Android Phones
Latest about Android Phones
-
-

This hidden Android feature was a lifesaver when my home internet died — here's how it works
By Tom Pritchard Published
-

Not a typo! T-Mobile is giving away Samsung's Galaxy S25 Plus for free right now
By Olivia Halevy Published
-

A whole new kind of phone case — 3 action buttons revolutionize the S25 Ultra experience
By Sponsored Published
-

Samsung Galaxy Z Flip 7 rumors — everything we know so far
By Josh Render Last updated
-

Samsung keeps hyping the Galaxy Z Fold 7 — here's why that could backfire
By Philip Michaels Last updated
-

Samsung Galaxy Z Fold 7 teaser suggests a big AI camera upgrade is on the way
By Richard Priday Published
-

Samsung Galaxy Z Fold 7 rumors and leaks — everything we know so far
By Richard Priday Last updated
-
Explore Android Phones
Google Phones
-
-
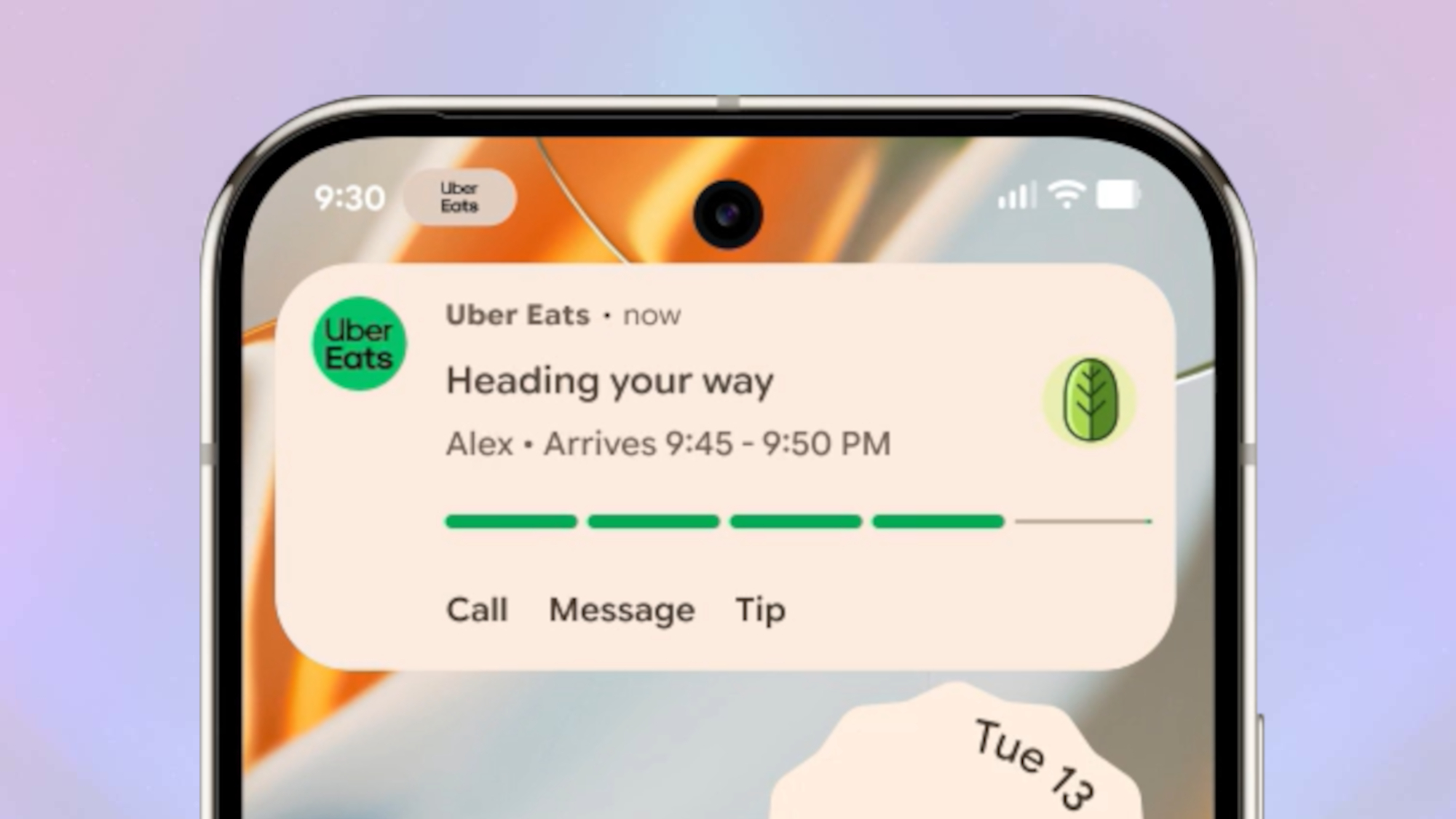
Live Updates just arrived on Android 16 — but it's not quite finished yet
By Josh Render Published
-

