Another Dangerous App Found on OnePlus Phones
Another possibly risky app was found on OnePlus phones. This one lets you log the user's Wi-Fi, Bluetooth and GPS history.
UPDATED 1:40 p.m. EST Nov. 15 with further information and a statement from Qualcomm.
The security researcher who found a hidden backdoor in OnePlus phones earlier this week is back with more bad news for the Chinese handset maker.

"Hi @Oneplus! Remember me?" tweeted the researcher, who goes by the pseudonym "Elliot Alderson" online, earlier today (Nov. 15). "Let's talk about another debug app you left in your device. OnePlusLogKit is a system application which allow you to do a multitude of things: get wifi logs, nfc logs, gps logs."
"Elliot Alderson" — whom other sites now identify as a Frenchman named Robert Baptiste, but we can't confirm that — warns that OnePlusLogKit can be abused to record a user's Wi-Fi, Bluetooth and GPS histories.
However, the attacker would need access to the phone to both turn on the logging function (it's disabled by default) and to collect the logged information some time afterward (although an app reading data from the "SD card" storage area can do the latter as well).
What You Should Do
To prevent such badness from happening to your OnePlus phone, enable a screen-lock PIN (but not a pattern lock) and don't let strangers handle the device. We'd normally tell you to install and run Android antivirus software (which you should do anyway), but it wouldn't stop this kind of attack, which uses the phone's built-in features.
MORE: Best Android Antivirus Software
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Like the EngineerMode app that "Elliot Alderson" earlier found, OnePlusLogKit is accessible by dialing a special shortcode, in this case "*#800#". In fact, it seems to be another feature of EngineerMode itself.
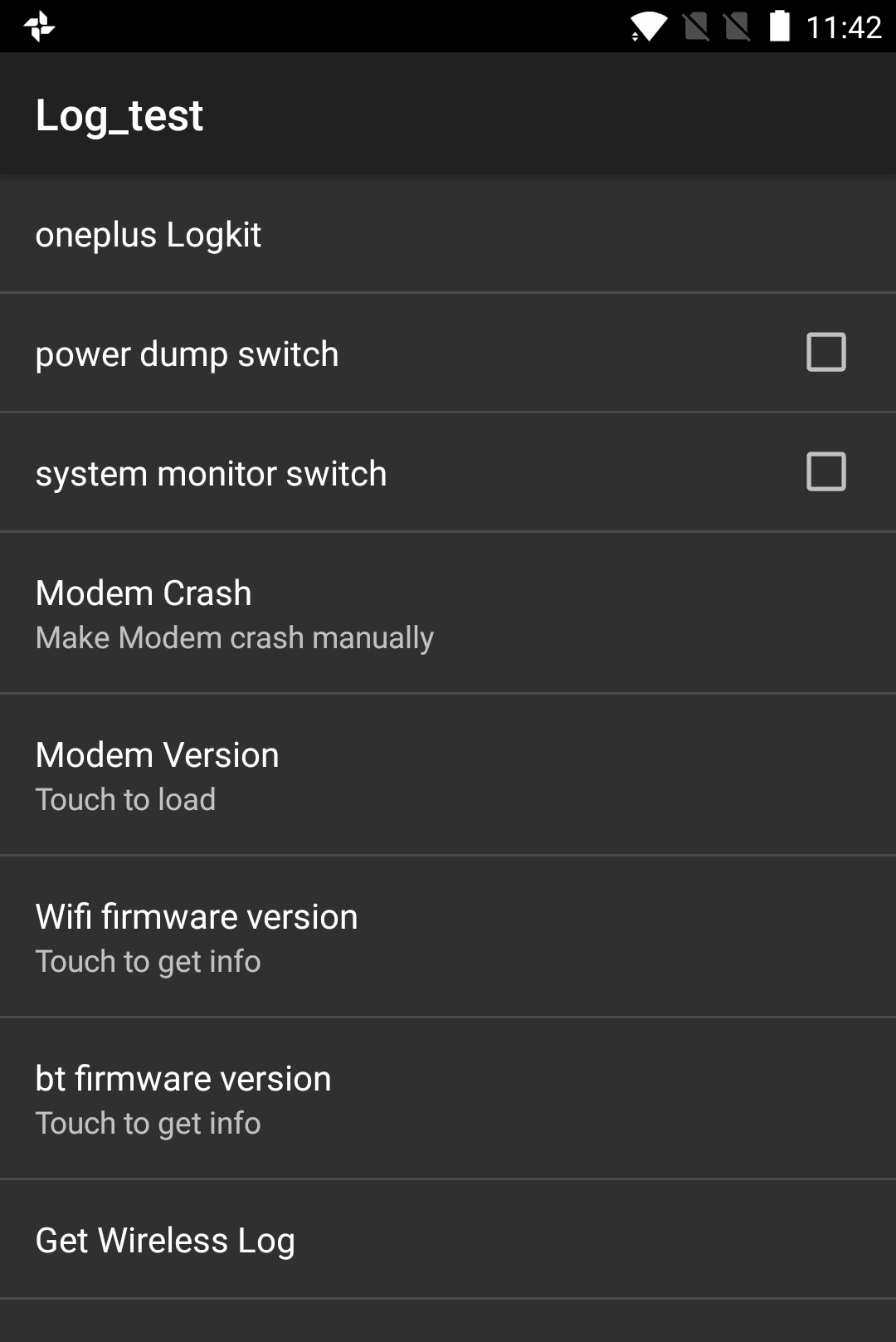
