StrandHogg flaw lets hackers hijack nearly any Android phone
This is serious.

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
UPDATED with comment from Google.
There's a new Android security flaw that affects all versions of Android, including Android 10, and cybercriminals are using it to break into online bank accounts and steal money from users.
The vulnerability, called StrandHogg, involves Android's core multitasking processes and affects unrooted and rooted phones alike. Although Google has known of StrandHogg for at least three months, no fix has yet been delivered.
"StrandHogg is unique because it enables sophisticated attacks without the need for the device to be rooted," says a report posted earlier this week by researchers at Norwegian security firm Promon, who found and named the bug.
"To carry out attacks, the attacker doesn't need any special permissions on the device. The vulnerability also allows an attacker to masquerade as nearly any app in a highly believable manner."
Hackers exploiting StrandHogg can "listen to the user through the microphone; take photos through the camera; read and send SMS messages; make and/or record phone conversations; phish login credentials; get access to all private photos and files on the device; get location and GPS information; get access to the contacts list [and] access phone logs," according to the report.
UPDATE: In response to a query from Tom's Guide, Google provided this statement:
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
"We appreciate the researchers work, and have suspended the potentially harmful apps they identified. Google Play Protect detects and blocks malicious apps, including ones using this technique. Additionally, we're continuing to investigate in order to improve Google Play Protect's ability to protect users against similar issues."
We've repeated our question to Google about when a patch might be forthcoming, and will update this story again if we receive an answer.
How to protect yourself from the StrandHogg flaw
If you're an Android user, it won't be easy to tell if your phone has been infected by StrandHogg-exploiting malware. However, you should get suspicious if an app to which you're already logged in, such as Facebook or Google, asks again for login credentials, or if an app seems to make excessive permission requests.
Running one of the best Android antivirus apps should protect you for the most part, especially if you download apps only from the Google Play Store and grant no apps permissions to download apps from anywhere else.
Promon posted a video showing how StrandHogg could steal login credentials from someone using a Samsung Galaxy S10 phone running Android 10.
San Francisco security firm Lookout Mobile Security partnered with Promon and found 36 apps exploiting the StrandHogg flaw. Many were banking Trojans designed to steal money from online bank accounts.
None of those 36 apps were in the Google Play Store, but there's a twist. Sticking to the Google Play Store for apps won't be enough to protect you, because Promon found several "dropper" apps in Google Play that, once installed, would then install StrandHogg-exploiting apps without the users' knowledge in a two-step process.
The StrandHogg flaw, named after the Vikings who would raid beach towns, is pretty easy to grasp. It lets a malicious app hijack the fullscreen-display process from another app and seize control of the screen without the user's knowledge.
So, for example, if you tapped the Facebook icon on your Android phone, a StrandHogg-exploiting app could seize control of the screen from Facebook before Facebook could display a fullscreen image.
The malicious app could then display a Facebook login page and get you to input your email address and password, which the malicious app could then send to a remote attacker.
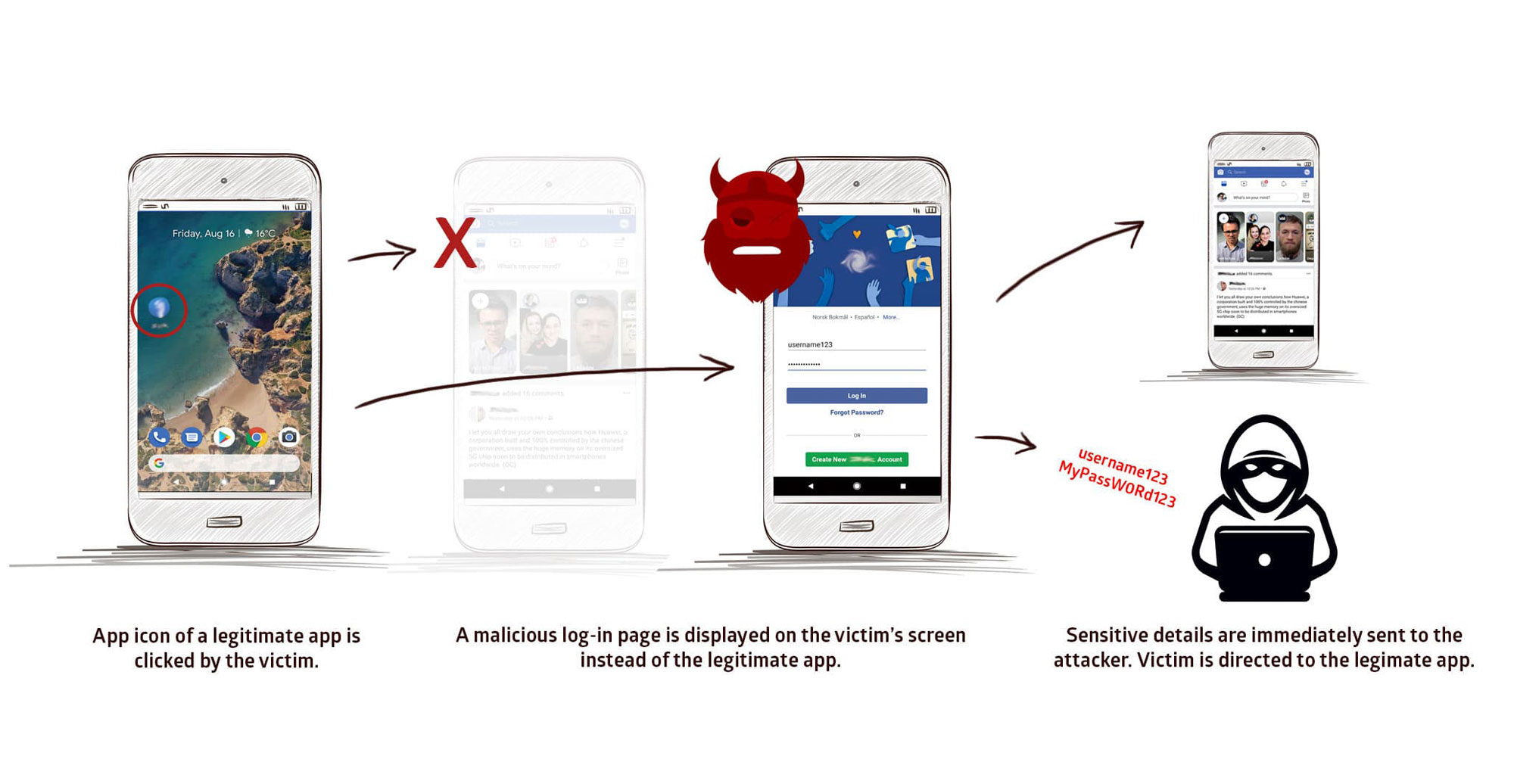
That's a classic phishing attack, and StrandHogg makes it possible on all versions of Android. On Android 6 Marshmallow and later, it gets worse: A StrandHogg-exploiting malicious app can also ask you for various system permissions while pretending to be a known benign app. You could inadvertently give hackers nearly total control over your phone.
