Spying Cell Towers May Be Spread Across U.S.
A phone-security company says it has detected nearly 20 suspicious cellular towers that could spy on phones across the country.
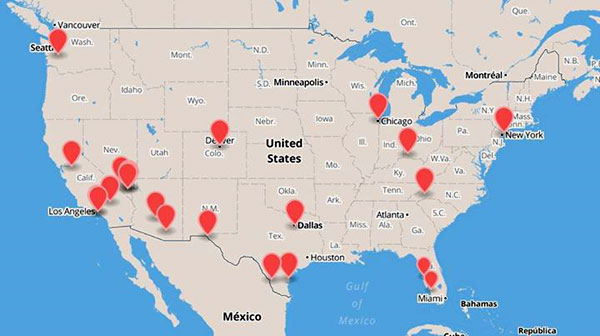
There are at least 19 bogus cellphone towers operating across the United States that could be used to spy upon, and even hijack, passing mobile phones.
So says Les Goldsmith, head of ESD America, a company that imports and sells tightly secured mobile phones that can detect "baseband" hacking attempts. Goldsmith calls fake cell towers "interceptors."
"Interceptor use in the U.S. is much higher than people had anticipated," Goldsmith told Popular Science in a piece posted online last week. "One of our customers took a road trip from Florida to North Carolina, and he found eight different interceptors on that trip."
MORE: Best Android Antivirus Software 2014
The better to spy on you with
Cellphones communicate with cellular-service towers using the baseband processor, a chip that controls some or all of the radio signals sent to and from the device. Baseband processors run their own operating systems and are made by a handful of companies that zealously protect their trade secrets; not even phone makers know exactly how the baseband processors work.
Mobile phones seek out and establish contact with the nearest compatible cell tower, or at least the one with the strongest signal, jumping from one "cell" to another as they move around. However, while each phone has to prove its authenticity to each tower (to verify that the cellular service has been paid for), towers are under no obligation to verify their own identities to phones.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
That's where bogus towers come into play. Also known as "IMSI catchers," they're used by law enforcement in many countries, including the U.S., to collect the IMSI identification numbers of the SIM cards on GSM and LTE phones. Even without any phone calls or texts sent or received, a phone's IMSI will be logged by every nearby cell tower, real or fake.
Most cellular communications between a phone and a tower are encrypted, but the encryption standard has to be agreed upon during initial contact. A tower can demand that weak encryption, or no encryption at all, be used. Signal protocols — various iterations of 4G, 3G or 2G — are also negotiated.
An ordinary cellphone indicates when it moves from 4G to 3G, but it won't display which form of encryption is being used. The user will have no idea if calls, texts or data are being transmitted "in the clear" for anyone to hear or see.
MORE: How to Secure Your iPhone Now
In this way, a bogus tower with a signal stronger than other nearby towers can force decryption upon targeted devices. High-end bogus towers can relay outgoing communications to genuine cellular networks, and thereby stage man-in-the-middle attacks; the targeted user can place calls and send texts, usually with no indication that he or she is being monitored.
Bogus towers can even be used to deliver malware by attacking the baseband processor, as several proof-of-concept hacks demonstrated at security conferences have shown. It's possible that the much-rumored, but never proven, ability of the National Security Agency to use a phone that's been "turned off" as a microphone depends on baseband malware.
Catching the catchers
The CryptoPhone 500 sold by Goldsmith's company can tell when an IMSI catcher is in operation. A Samsung Galaxy S3 running a heavily modified version of Android licensed from the German company GSMK, the phone has a "baseband firewall" that monitors everything going in and out of the baseband processor.
If GSM encryption is downgraded or deactivated, or the baseband sees a lot of traffic without corresponding activity in the "userland" operating system (in this case, Android), the screen alerts the user that an IMSI catcher may be in operation.
Using data provided from clients who use CryptoPhone 500s, Goldsmith's company has created a map of the U.S. showing locations of 19 IMSI catchers. Most are in California and the Southwest, but Chicago and New York have one each.
"A lot of these interceptors are right on top of U.S. military bases," Goldsmith told Popular Science. "So we begin to wonder — are some of them U.S. government interceptors? Or are some of them Chinese interceptors?"
It's possible that they're neither. One unnamed American expert who spoke to the British tech-news site The Register put forward a less thrilling explanation.
"It is most probable that these sites are to allow coverage to groups of people that are not in a conventional coverage area (such as paying customers in a casino, or military groups)," the source said. "I would suggest that university campus areas may do the same."
Do it yourself
If you want the ability to detect IMSI catchers with your own phone, you're in luck, because it's gotten a bit easier. Goldsmith won't disclose how much the CryptoPhone 500 costs, but media reports have put the U.S. retail price at about $3,500.
If you already have your own Samsung Galaxy S3 and know how to root it, however, you can install the recently released IMSI-catching app Darshak, available for free in the Google Play store.
- 12 PC Security Mistakes You're Probably Making
- California Kill-Switch Law Based on Garbage Research
- Best Mobile Privacy and Security Apps
Follow Paul Wagenseil at @snd_wagenseil. Follow Tom's Guide at @tomsguide, on Facebook and on Google+.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
skit75 "It is most probable that these sites are to allow coverage to groups of people that are not in a conventional coverage area (such as paying customers in a casino, or military groups)," the source said. "I would suggest that university campus areas may do the same."Reply
Sounds like these fake or spying cell towers are actually something else to me. This seems more plausible than rogue spy cell towers that happen to be located either next to a military base or a college campus. How would that go so un-noticed if they are wearing such black hats. -
jakjawagon Reply"It is most probable that these sites are to allow coverage to groups of people that are not in a conventional coverage area (such as paying customers in a casino, or military groups)," the source said. "I would suggest that university campus areas may do the same."
This doesn't explain why they would downgrade or disable encryption. I'm not convinced.
 Club Benefits
Club Benefits





