing the ransomware will not decrypt your files, and it may kill your chances of getting the files back by paying the ransom. But it will let you carry out all of the following steps without the risk that the ransomware will encrypt new files or try to thwart the recovery process.
4. See if you can recover deleted files. Many forms of encrypting ransomware copy your files, encrypt the copies and then delete the originals. Fortunately, you can often recover deleted files easily with tools such as the free ShadowExplorer or the paid Data Recovery Download.
5. Figure out exactly which strain of encrypting ransomware you're dealing with. If the ransomware doesn't announce its own name, then try the Crypto Sheriff online tool or the ID Ransomware online tool. Both let you upload encrypted files and then tell you whether the encryption can be reversed. (In many instances, it can't be.)
6. See if there are decryption tools available. If you already know the name of the ransomware strain, cruise over to the list of decryption tools at the No More Ransom website and see if there's a matching decryptor. (The top two entries on the list, Rakhni and Rannoh, can decrypt multiple strains.) The list is not alphabetical, and new decryptors are added to the bottom of the list.
If you don't see what you need, try some other websites that aggregate ransomware decryptors:
https://fightransomware.com/ransomware-resources/breaking-free-list-ransomware-decryption-tools-keys
https://heimdalsecurity.com/blog/ransomware-decryption-tools
http://www.thewindowsclub.com/list-ransomware-decryptor-tools
https://www.watchpointdata.com/ransomware-decryptors
You could also try the individual antivirus companies' decryptor pages for brand-new tools that haven't yet migrated to the aggregated pages:
Avast: https://www.avast.com/ransomware-decryption-tools
AVG: http://www.avg.com/us-en/ransomware-decryption-tools
Bitdefender: https://www.bitdefender.com/free-virus-removal
Emsisoft: https://decrypter.emsisoft.com
Kaspersky Lab: https://noransom.kaspersky.com
McAfee:
https://www.mcafee.com/us/downloads/free-tools/shadedecrypt.aspx
https://www.mcafee.com/us/downloads/free-tools/tesladecrypt.aspx
https://www.mcafee.com/us/downloads/free-tools/wildfiredecrypt.aspx
Trend Micro: https://success.trendmicro.com/solution/1114221-downloading-and-using-the-trend-micro-ransomware-file-decryptor
7. Restore your files from a backup. If you regularly back up the affected machine, you should be able to restore the files from the backup.
However, you'll want to make sure the backup files weren't encrypted too. Plug a backup drive into another machine, or log in to one of the best cloud backup services, to check on the status of the files. (You should also make sure you have the installation media and/or license keys for all third-party applications.)
If all is good, you'll want to fully wipe the drive, do a clean installation of the operating system and then restore the files from the backup.
You could also just restore the files from the backup drive without wiping and reinstalling the OS. This might seem like less trouble, but it's not a good idea — you might leave some trace of the ransomware on the machine, even after performing a full antivirus scan.
If these methods don't work, you'll have to make a choice: pay the ransom, or give up the files.
8. If you're going to pay the ransom, negotiate first. Many ransomware notes have instructions on how to contact the criminals running the malware. If so, contact them and haggle for a lower ransom. It works more often than you'd think.
Once you agree on a set price, follow the instructions for paying. There's no guarantee that your files will actually be freed, but the more sophisticated ransomware criminals usually do live up to their word.
9. Give up on the files and reinstall the operating system. If you'd rather just cut bait, then you should do a full wipe and reinstallation of the operating system. Windows 10 lets you "factory reset" many devices, but with other operating systems, you'll have to use installation disks or USB sticks.
10. File a police report. This sounds pointless, but it's a necessary legal step if you want to file an insurance claim or a lawsuit related to your infection. It will also help authorities keep track of infection rates and spreads.
Special note for the Petya ransomware worm
The Petya ransomware worm that hit Europe hard at the end of June 2017 is unusual. Following infection, it restarts the computer and tries to overwrite a Windows hard drive's Master Boot Record. If you can stop the reboot process, you may prevent this.
