Clubhouse for Android? Nope, just sneaky password-stealing malware
This is one Clubhouse you don't want to join
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
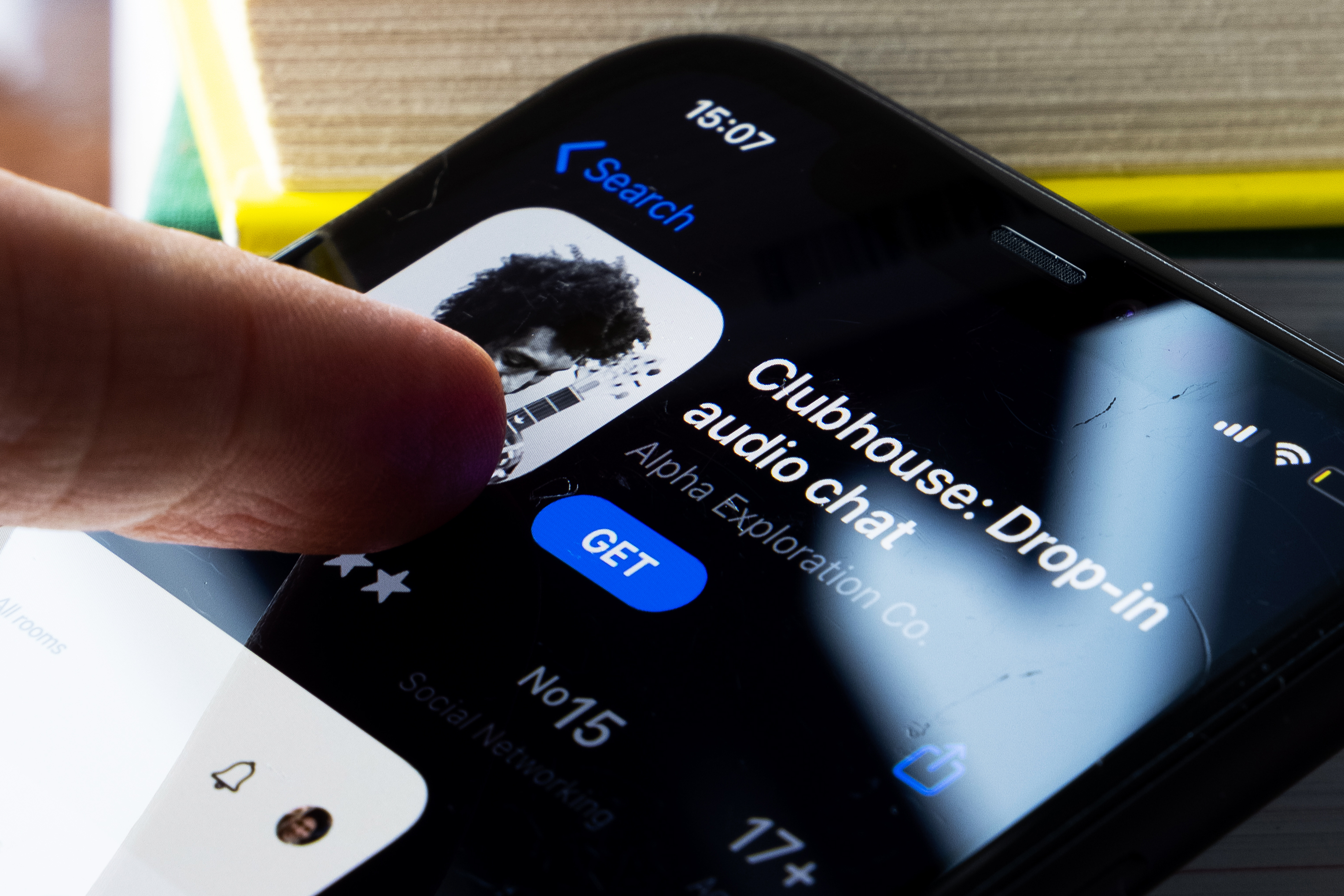
If you're pining to use Clubhouse on Android, don't be too eager as you might fall prey to this fake Clubhouse Android app that installs password-stealing malware.
Discovered by ESET and written up in a blog post yesterday, the fake Clubhouse app installs the BlackRock Android Trojan, which we first wrote about last summer.
- Clubhouse app hacked, audio reposted — what you need to know
- The best Android antivirus apps
- Plus: Samsung Galaxy Z Fold 3 colors — and a design surprise
This fraudulent app is trying to cash in on the Clubhouse craze, which has seen the 11-month-old iPhone voice-chat app skyrocket in popularity following celebrity endorsements from the likes of Elon Musk.
The fake Clubhouse app is delivered by a bogus Clubhouse website that looks exactly like the official site, ESET said.
There are only two differences: The ".com" in "joinclubhouse.com" is replaced by a different top-level-domain suffix, and the official Apple button to "Download on the App Store" is replaced by one that looks like the real Google app button, which reads "Get it on Google Play."
If you're on your Android phone and you click that fake link to the Google Play Store, an app called "Install" will download to your phone and prompt you "Enable Install." This will work only if you've given Chrome, or whichever of the best Android browsers you're using, permission to install apps.
How to avoid joining the wrong Clubhouse
To prevent being hoodwinked by this fake Clubhouse app, make sure that only Google Play can install or update software on your Android device. Go into Settings > Apps & Notifications > Special App Access > Install unknown apps and make sure no apps have this ability.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
You'll also want to be running one of the best Android antivirus apps, which will block the BlackRock Trojan from installing and find any other malware you may already have on your phone or tablet.
BlackRock mimics the login screens of hundreds of Android apps, including Amazon, eBay, Facebook, Gmail, Google Play, Hotmail, Instagram, Microsoft Outlook, Netflix, PayPal, Twitter, Uber, WhatsApp and Yahoo Mail, plus every major bank you've ever heard of. It also fakes the credit-card-entry screens of dozens of other apps.
Put your username, password or credit-card number into one of BlackRock's fake login screens, and you can kiss them goodbye.
Having two-factor authentication (2FA) activated doesn't always work, says ESET, because BlackRock can intercept text messages. That's one reason it's better to use an authenticator app or a USB security key as your "second" 2FA factor.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
 Club Benefits
Club Benefits










