iOS 12's Security Features: The Good and the Bad
Apple's iOS 12 update adds several new promising security and privacy features, though a couple might lead to further problems.
Some good news for the security-conscious iPhone user: Apple has packed in a lot of security and privacy improvements and patches into iOS 12. Now the bad news: A couple of the upgrades might lead to unintended consequences.
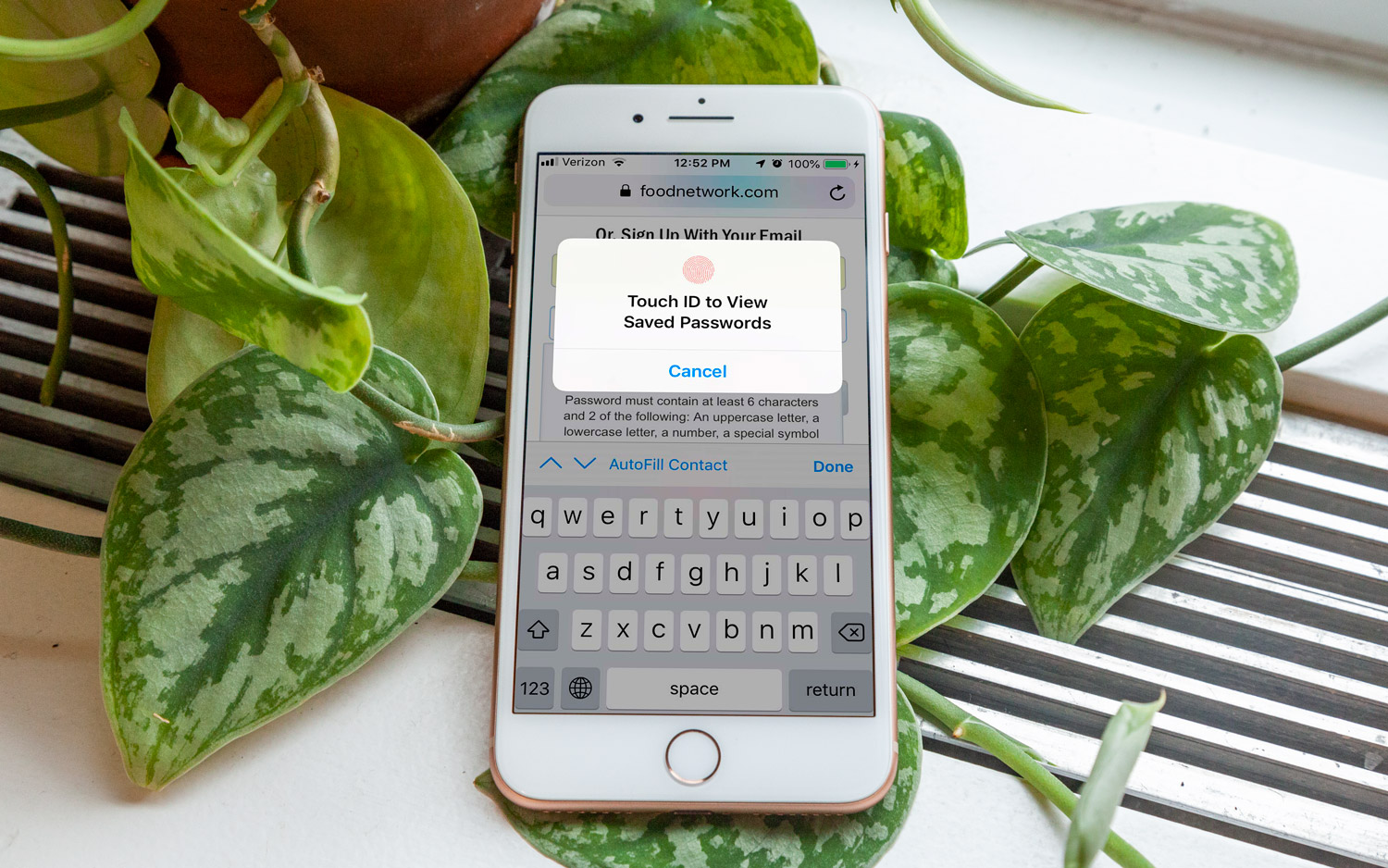
First, the good news: iOS 12 has a built-in password manager, blocks USB access to your phone if it's been locked for more than an hour, makes it easier to use two-factor authentication (2FA) and gives you the option to set automatic updates.
Now, the possibly bad news: You can AirDrop passwords to other iOS and macOS users, creating a potential opportunity for hackers to grab your passwords via Bluetooth or Wi-Fi. And if the 2FA code autofill function still works the way it did in the iOS 12 beta, it could give hackers a chance to break into your online bank account.