Google just launched Android 16 — plus a bunch of other useful software upgrades
By Tom Pritchard Published
-

Don’t wait! This Pixel 8 Pro deal for $499 includes a Pixel Watch 2 and case
By John Velasco Published
-

Google Pixel 10's video stabilization could be so good you'll never need a gimbal again
By Tom Pritchard Published
-

Google Pixel 10 may not be launching on August 13 after all — what we know
By Josh Render Published
-

Pixel 10 Pro images may give us our best look at the phone yet — and it looks very familiar
By Tom Pritchard Published
-

Google Pixel 10 — biggest rumors and what we want to see
By Tom Pritchard Last updated
-

Pixel 10 release date just leaked — here's when it could drop
By Dave LeClair Published
-

The Pixel 10 lineup could launch sooner than we think thanks to a Google hint
By Scott Younker Published
-
Motorola Phones
-
-

I've used the Motorola Razr Ultra (2025) for a month and it solves my biggest issue with the Galaxy S25 Edge
By John Velasco Published
-

Not a typo! You can already get the Motorola Razr (2025) for free — here's how
By John Velasco Published
-

I shot over 200 photos with the Razr Ultra 2025 vs Razr Plus 2024 — here’s the winner
By John Velasco Published
-

Motorola Razr Ultra 2025 review: The most powerful flip phone to date
By John Velasco Last updated
-

Forget Razr Ultra — Best Buy has the Motorola Razr Plus 2023 for just $249 right now
By John Velasco Published
-

I tried the Motorola Razr Ultra's killer feature — and it takes productivity to a new level
By John Velasco Published
-

Motorola Razr 2025 launch live — three new foldables just announced
By John Velasco Last updated
-

Motorola Razr 2025 design and colors just leaked ahead of launch tomorrow
By Tom Pritchard Published
-

Motorola Razr Plus 2025 — 7 biggest rumored upgrades for the new flip phone
By John Velasco Published
-
OnePlus Phones
-
-

OnePlus 13s just got this useful Gemini feature — and not even Google Pixels have it
By Josh Render Published
-

OnePlus 13T isn't coming to the US or Europe — and I don't get why
By Richard Priday Published
-

OnePlus confirms the 13T won't be coming to North America
By Scott Younker Published
-

OnePlus 13T confirmed for April 24 launch — here's your first official look
By Tom Pritchard Last updated
-

Android 16 public beta released for OnePlus 13 — and I wouldn’t download it
By Josh Render Published
-

OnePlus teases the new ‘shortcut key’ on OnePlus 13T — say goodbye to the Alert Slider
By Tom Pritchard Published
-

Best OnePlus phones in 2025
By Richard Priday Last updated
-

OnePlus Open 2 could have been the best foldable of the year — so why is it not happening?
By Philip Michaels Last updated
-

OnePlus reportedly developing massive smartphone batteries — what we know
By Scott Younker Published
-
Samsung Phones
-
-

Not a typo! T-Mobile is giving away Samsung's Galaxy S25 Plus for free right now
By Olivia Halevy Published
-

A whole new kind of phone case — 3 action buttons revolutionize the S25 Ultra experience
By Sponsored Published
-

Samsung keeps hyping the Galaxy Z Fold 7 — here's why that could backfire
By Philip Michaels Last updated
-

Samsung Galaxy Z Fold 7 teaser suggests a big AI camera upgrade is on the way
By Richard Priday Published
-

Samsung Galaxy Z Fold 7 rumors and leaks — everything we know so far
By Richard Priday Last updated
-

The Galaxy Z Fold 7 could be the fastest foldable yet with Snapdragon 8 Elite power
By Dave LeClair Published
-

Samsung Galaxy S25 is suffering from an embarrassing design quality issue — what you need to know
By Josh Render Published
-

Samsung teases Galaxy Z Fold 7 again — promises 'thinnest, lightest and most advanced foldable yet'
By Richard Priday Published
-

New rumor doubles down on smaller battery for the Galaxy S26 Ultra — here’s what we know
By Josh Render Published
-
More about Android Phones
-
-

Samsung Galaxy Z Fold 7 rumors and leaks — everything we know so far
By Richard Priday Last updated
-

The Galaxy Z Fold 7 could be the fastest foldable yet with Snapdragon 8 Elite power
By Dave LeClair Published
-

Live Updates just arrived on Android 16 — but it's not quite finished yet
By Josh Render Published
-