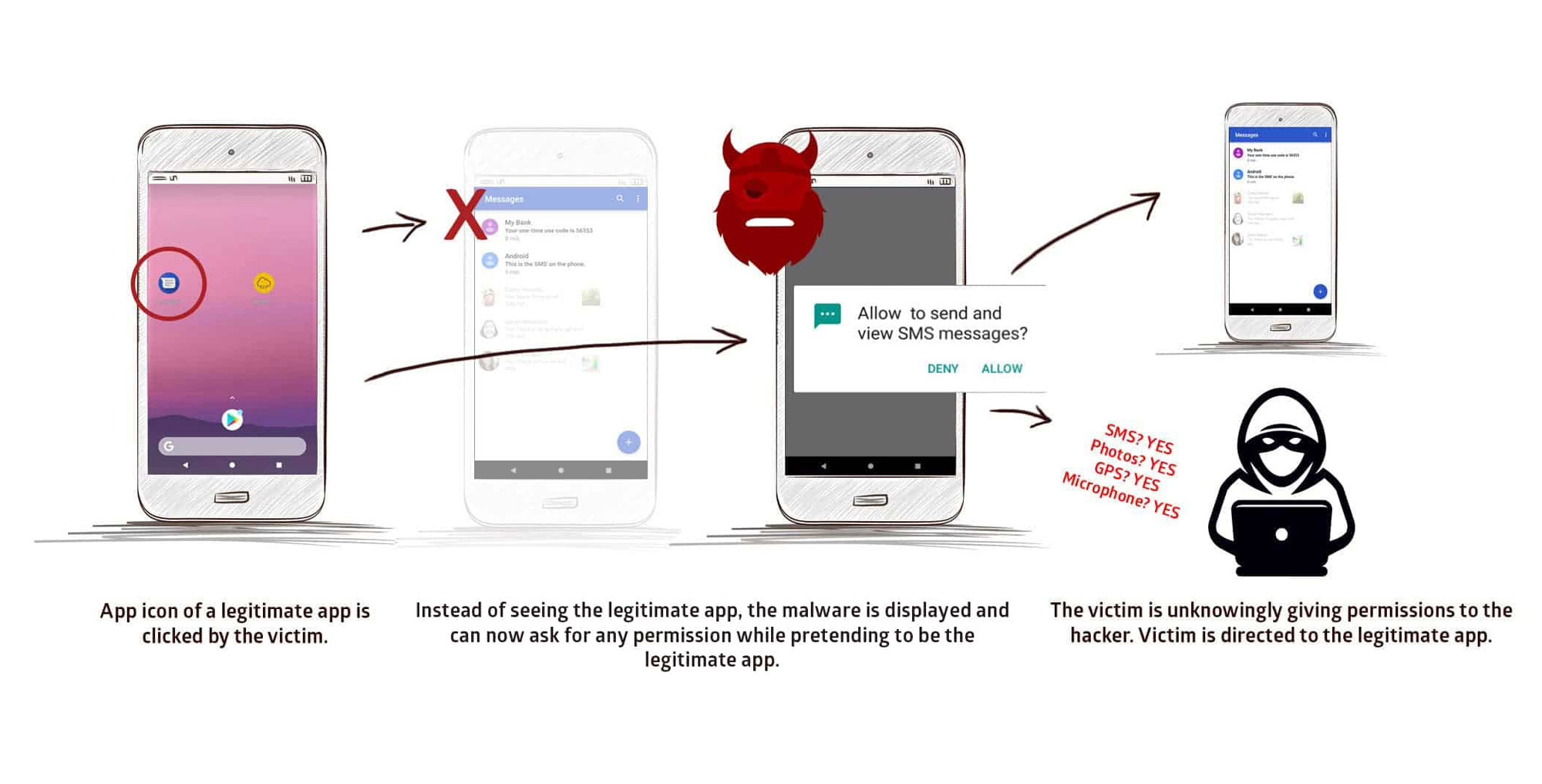
These attacks seem to work on all legitimate Android apps. Promon tested 500 of the most popular Android apps and couldn't find a single one that was immune.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
 Club Benefits
Club Benefits










