iPhone users under threat from new ‘reset password’ attack — how to stay safe
Don’t fall for this advanced phishing attack or you might be locked out of your iPhone for good
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
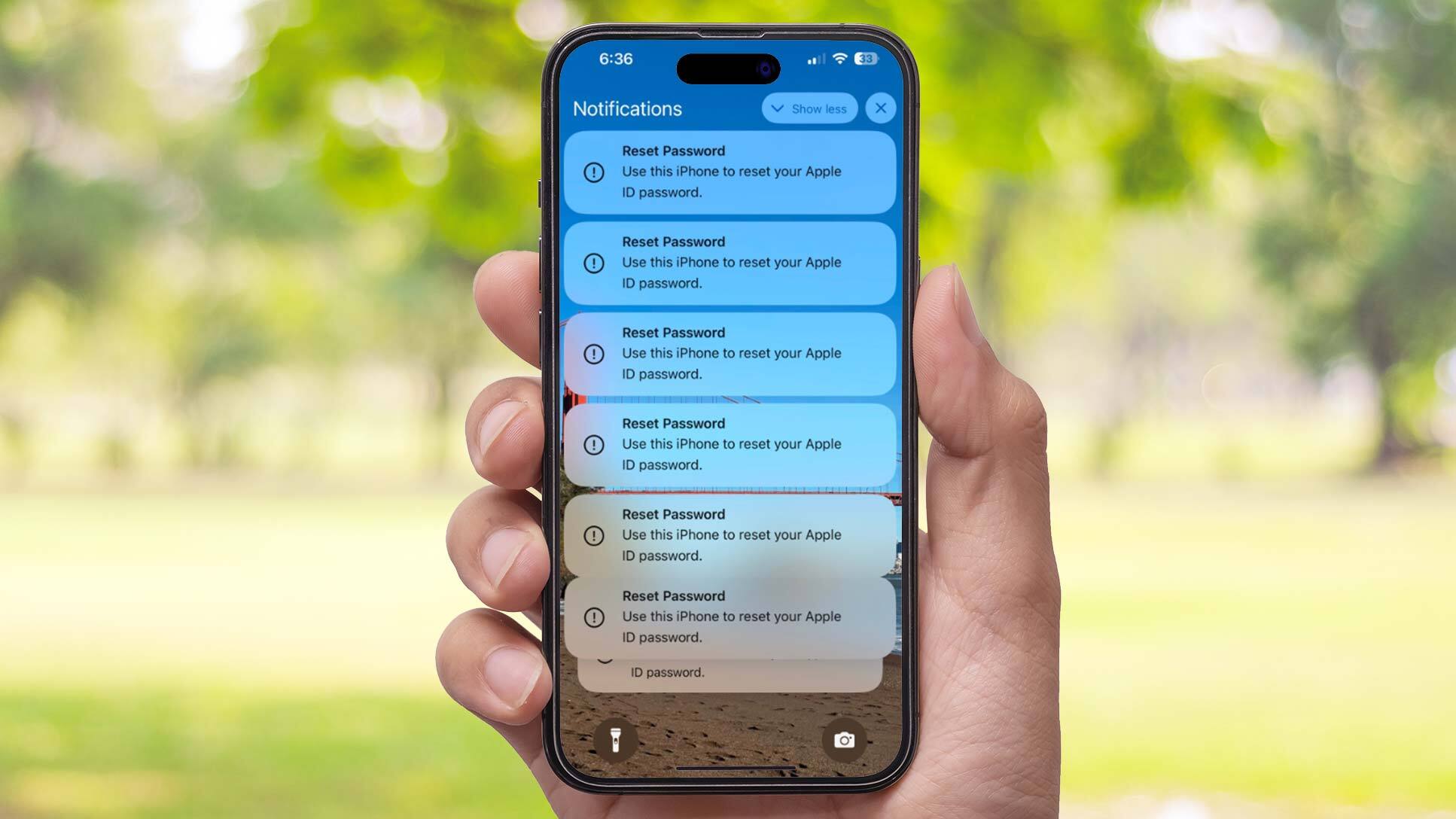
Hackers have figured out a way to exploit what seems to be a bug in Apple’s password reset feature in a new scam that can lock you out of your iPhone if you’re not careful.
