Android Phones
Explore Android Phones
Latest about Android Phones

I tested the Honor Magic8 Pro, and it addressed almost all the problems I had with the last model
By Richard Priday published
Honor clearly listened to critiques when developing this phone
Got a new Android phone? These are the top 5 apps that you should consider downloading first
By Josh Render published
Your phone is more than just a means to call your friends

Samsung Galaxy S26 Ultra vs. iPhone 17 Pro: How these top flagship phones could compare
By Philip Michaels published
The Galaxy S26 Ultra figures to be Samsung's premium flagship when it debuts this year. But can it top the value that the iPhone 17 Pro provides?
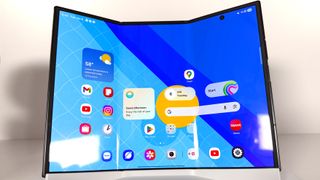
Samsung Galaxy Z TriFold hands-on: Your biggest questions answered
By Mark Spoonauer published
Not yet ratedSpoiler: I like it a lot more than I thought I would

Samsung Galaxy S26 Ultra: All the rumors so far
By Alan Martin last updated
Samsung’s next flagship phone is already taking shape ahead of its launch later this year. Here's what we know so far about the Galaxy S26 Ultra.

First the iPhone 17 Pro, now the Galaxy S26 Ultra? Why phone makers may be turning their backs on titanium
By Philip Michaels published
Galaxy S26 rumor has Samsung dropping titanium from its Ultra model

Motorola Razr Fold hands-on: I like it more than I thought I would
By Mark Spoonauer last updated
The Motorola Razr Fold is the company’s first book-style foldable, and I went hands-on at CES 2026 to check out the design, displays and cameras to see if it can compete with Samsung.

Motorola could challenge the iPhone Fold with a new book-style foldable phone this year
By Josh Render last updated
A leaked slide from Motorola indicates that the company could soon reveal a brand new book-like foldable phone.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
 Club Benefits
Club Benefits