If the Master Boot Record has been overwritten, you will see the ransom note below:
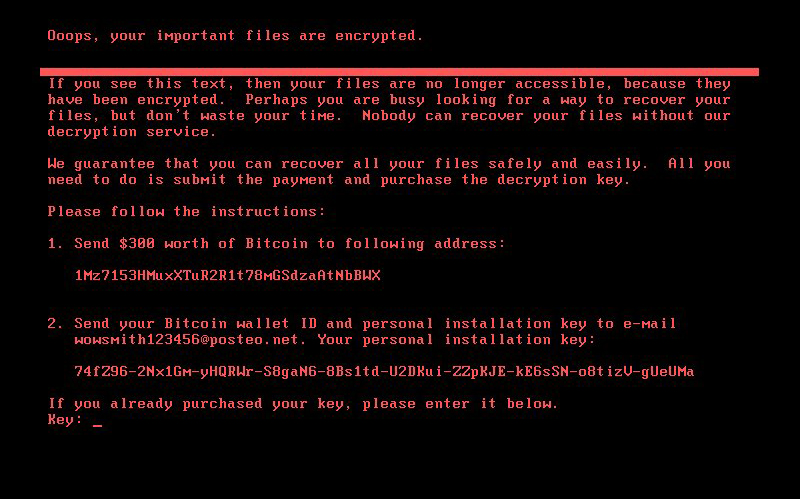
But don't despair. Creating a new Master Boot Record is not terribly difficult. If you have an installation disk for your version of Windows, you can follow the detailed instructions on this page: http://neosmart.net/wiki/fix-mbr/ . If not, then take your computer to any computer-repair shop and a technician will be able to create a new Master Boot Record in a few minutes.
Petya has a backup module that encrypts files if wiping the Master Boot Record does not succeed. If that has happened to your machine, then follow the regular instructions for handling encrypting ransomware.
Whatever you do, don't bother trying to pay the Petya worm's ransom. The malware is written so that encrypted data is unrecoverable, and the sole contact email address given on the malware's ransom screen has been disabled by the associated email service provider.
How to handle screen-locking ransomware
Screen-locking ransomware isn't as prevalent as it was a few years ago, but it still crops up from time to time. Follow these steps to remove it.
1. Disconnect your machine from any others, and from any external drives. If you're on a network, go offline. You don't want the ransomware to spread to other devices on your local network.
2. Use a smartphone or a camera to take a photograph of the ransom note presented on your screen. If you can take a screenshot, do so as well. You'll want to file a police report later, after you go through all these steps.
MORE: How to Protect Yourself from WannaCry Ransomware
3. Reboot your computer in Safe Mode by pressing the power button and the S key on the keyboard at the same time. When the computer restarts, run antivirus software to remove the ransomware.
4. Try System Restore if Safe Mode doesn't work. Most Windows machines let you roll back the state of the computer to the last known good state.
In Windows 7, restart your PC while tapping the F8 key to get to the Advanced Boot Options menu. Choose Repair Your Computer, log on with your password, and select System Restore.
In Windows 8, 8.1 or 10, restart your PC while holding down the Shift key to get to the recovery screen. Select Troubleshoot, then Advanced Options, then System Restore.
If you can't reach the recovery screens but you have the installation disk or USB stick for that version of Windows, reboot from that and select Repair Your Computer instead of installing the operating system.
5. Run antivirus software one more time to clean out your system.
6. File a police report. This sounds pointless, but it's a necessary legal step if you want to file an insurance claim or a lawsuit related to your infection. It will also help authorities keep track of infection rates and spreads.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
nirmalkant Excellent suggestion. Really impressed to read the entire blog because it covered almost everything that one should do when they get victimized by an ransomware. But i have one thing to mention that Petya isn't a ransomware as Matt Suiche did analysis and described in his blog on medium - https://blog.comae.io/petya-2017-is-a-wiper-not-a-ransomware-9ea1d8961d3b. Besides, the ransomware attacks keep increasing and I think the number would be double compared to 2016 so far. We all have witnessed Wannacry, the major havoc. Being small business owner we never knew about such thing until it came to picture early this year. I read couple of articles about it one really helped me gaining knowledge about it is http://gotowebsecurity.com/know-everything-ransomware/ which described everything in detail like you did. It also suggest prevention. Few people are writing for cause. Its good to read out and get some knowledge out of it.Reply
 Club Benefits
Club Benefits