As reported by Krebs on Security, this attack starts with a single Reset Password notification on one the best iPhones and is then followed by dozens of similar prompts. What makes this attack particularly annoying is the fact that targeted users will need to respond with “Don’t Allow” to each individual prompt.
If they don’t, these notifications won’t go away which essentially renders your iPhone useless. Another thing to be worried about is that some victims may accidentally hit the “Allow” button instead of the “Don’t Allow” one. If this happens, the hackers behind this attack would have complete control over your Apple account after resetting the password.
If you own multiple Apple devices, this attack becomes even more annoying as these prompts appear on all of them. For instance, a potential victim named Ken who spoke to Krebs on Security said that these prompts appeared on his Apple Watch and he had to scroll down to be able to hit the “Don’t Allow” button.
Here’s everything you need to know about this new reset password attack along with some steps you can take to stay safe.
From push bombing to phone phishing
In a post on X, entrepreneur Parth Patel detailed his own first-person account of the attack and he also included screenshots. Patel explained that he and other startup founders were being “targeted by the same group/attack” which led him to make the thread in the first place.
This kind of attack is known as “push bombing” or “MFA fatigue” as the cybercriminals behind it are abusing either a feature or weakness in a company’s multi-factor authentication (MFA) system.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
As Patel is fully invested in the Apple ecosystem, he started seeing these password reset notifications on his watch, laptop and phone. The worst part is that he couldn’t do anything else on his phone until he manually went and dismissed all of these notifications one after the other.
Another big concern is that some iPhone users may just tap “Allow” just to be able to use their devices. However, doing so would give the hackers behind this attack complete access to your Apple account and they would then be locked out of it.
While Patel thought the attack was over after dismissing dozens of password reset notifications, the hackers behind this campaign had another trick up their sleeves. He got a phone call that said it was from Apple Support that used the number 1-800-275-2273 which is the iPhone maker’s actual customer support line.
As a high-value target though, Patel was super suspicious when he picked up the phone. He then asked the person on the other line to verify some information about him and much to his surprise and after some “aggressive typing” on their end, they were able to do so. The one thing they couldn’t confirm though was Patel’s real name which was a clear giveaway that he was speaking to hackers and not a customer support representative from Apple.
The attackers most likely got Patel’s information from a people-search website as the name they provided was one that he only had seen on the site PeopleDataLabs. This is why it’s always a good idea to limit how much of your personal information is available online.
How to stay safe from advanced phishing attacks

While we don’t know yet whether or not this password reset attack was possible due to a bug in Apple’s password reset feature, it very well could be. Tom’s Guide has reached out to Apple and the company did provide some guidance on how iPhone users can protect themselves form this and similar attacks.
For starters, the iPhone maker has a useful support page with everything you need to know about dealing with phishing and other scams. In this guide, Apple recommends that you report any phishing attempts you discover to the company directly at its reportphishing@apple.com email address. Likewise, in a statement, a company spokesperson also recommended that users who have received a scam phone call like the one detailed above report these occurrences on the FTC's website.
If you do happen to be targeted by this attack, it’s of the utmost importance that you don’t tap “Allow” on any of these password reset notifications. Dismissing them individually is both annoying and time consuming but not doing so will render your iPhone unusable and tapping “Allow” will give the hackers behind this campaign complete control over your Apple account.
If you do receive a phone call from anyone claiming to be from Apple Support, don’t give out any personal information. Instead, you should follow in Patel’s footsteps and have the person on the other hand confirm what information they do have on you first. However, it’s highly unlikely that Apple Support would call you out of the blue and if they did, they would never ask for your password or other personal information over the phone.
We’ll likely find out more on this password reset attack once Apple has implemented a fix but until then, keep your iPhone close and make sure you know exactly what you’re tapping on if you receive a password reset notification.
More from Tom's Guide
- Unpatchable vulnerability discovered in Apple M1, M2 and M3 chips
- FTC just issued warning over this scam stealing thousands from Americans
- Hackers are using these Android apps on the Play store to stage attacks

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
 Club Benefits
Club Benefits