MORE: iOS 12 Guide: Tips, Tricks and How-Tos
Let's get the boring stuff done right away. iOS 12 fixes a number of security flaws, most of which were under the radar until now. The patched flaws include an "input validation issue" in Bluetooth; buffer and kernel flaws that let apps read restricted memory; and a browsing-history leak and an address-bar validation flaw in Safari.
iOS 12 also includes new restrictions on browser and app trackers, which should mitigate the surreptitious tracking of user location and behavior disclosed last week by third-party researchers. But there's no fix yet for the malicious-website attack disclosed over this past weekend, which freezes and sometimes reboots iPhones and Macs.
What's the Password?
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The password-management functions are undoubtedly the best security enhancement of iOS 12. The new OS will suggest complex passwords for you when you create a new account. New passwords get saved in your iCloud Keychain so that they'll work across all your Apple devices. iOS 12 also flags reused passwords so that one data breach won't compromise multiple accounts. Finally, it autofills passwords into form fields.
Best of all, these new features will work with third-party password managers, which you can use as your password manager instead of Keychain. This is a bonus if you don't exist exclusively in the Apple universe, or already use a password manager, as the third-party managers also sync with Windows, Android and often Linux.
Dashlane, LastPass and 1Password already mesh with iOS 12 in this way, and more passwords managers will soon.
Now for the touch of gray in this silver lining: iOS 12 will also let you AirDrop passwords to nearby iDevices so that, say, visitors to your home can get onto your Wi-Fi network, or your kids can log onto your Netflix account.
This sounds very convenient. It could also create an opportunity for hackers to sniff out passwords. AirDrop transmissions are encrypted, but the communicating devices don't need to be on the same Wi-Fi network or be paired over Bluetooth — they just need to each have both their Wi-Fi and Bluetooth radios on. There are ways to crack transmission encryption on Bluetooth, and Wi-Fi isn't secure at all by default; Apple's own encryption protocol sounds pretty strong, but nothing's perfect.
AirDrop is also noteworthy for letting people, accidentally or not, receive strangers' files — space sloths, gory images, nude photos — when both sender and receiver are in crowded public places.
From what we understand, the passwords themselves will be encrypted before they're sent over the already encrypted AirDrop connection, and both the sender and recipient will need to authenticate themselves using Face ID or Touch ID before a password can be shared. But it's likely that both black-hat hackers and security researchers are having a look at this feature. After all, AirDrop has had security issues before.
2FA made E-Z
A similar good news/bad news situation arises with iOS 12's autofilling of 2FA temporary codes transmitted via SMS text messages. If your online account provider — Amazon, for example, or your bank — texts you a 2FA code, iOS 12 will grab it and make it an autotype suggestion so that you won't have to commit that temporary IN code to memeory.
This is very convenient and will, we hope, get a lot more people to use 2FA, which is perhaps the single most important security enhancement available right now. (Generated 2FA codes are even better than texted ones, but that's an argument for another day.)
There's a slightly increased risk that someone will figure out a way to intercept the 2FA code as it's copied from Messages to the keyboard app, but it's worth the tradeoff if it increases the 2FA uptake rate.
But here's the potentially bad part: It's possible that the autofill suggestion might capture not only 2FA codes, but also special codes that many banks in Europe transmit during online-banking sessions, after a user has already successfully logged in.
These codes are called transaction authentication numbers (TANs), and they're generated whenever a logged-in user actively initiates a financial transaction, such as moving money between accounts or paying a bill. (There's no TAN needed for passive stuff like viewing your bank balance.)
The bank texts the TAN to the user's phone to ask the user to verify that he or she really does want this transaction to take place, and the user replies affirmatively by typing in the TAN. If the user doesn't recognize the transaction request, then he or she is told to call the bank immediately.
The problem with the 2FA autofill is that users might not realize that the suggested code is for a TAN instead of a 2FA authentication code. A crafty hacker might use that confusion to fool users into authorizing money transfers.
Because TANs aren't yet used by American banks, we haven't been able to verify if the final release of iOS 12 auto-suggests TANs as well as 2FA codes. We've asked the researcher who discovered this issue in the iOS 12 beta about it, and will update this story once we learn more.
More good stuff
The rest of the iOS security enhancements don't have any downsides that we can think of.
The USB Restricted Mode that was optional in iOS 11 is now on by default; it will prevent anyone from using a USB cable to access your iPhone's data if the phone has been screen-locked for more than one hour. (Before this, the window was an entire week.) You'll have to provide your device passcode or unlock the phone with your fingerprint (or face on devices that support Face ID) to provide USB data access.
Automatic iOS updates are now an option — you can now be sure that your iPhone always has the latest security patches. Granted, there have been a few buggy updates in the past, but that's not as much of an issue on iOS as it is in Windows. We recommend turning this feature on.
The Screen Time feature that tells you how much time you're spending on your phone can also tell you which apps your kids use, and for how long. You can also limit the amount of time your kids spend on specific apps, or on entire categories of apps.
Combined with the location-sharing feature in family Sharing, iOS 12 now offers many of the features found in third-party parental-control apps. You still can't read a child's text messages unless you know his or her iCloud password, though.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
 Club Benefits
Club Benefits





