Don't Be Like Jack — Make Sure Your Twitter Account Isn't Hijacked
Securing your Twitter account is so simple even a CEO should be able to do it

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
Twitter CEO Jack Dorsey appeared to have his own Twitter account hijacked today (Aug. 30) — but all may not have been what it seemed.
The account — just @jack, if you were wondering — starting sending out stupid, racist stuff and shout-outs to random friends about 3:45 p.m. ET. Basically, the tweets was what you'd post if you were a bored sixth-grader who wanted to shock people.
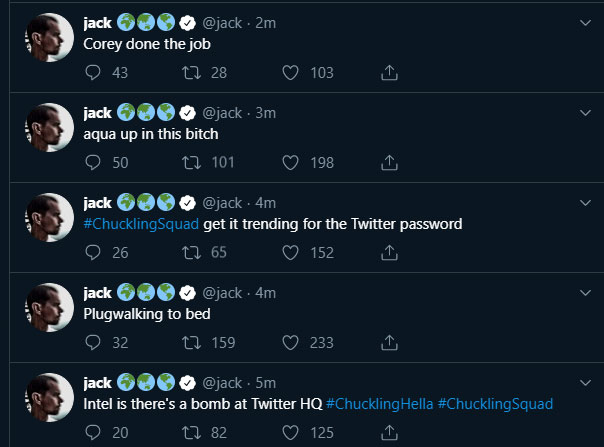
The posts were deleted within about 20 minutes, but the real question was: How did the CEO of Twitter get his Twitter account hacked?
It turned out it may not have been hacked at all. Some users saw in their own feeds that the tweets had been sent via a service called Cloudhopper, one of dozens of Twitter-feed managers that sprang up a decade ago when Twitter surged in popularity and there wasn't an easy way to manage your feed in Twitter itself.
.@jack’s hacked tweets are being posted from an app called Cloudhopper, which is apparently an app Twitter acquired previously that had something to do with SMS. So his account appears not breached - but rather Jack’s account is still hooked up to an old service that got hacked. pic.twitter.com/V3U5rJXrDPAugust 30, 2019
Cloudhopper specialized in tweeting from phones via SMS, and Twitter itself bought Cloudhopper in 2010, just as it bought TweetDeck, the best-known Twitter manager, a year later.
MORE: The One Twitter Trick Everyone Needs to Know
It seems that Jack Dorsey had tied his Twitter account to Cloudhopper -- and then apparently forgot about it. Someone apparently hacked into Cloudhopper, not Twitter, and started posting from Dorsey's Cloudhopper interface.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
We're not going to go into how Cloudhopper got compromised. There might be half a dozen different ways it could have been.
How to revoke access to old Twitter apps
But here's how to make sure a forgotten application or service with hooks into your Twitter account doesn't make you look like a 12-year-old Nazi.
- Log into your Twitter account (you're probably logged in permanently, but anyway).
- Go to https://twitter.com/settings/applications
- Take a look at the apps that have access to your Twitter account. Didn't know you had that many, right?
- Click on each one you no longer use, or don't even remember existed.
- Click on Revoke access -- it's in red.
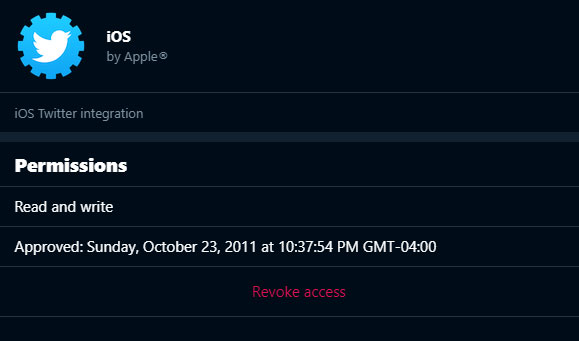
Now you're done. But before you go, nanny wants to remind you to ...
- Use a strong, unique password for your Twitter account. "Unique" means don't use it anywhere else, honey.
- Enable two-factor authentication (2FA) on your Twitter account. You can do that at https://twitter.com/settings/account/login_verification.
When it comes to two-factor authentication methods, text message is easiest but least secure. Mobile authenticator apps are almost as easy, but much more secure, so go with that. If you have a physical security key, that's even better.
UPDATE: Later Friday evening, Twitter posted a new development in @Jack-gate:
The phone number associated with the account was compromised due to a security oversight by the mobile provider. This allowed an unauthorized person to compose and send tweets via text message from the phone number. That issue is now resolved.August 31, 2019
Two possibilities can be inferred from this tweet. Jack Dorsey may have been SIM swapped, which would be very serious indeed. Or some kids got his mobile carrier (said by various Twitter users to be AT&T) to cough up his phone number, which the kids then "spoofed" to send tweets via SMS. That would be less serious.
Let's go through these quickly.
What is SIM swapping?
SIM swapping, aka SIM jacking or port-out scams, can have horrifying results. Basically, an attacker sweet-talks a support representative at your mobile carrier to transfer your phone number to a different phone or SIM card controlled by the attacker.
Now all calls and texts sent to that number go to the attacker instead, which means that SMS-based two-factor authentication codes go to the attacker, not you. If your phone number is used by an account to confirm your identity in case you need to reset your password, then the attacker can completely take over that account.
This is something that mobile carriers are not prepared to handle. They did not expect that the numbers they handed out to customers, and which were meant to be portable to new handsets by design, would be used by other companies as a means to establish ironclad verification.
Millions of dollars in cryptocurrency have been lost to SIM swappers who targeted high-profile investors, and ordinary people have had thousands of dollars of purchases racked up on their Apple Pay accounts due to SIM swapping.
We've got a couple of articles on how to avoid becoming a victim of SIM swapping, but one chief tip is to stop using SMS codes in two-factor authentication to contain the damage. As noted above, use authenticator apps or physical security keys instead.
Tweeting without Twitter
The hijackers of Dorsey's Twitter feed didn't seem to get total control of his account, or try to grab control of any other accounts. It may be that they did get his number transferred to their phone, but couldn't, or didn't bother to, reset his account password.
But they may not have needed to get the SIM swapped at all. Twitter lets you tweet via text message if you have a mobile phone number linked to your Twitter account. All you have to do is text to "40404" and write something -- give it a try. (This was useful when smartphones weren't so common.)
Mobile phone numbers are pretty easy to "spoof" in outgoing calls and texts with the right tools, and there are plenty of those tools available. Some of them are even legal.
So if these attackers had Dorsey's mobile number, they could have tweeted as him directly from SMS. That might explain why they use Cloudhopper, which was designed to make SMS tweeting easier.
It might also explain why Twitter's statement specified that the "security oversight" allowed the attackers to "compose and send tweets via text message," but not compose and send tweets from the actual Twitter app or website.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
 Club Benefits
Club Benefits










