Why You Should Turn Off Apple's AirDrop Right Now
Convenience may come at a cost

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
As effortless as it may be to send images to other iPhone users via AirDrop or mirror your MacBook screen on a TV using AirPlay, the Apple protocol used to enable those wireless conveyances is actually filled with security risks.
New research reveals that Apple Wireless Direct Link (AWDL), the AirDrop/AirPlay networking protocol installed on more than 1.2 billion Apple devices, leaves unknowing users susceptible to a number of cyberattacks.
Owners of Macs, iPhones, iPads, Apple watches, Apple TVs, and HomePods with AWDL installed are vulnerable to assailants attempting to track users, crash devices, or intercept AirDrop dispatches through man-in-the-middle (MitM) attacks, according to the research results.
Real-life attacks using AirDrop or AirPlay may not be immediately likely, but if you're worried, you should turn off the features on your Apple devices when you're not using them.
What you can do, how to disable AirDrop
Turning off AirDrop is pretty easy. Open Settings, tap General and tap AirDrop. Here, you'll get three options: Receiving Off (disable), Contacts Only and Everyone. The smart move is to selectively enable only when you're in private, safe areas, such as your home, with a 30-foot radius from bad actors.
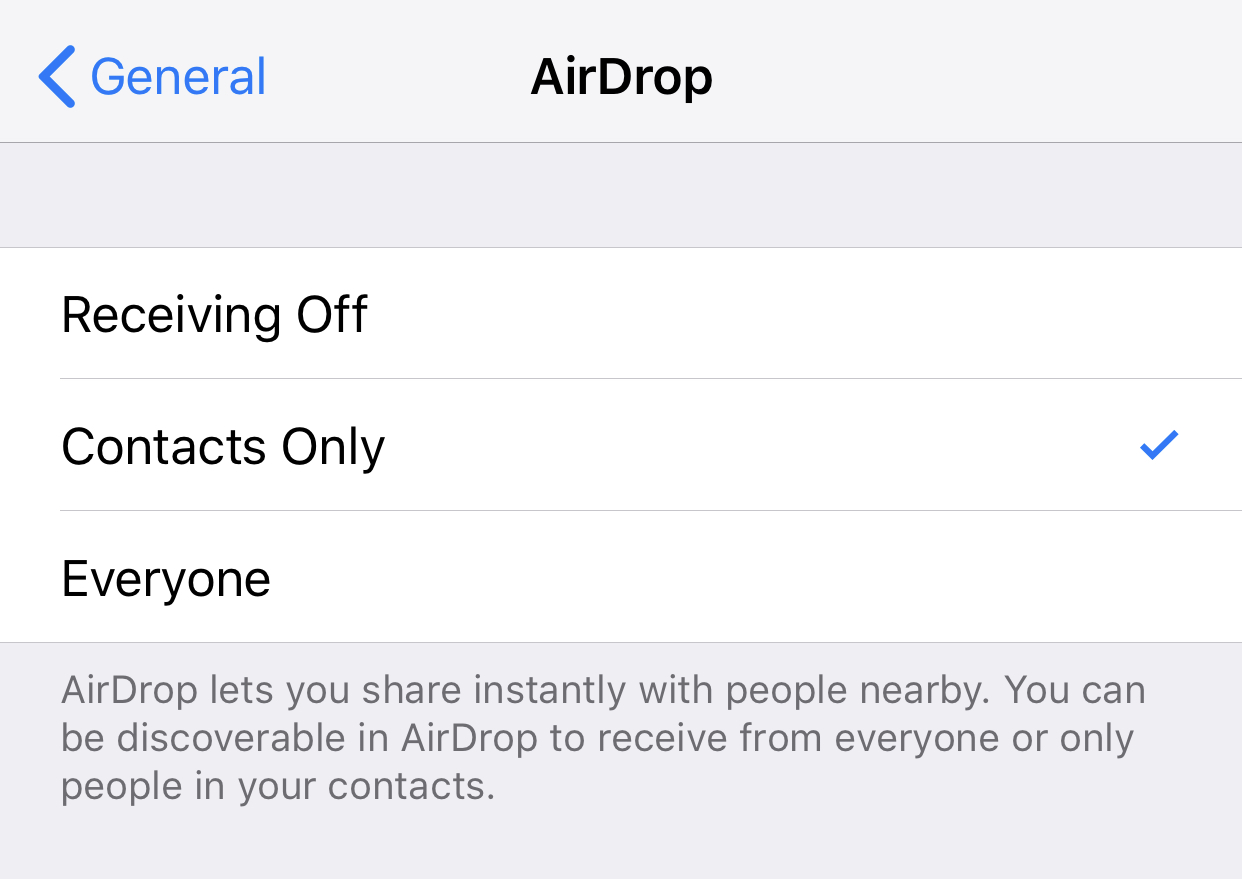
If you're confused by the technical jargon, you should understand the convenience of wireless communication like AirDrop comes with a cost. Consider sending photos and files to your friends the old-fashioned way: through text, email, or literally anything with encryption.
And before you panic, know that these researchers are seasoned security experts. Joe Schmo passing you on the street (probably) won't be able to penetrate your Apple device just for the heck of it -- yet.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
What does this mean?
MORE: Why Apple iPhones Don't Need Antivirus Software
These findings come from the Technical University of Darmstadt in Germany, where researchers sought to analyze the AWDL protocol, which Apple introduced in 2014. The full technical paper can be read here.
Five years later, Apple has yet to publish any significant details about how the networking technology included by default on all its devices works. TU Darmstadt noticed the lack of security research on AWDL and decided to take a look into the highly pervasive protocol.
"Considering the well-known rocky history of wireless protocols' security, with various flaws being repeatedly discovered in Bluetooth, WEP, WPA2, GSM, UMTS, and LTE, the lack of information regarding AWDL security is a significant concern given the increasing number of services that rely on it," the TU Darmstadt team said.
They partnered with academics from Boston's Northeastern University to reverse-engineer the protocol and test it for vulnerabilities. While Apple's ADWL contained some security features, the researchers managed to bypass them and successfully carry out staged attacks.
The researchers discovered they could intercept and modify device-to-device communication via AirDrop, permitting the injection of malicious files. They also found long-term device tracking possible, despite MAC randomization. Three denial-of-service (DoS) attacks were also completed, crashing the Apple devices tested.
Tom's Guide has reached out to Apple for comment, and we will update this story when we receive a response.
Apple might have to rebuild the technology behind AirDrop and AirPlay if it wants to protect users from these kinds of cyber attacks. While the tech giant rolled out an AWDL patch for DoS attacks in May in response to the research team's early disclosures, the overall protocol is still vulnerable to other types of attacks. The researchers say the flaws "require the redesign of some of [Apple's] services."

Kate Kozuch is the managing editor of social and video at Tom’s Guide. She writes about smartwatches, TVs, audio devices, and some cooking appliances, too. Kate appears on Fox News to talk tech trends and runs the Tom's Guide TikTok account, which you should be following if you don't already. When she’s not filming tech videos, you can find her taking up a new sport, mastering the NYT Crossword or channeling her inner celebrity chef.
 Club Benefits
Club Benefits










