Apple
Latest about Apple

AirTag 2 vs AirTag: What's the difference?
By Josh Render last updated
Apple has unveiled the next generation of Apple AirTag. The question now is if you should upgrade to this new generation.

iPhone 18 — 3 key things from the Apple earnings call that make me excited about the new iPhone
By John Velasco last updated
After hearing a lot of good news from its Q1 2026 earnings report, Apple can look ahead to the iPhone 18. Here are some key facts from the earnings call that stand out.

Apple TV just landed its own major fantasy franchise — and it could be even better than peak 'Game of Thrones'
By Martin Shore published
Apple has struck a deal to bring Brandon Sanderson's Cosmere books to life, and it could make Apple TV a must-have streaming service for fantasy fans.

Your iPhone can browse Safari at a smooth 120Hz, and this is the setting you need to change
By Sanuj Bhatia published
A hidden Safari setting lets compatible iPhones use the full 120Hz refresh rate.
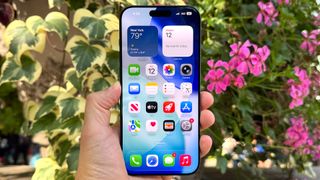
7 things your iPhone search bar can do that you probably don't know about
By Kaycee Hill published
Your iPhone search bar can do way more than you think. Here's seven hidden features to try next.

Apple warns the RAM crisis will have 'more of an impact' — what it means for iPhone and MacBook prices
By Darragh Murphy published
Apple CEO Tim Cook expects 'a bit more of an impact' in the ongoing RAM crisis, and it could affect your next iPhone and MacBook upgrade.

Apple earnings report — Tim Cook calls iPhone 17 series 'by far the most popular'
By Dave LeClair, John Velasco last updated
Apple shared its Q1 2026 earnings report, which shows record settings achievements for revenue and earnings per share.

Best iPad deals for January 2026
By Louis Ramirez last updated
The best cheap iPad deals from every retailer so you'll never have to pay full price for your iPad again.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
 Club Benefits
Club Benefits