We got hold of a OnePlus 5 and dialed all the shortcodes from "*#800#" through "*#809" and found lots of fun stuff along the way, including a screen test that cycled through various colors and patterns, detailed information on all Wi-Fi networks in range, and something called "aging mode." There's even a special code ("*#801#") to turn EngineerMode on and off (although it seems to have no effect).
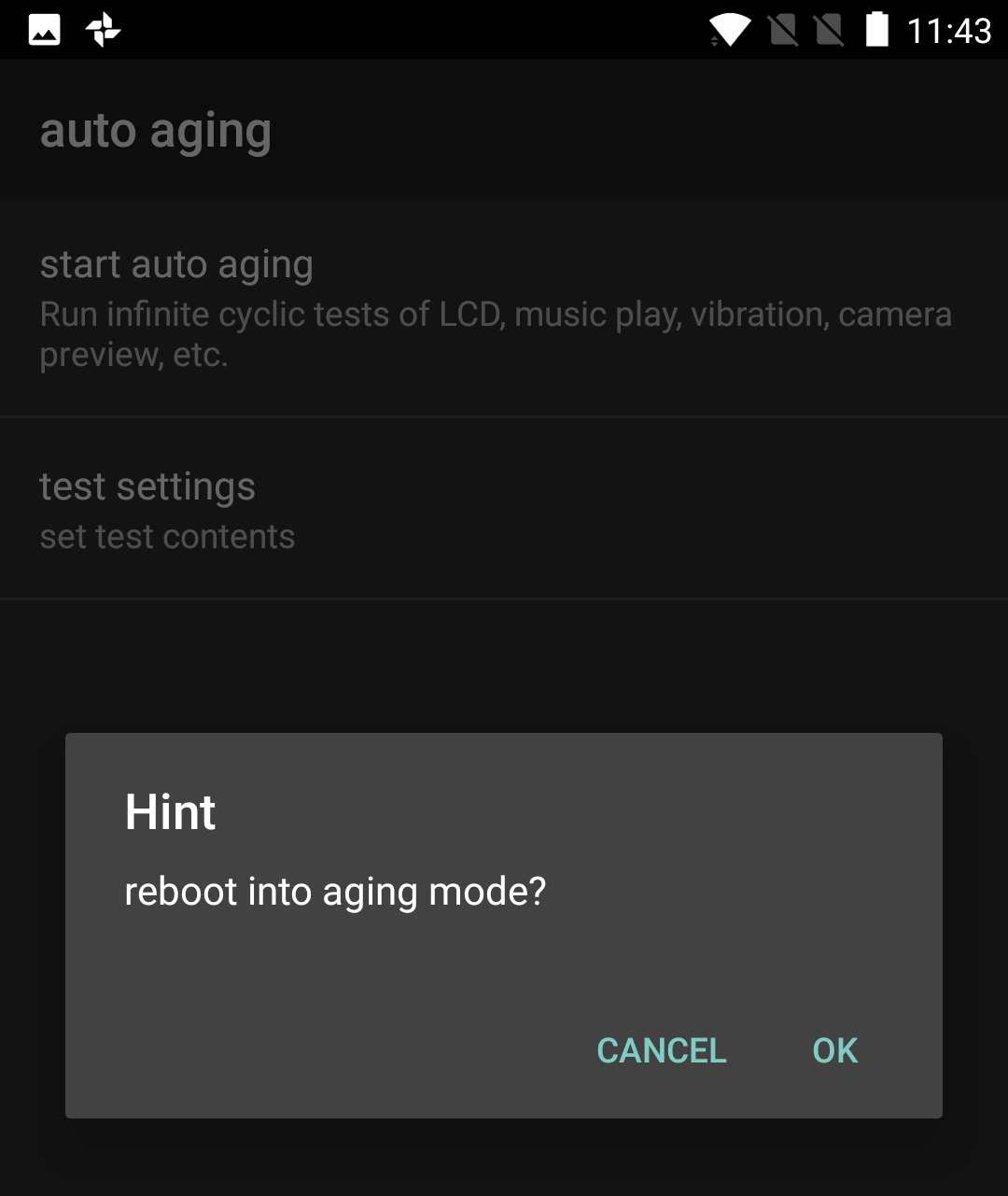
None of this stuff — which all appears to be for the use of factory workers to test for possible problems before units are shipped out to customers — is meant to be left on the phones. But to be honest, none of these debugging apps seem to be fundamentally different from common Windows diagnostic tools that anyone can use on their PCs.
Speaking for myself, I like being able to drill into my Android phone's innards to see what's going on behind the scenes. I realize that these debugging apps increase the risk that someone could be able to pwn my phone if they got hold of it and got past my PIN code or fingerprint — but as security experts like to repeat, physical access generally means game over anyway.
As he did with the EngineerMode app, "Elliot Alderson" pointed out that the real danger lies when an attacker puts the phone into Android Device Bridge (ADB) mode and connects it to a PC via a USB cable to really get into the handset. (UPDATE: Actually you don't need ADB mode with today's issue. See below.)
EngineerMode and OnePlusLogKit give even more information about the phone than you'd normally be able to get even with ADB. The former even lets you root a OnePlus phone without unlocking the bootloader, which is a security no-no.
But, again, if an attacker has your phone in ADB mode and is connecting it to a PC, you've got many more problems on your hands already.
What's the Impact
What this issue really points to is a certain sloppiness on OnePlus' part. The EngineerMode app has been found on all phones running OnePlus' custom Android fork OxygenOS, which was introduced in March 2015 after OnePlus got dumped by the maker of its previous Android fork, CyanogenOS. It's kind of unbelievable that OnePlus hadn't noticed.
