Microsoft's agentic AI roadmap had a flaw that let hackers take over browsers — here's what to know and how to stay safe
Microsoft’s Agentic Web dream derailed by security flaw

Microsoft is quickly heading towards AI agentic browsing — that much is obvious with Edge’s AI makeover and an open project called NLWeb that can be used to give any website AI power.
But while this all sounds good on paper, it does open the door to a whole lot of security risks, and the company’s agentic aspirations have already been hit by a flaw that is concerningly simple.
Fortunately, it has been patched out, but it does start a bigger conversation we need to have about staying safe while agentic browsing. Let’s get into it.
So what happened?
NLWeb is envisioned as “HTML for the Agentic Web.” Announced back at Build 2025, this is the framework for AI browsing on your behalf, but researchers Aonan Guan and Lei Wang found what is called a "path traversal vulnerability".
This is a pretty standard security oversight that hackers can take advantage of by having an agentic AI visit a specially-made URL that can grant the attacker access to sensitive files like system configuration files and API keys.
What can be done with this information is what can amount to stealing your agent’s brain. Attackers at this point can get to the core functions of your AI agent and do a wide-ranging amount of things like look at/interact with emails on your behalf, or even get into your finances.
The flaw was found and reported to Microsoft on May 28, 2025, and the company patched it out on July 1, 2025 by updating the open-source repository. It was a simple exposure that had huge problematic potential.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
“This issue was responsibly reported and we have updated the open-source repository,” Microsoft spokesperson Ben Hope told The Verge. “Microsoft does not use the impacted code in any of our products. Customers using the repository are automatically protected.”
How to stay safe while agentic browsing
We’ve seen a significant shift towards agentic browsing over the last 12 months — spearheaded by the likes of OpenAI Operator, Opera launching the world’s first on-device agentic AI browser, and Rabbit R1’s LAM Playground.
This serious flaw may have already been patched out by Microsoft, but it’s clear that this won’t be the last security issue we come across. For example, there’s the Model Context Protocol (MCP), which is an open standard launched by Anthropic to allow AI assistants to interact with tools and services on your behalf.
Sounds good on paper, but researchers have already identified the risks of account takeover and token theft: when a hacker gains access to personal authentication tokens and essentially gets the keys to your kingdom.
So it’s clear you need to be extra careful in the agentic era. Here are some key steps you can take:
Be cautious with OAuth permissions
If your AI agent is asking to connect to a service like Gmail or Google Drive, read the permissions carefully. Don’t approve full access if only read access is needed, so avoid clicking “allow all” without thinking about it. On top of that, if you want an additional layer of security, use a separate account. That way you can see what the agentic AI will be able to do without putting your sensitive information on the line.
Don’t 100% trust any agent
Think of any agent as a teenager you just gave the car keys to — effective most of the time, but not averse to mistakes (my battered Vauxhall Corsa can attest to this). By that, I mean check the agent you use is from a reputable company to start with. That means don’t install any browser extensions that claim to “autonomously browse the web.” And whatever you’re using, don’t let them auto-fill forms, send emails or make purchases unless you explicitly tell them to.
