How to Decrypt Files Seized by CoinVault Ransomware
Thanks to Dutch police and Kaspersky Lab, CoinVault victims may be able to decrypt files held hostage by the hard-to-beat ransomware.
Have you been infected with the insidious CoinVault encrypting ransomware? If so, there's some potentially good news. Thanks to the efforts of Dutch police and antivirus maker Kaspersky Lab, you may be able to decrypt your files. There's only one catch: If you get infected in the near future, you're out of luck.
Dutch investigators found that CoinVault was based in the Netherlands and raided the malefactors' servers, yielding many encryption keys for users files locked up by CoinVault in the Netherlands, Germany and the United States. From there, Moscow-based Kaspersky Lab stepped in and developed a free tool to help victims liberate their own data.
MORE: Best Antivirus Software and Apps
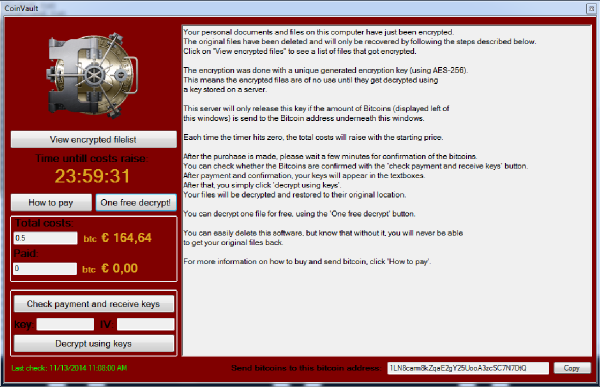
CoinVault is a nasty bit of ransomware that infects users' computers, locks the users out of their files and then demands money to decrypt them. After the encryption takes place, there's no easy fix other than paying up, and removing the malware won't restore the files. Although CoinVault is not as prominent as better-known encrypting ransomware such as Cryptolocker or Cryptowall, it has more than its share of victims.
If you've been infected with CoinVault and want your data back, Kaspersky Lab details the process of how to do so. The steps are as follows:
1. Make note of both the Bitcoin wallet address and the encrypted file list when the CoinVault ransom demand screen appears. Copy the Bitcoin address and save the encrypted file list somewhere safe.
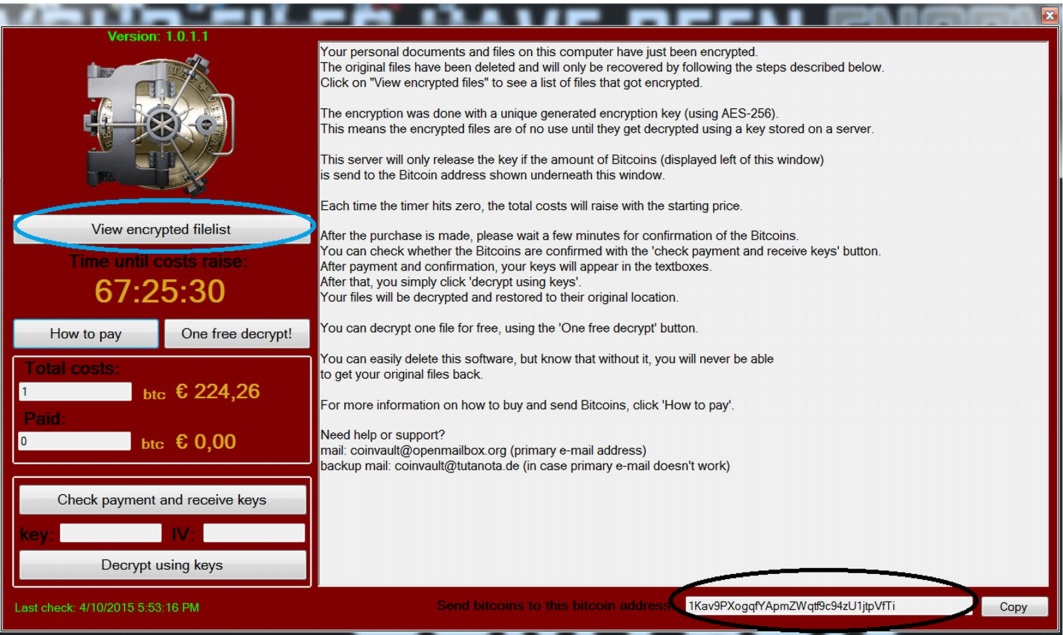
2. Remove the CoinVault malware from your system. Kaspersky Lab points out that the trial version (offered here for download) or full version of Kaspersky Internet Security will do so, but so will any other anti-malware program worth its salt. (Remember that removing the program will not decrypt your files.)
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
3. Visit the Kaspersky Ransomware Decryptor site at noransom.kaspersky.com. Enter the Bitcoin wallet address you copied earlier and see whether it corresponds to one of the encryption keys that the police recovered. (If it doesn't, then you're back to Square One with no easy fix.) Download the decryption tool, run it, and follow all the on-screen directions.
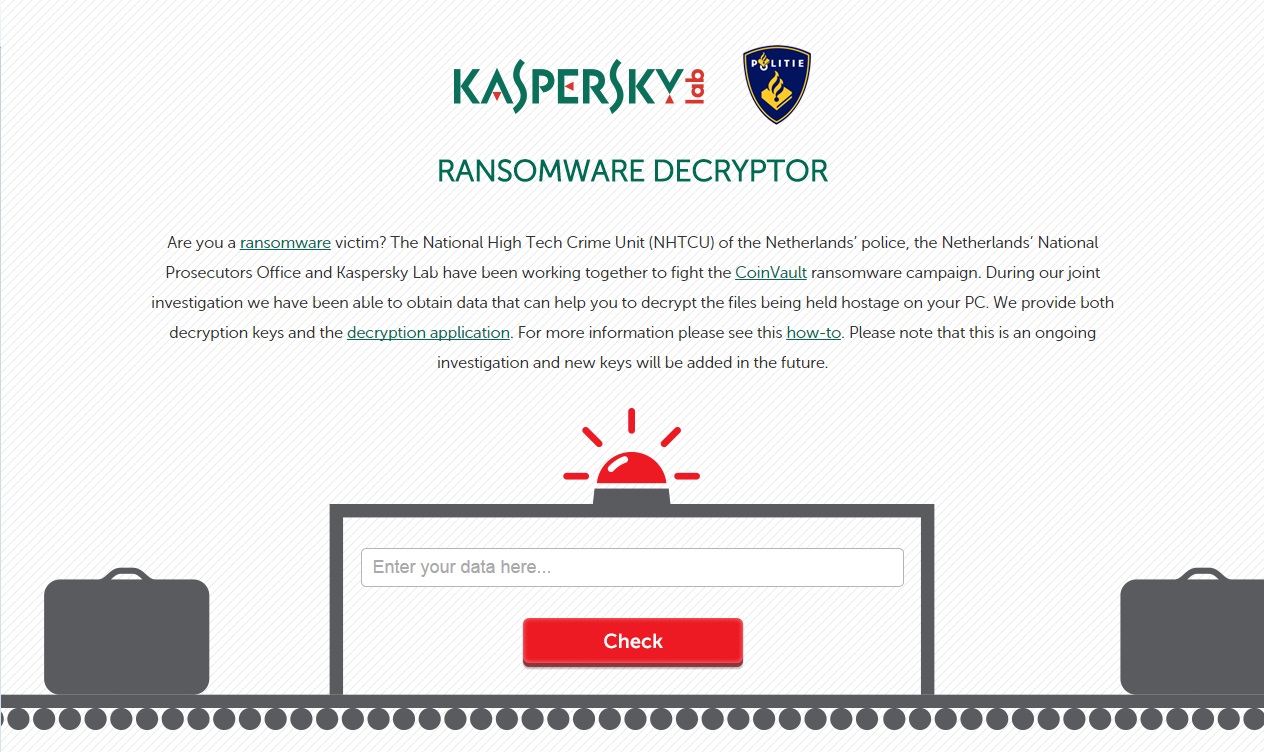
4. If you get a .NET Framework error while trying to install the decryption tool, you'll have to download additional Microsoft libraries and install them. Simply visit Microsoft's website, download the necessary files, and install them. Then, try reinstalling the decryption tool.
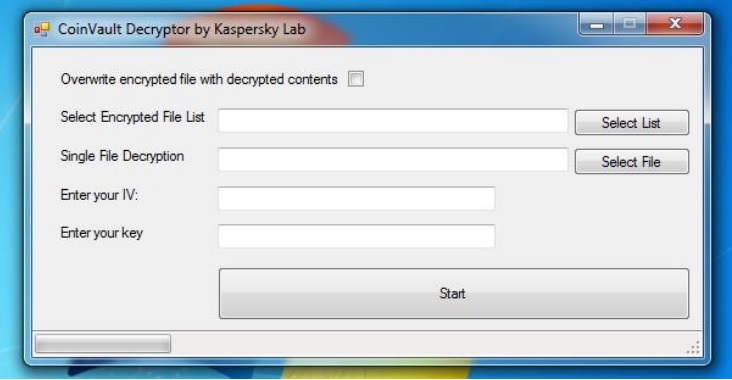
5. Enter your file list, initialization vector and decryption key into the tool's form fields. (If more than one decryption key or IV were associated with your Bitcoin address, make sure to NOT check the box marked "Overwrite encrypted file with decrypted contents.")
6. Click Start, and wait for your files to become your own once again. If you had more than one possible decryption key, and the output files still look like gibberish, delete the output files and try the next key-IV set on the encrypted files. Work your way through the list of possible keys and IVs.
There are some potential pitfalls to the process. It's unlikely the Dutch police found every single encryption key that CoinVault used, so some users may still be out of luck. Furthermore, any new CoinVault infection will probably use a new encryption key, so users who were infected very recently (or who will be infected in the future) may have little recourse except to pay up or wait for another solution.
- How to Survive a Data Breach
- Best Cloud Backup Services
- Mobile Security Guide: Everything You Need to Know
Marshall Honorof is a senior writer for Tom's Guide. Contact him at mhonorof@tomsguide.com. Follow him @marshallhonorof. Follow us @tomsguide, on Facebook and on Google+.

Marshall Honorof was a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.