We've contacted OnePlus for a comment on this new finding, and will update the story when we hear back from the phone maker.
None of these apps appear to be on OnePlus One phones running CyanogenOS. (We've seen reports that other makes of Android handsets have EngineerMode as well, but we haven't seen that ourselves.)
In an official OnePlus blog posting yesterday (Nov. 14), a developer of OxygenOS promised that EngineerMode would soon be removed by an over-the-air software update. That's ultimately best for all concerned, but I'm going to be a bit sad to see it go.
UPDATE: "Elliott Alderson" reached out to us and pointed out that ADB is not needed to enable or access any of the features of the OnePlusLogKit app. We confirmed this by enabling the logging mode (which requires a reboot) and finding the log files in File Manager -->Storage --> Internal storage --> oem_log. The log files can be viewed in a browser or the built-in HTML viewer app.
At the same time, we received this statement from Qualcomm, maker of the Snapdragon chips that power OnePlus phones, regarding EngineerMode:
"After an in-depth investigation, we have determined that the EngineerMode app in question was not authored by Qualcomm. Although remnants of some Qualcomm source code is evident, we believe that others built upon a past, similarly named Qualcomm testing app that was limited to displaying device information. EngineerMode no longer resembles the original code we provided."
Screenshots credit: Paul Wagenseil/Tom's Guide.
Best Android Antivirus Software

You'll have to pay $15 per year for Bitdefender Mobile Security, but its excellent malware protection and intuitive user interface make it well worth paying for.

Norton Mobile Security may seem pricey, but its excellent protection, multidevice license and unique privacy features make it a worthwhile investment.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

