Phones
Latest about Phones
-
-

Samsung Galaxy Unpacked July 2025 — Galaxy Z Fold 7, Z Flip 7, Galaxy Watch 8 and everything to expect
By John Velasco Last updated
-

Total Wireless deal knocks $300 off iPhone 16e — here's how to get it
By Louis Ramirez Published
-

Anker expands power bank recall to include five more products — how to tell if your charger is affected
By Scott Younker Published
-

Samsung Galaxy Z Flip 7 rumors — everything we know so far
By Josh Render Last updated
-

Apple reportedly has more iOS 26 features in the works — here's what's coming to your iPhone
By Scott Younker Published
-

Apple has announced 13 car makers that are offering iPhone car keys — but when are they coming?
By Scott Younker Published
-

Samsung Galaxy Z Fold 7 could be a record-breaking foldable — here’s why
By Josh Render Published
-
Explore Phones
Android Phones
-
-

Samsung Galaxy Unpacked July 2025 — Galaxy Z Fold 7, Z Flip 7, Galaxy Watch 8 and everything to expect
By John Velasco Last updated
-

Samsung Galaxy Z Flip 7 rumors — everything we know so far
By Josh Render Last updated
-

Samsung Galaxy Z Fold 7 could be a record-breaking foldable — here’s why
By Josh Render Published
-

Samsung Galaxy G Fold rumors — everything we know about Samsung's triple foldable phone
By Richard Priday Last updated
-
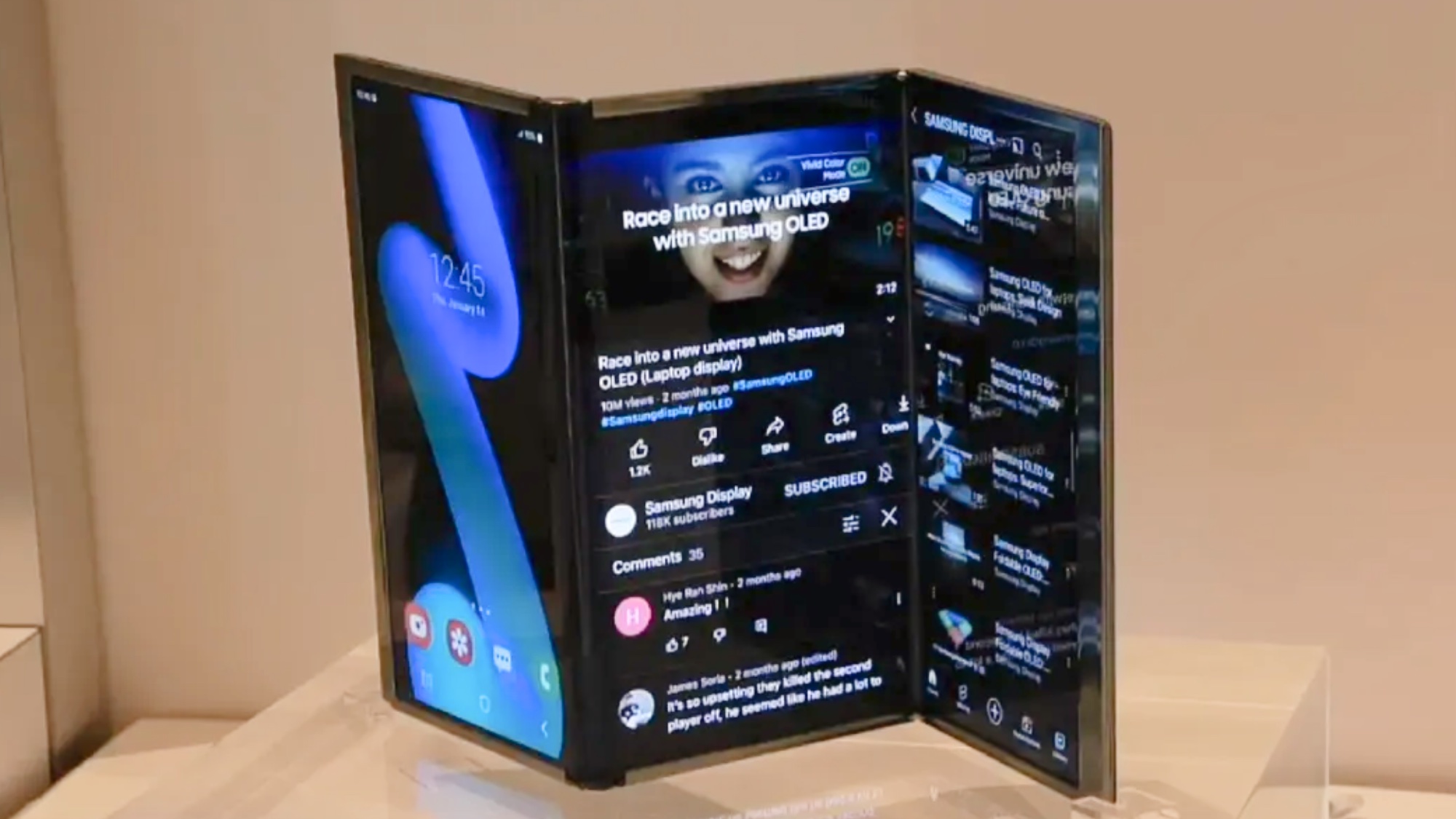
Samsung's tri-fold Galaxy G Fold could appear at Unpacked — what we know
By Josh Render Published
-