Sanitize your browsing and app permissions
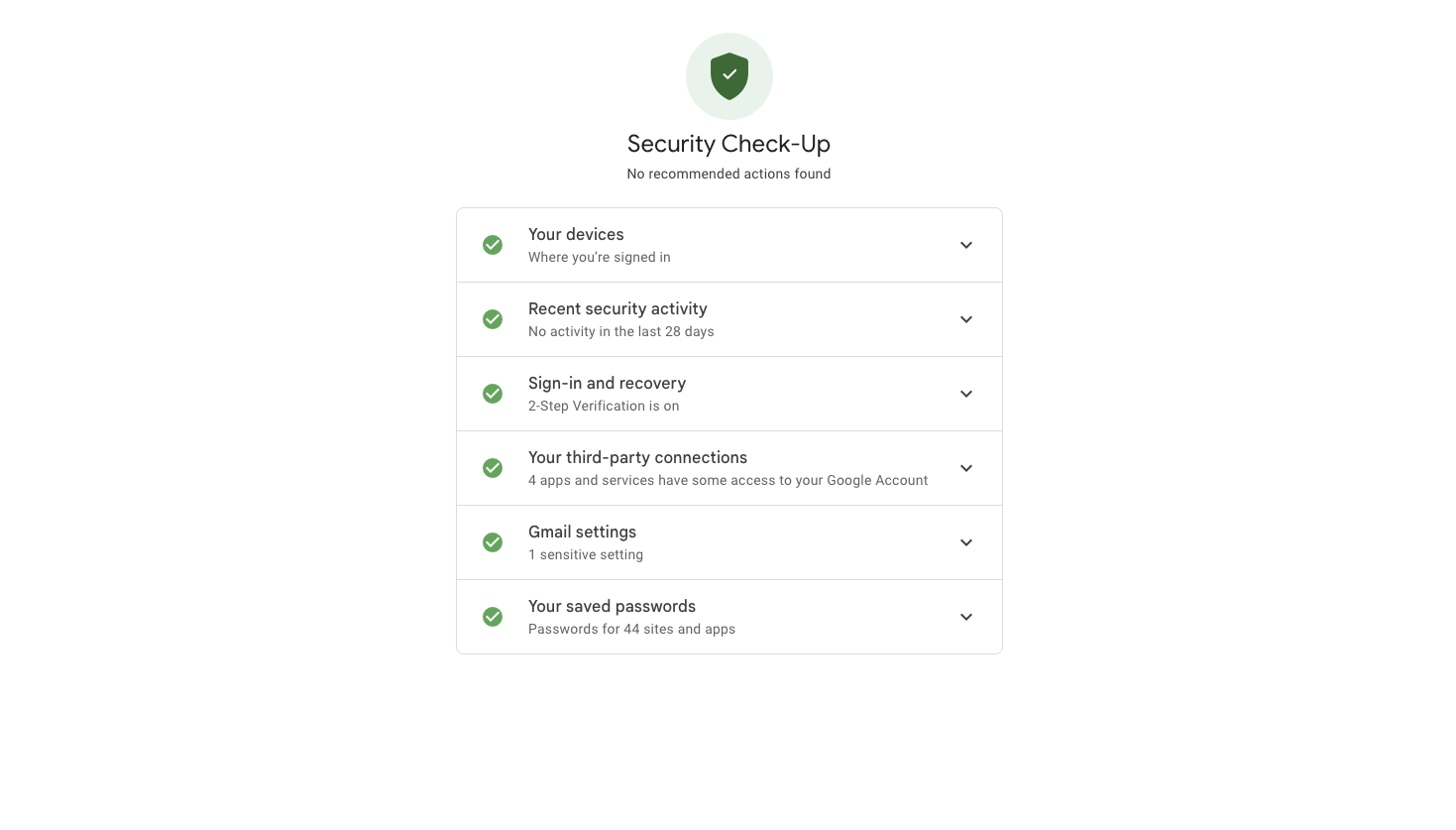
For Chrome users, head over to Google Security Checkup and get rid of any third-party services that have access to your account. This will limit any potential exposures, as much as turning off autofill or password auto-saving will too. And for an additional layer of security, use agentic web tools in incognito/private windows to limit cookie or token leakage.
Follow Tom's Guide on Google News to get our up-to-date news, how-tos, and reviews in your feeds. Make sure to click the Follow button.
More from Tom's Guide
- OpenAI ChatGPT-5 live blog: Countdown and all the big news as it happens
- This Windows 11 feature drove me nuts. Microsoft's finally fixing it — sort of
- I tested ChatGPT vs Gemini 2.5 Pro with these 3 prompts - and it shows what GPT-5 needs to do

Jason brings a decade of tech and gaming journalism experience to his role as a Managing Editor of Computing at Tom's Guide. He has previously written for Laptop Mag, Tom's Hardware, Kotaku, Stuff and BBC Science Focus. In his spare time, you'll find Jason looking for good dogs to pet or thinking about eating pizza if he isn't already.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits