Comcast Attack Combines Ransomware, Tech-Support Scam
Clicking an ad on a Comcast Xfinity search results page led users down a painful path featuring ransomware and the long-running Windows Tech Support scam.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
A new malware campaign stalked Comcast cable broadband customers with a one-two punch of ransomware and a tech-support scam, and required only that victims visit a single corrupted Web page. This hybrid campaign may be the first of its kind, and looks to hit users in every way possible.

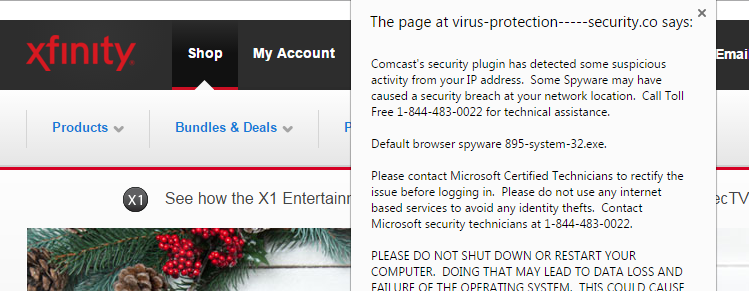
Users of Comcast’s Xfinity search engine were exposed to an ad link that reads "DirectTV compared to Comcast TV," which led to a page on the apparently legitimate SatTVPro website. But thanks to an outmoded content-management platform, the page had been infected with the dangerous Nuclear Pack browser exploit kit, which lurked in the background. The corrupted page also sent users to a fake Comcast Xfinity site, which popped up a message informing the victim that his or her computer was infected, and to call a provided toll-free number to speak to "Microsoft security technicians."
The Nuclear Pack exploit kit will attempt to drop many kinds of malware on your computer, including encrypting ransomware that will hijack your system and ask for money. The long-running Windows-tech-support scam is easier to understand, except in this case, the alert window that says your system has been infected isn't telling a lie. But as usual, the toll-free number will put you on the line not with Microsoft technicians, but with call-center workers overseas whose job it is to get you to buy bogus computer-security software.
MORE: Best Antivirus Protection for PC, Mac and Android
Researchers at the San Jose, California-based Malwarebytes security firm discovered the malware campaign and immediately notified Comcast, Google and the operators of the SatTVPro websites. Google temporarily added SatTvPro to its Safe Browsing blacklist to protect its users from opening the malicious Web page. Earlier today (Dec. 14) the SatTVPro blog switched its content platform from Joomla to WordPress, which seems to have purged the Nuclear Pack exploit kit, and the page in question is no longer blocked by Google.
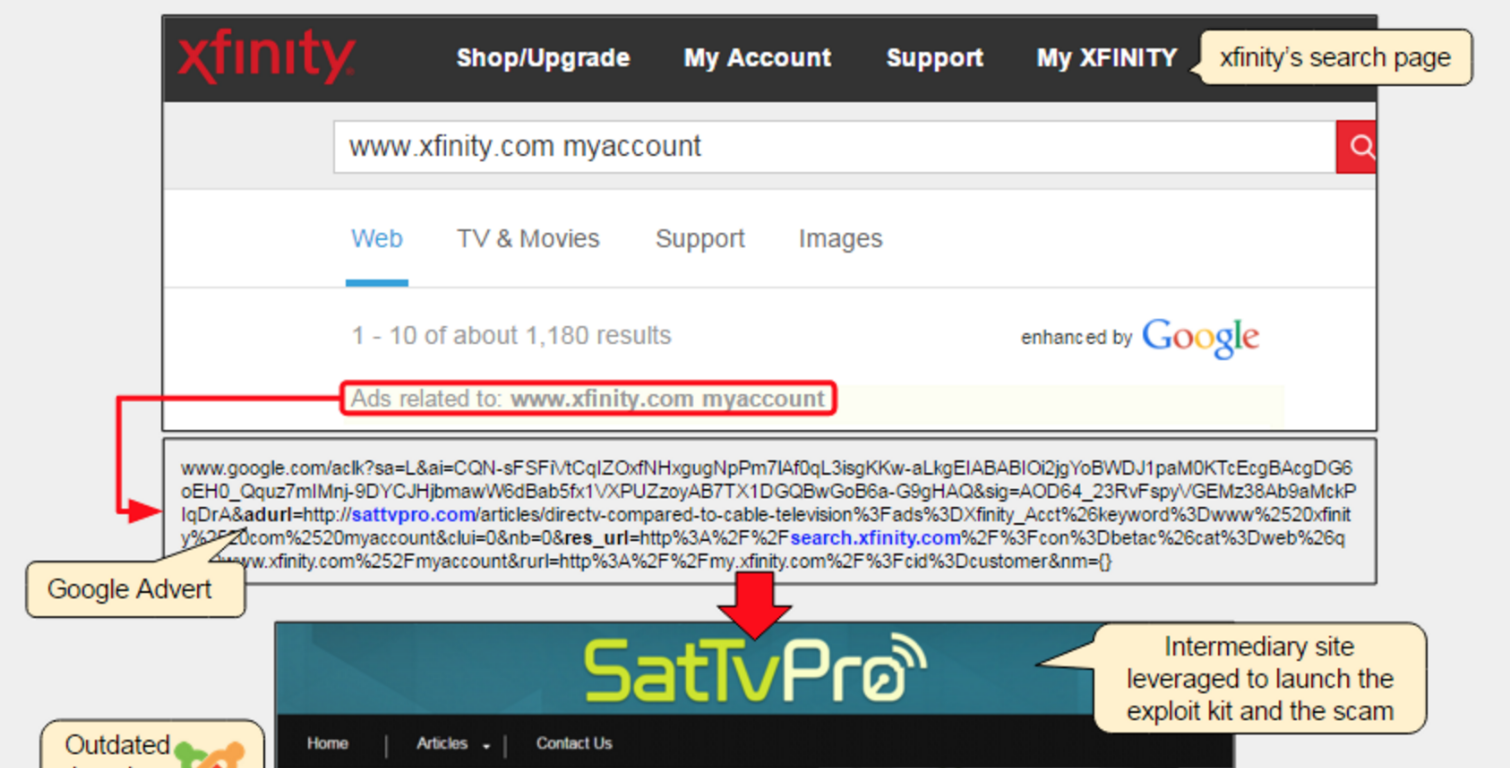
What isn't clear is who is coordinating this trifecta of malvertising, ransomware and support scam attacks, and who placed the ad link on the Comcast Xfinity page. It's possible that the ad was a legitimately purchased link to direct users to the SatTVPro page. It's also possible that a malicious actor, knowing the page had been infected with the Nuclear Pack exploit kit, bought the ad to funnel victims to the trap.
It may be that a single malevolent entity was directly pocketing the proceeds from the ransomware (and other malware) dropped on victims' PCs by the Nuclear Pack kit, and from the sales of bogus security software generated by the tech-support scams. But it's more likely that the person who infected the SatTVPro page simply collected a small percent of the proceeds from both, and that the exploit-kit handlers and tech-support-scammers didn't know each other.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
"From the point of view of a malicious actor redirecting traffic (traffer)," wrote Malwarebytes blogger Jerome Segura, "it makes a lot of sense to get paid a double commission for referral traffic: one from the exploit-kit operator and another from tech-support scammers."
While we advise users to not visit suspicious Web pages or click on shady links, this story is just the latest piece of evidence that skepticism while Web browsing is not enough. Users should protect their system with robust anti-virus software to protect themselves from attacks from reputable websites, should always keep their browsers and operating systems patched and up to date, and should consider disabling or limiting browser plugins commonly attacked by browser exploit kits, such as Adobe Flash Player, Java and Microsoft Silverlight.

Henry was a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom's Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He's also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
 Club Benefits
Club Benefits