I’ve been using Android 16 for two weeks — here’s why I’m so underwhelmed
By Tom Pritchard Published
-

Samsung Galaxy Fold 7 and Flip 7 leak before Unpacked — and they’re super slim
By Alyse Stanley Published
-

Samsung Galaxy Z Flip 7 FE tipped for Unpacked — and it could be the cheap foldable we've all been waiting for
By Philip Michaels Published
-

Nothing Phone 3 design just leaked in full — here's what the new renders show
By Tom Pritchard Published
-
Network Carriers
-
-

T-Satellite with Starlink is launching next month — what you need to know about T-Mobile's satellite-to-mobile service
By Philip Michaels Published
-

Best Verizon phone deals for June 2025
By Philip Michaels Last updated
-
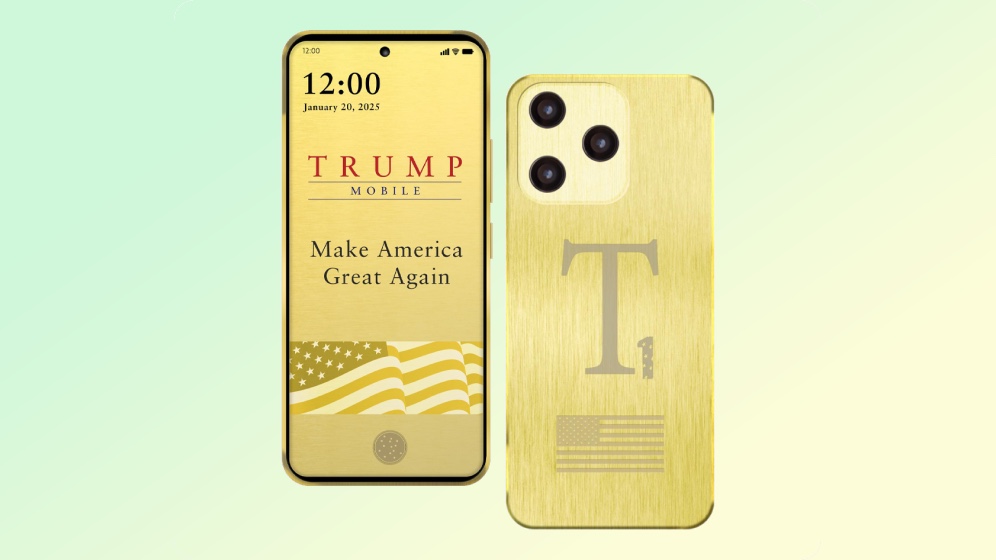
Trump Mobile launching with gold T1 phone and unlimited data — here's how they stack up
By Philip Michaels Published
-

The best prepaid phone plans in 2025
By Philip Michaels Last updated
-

The best cheap cell phone plans 2025
By Philip Michaels Last updated
-

Hurry! Metro by T-Mobile is offering one line of unlimited 5G for just $40
By Olivia Halevy Published
-

Best unlimited data plans in 2025
By Philip Michaels Last updated
-
Best phone carriers of 2025
By Philip Michaels Last updated
-
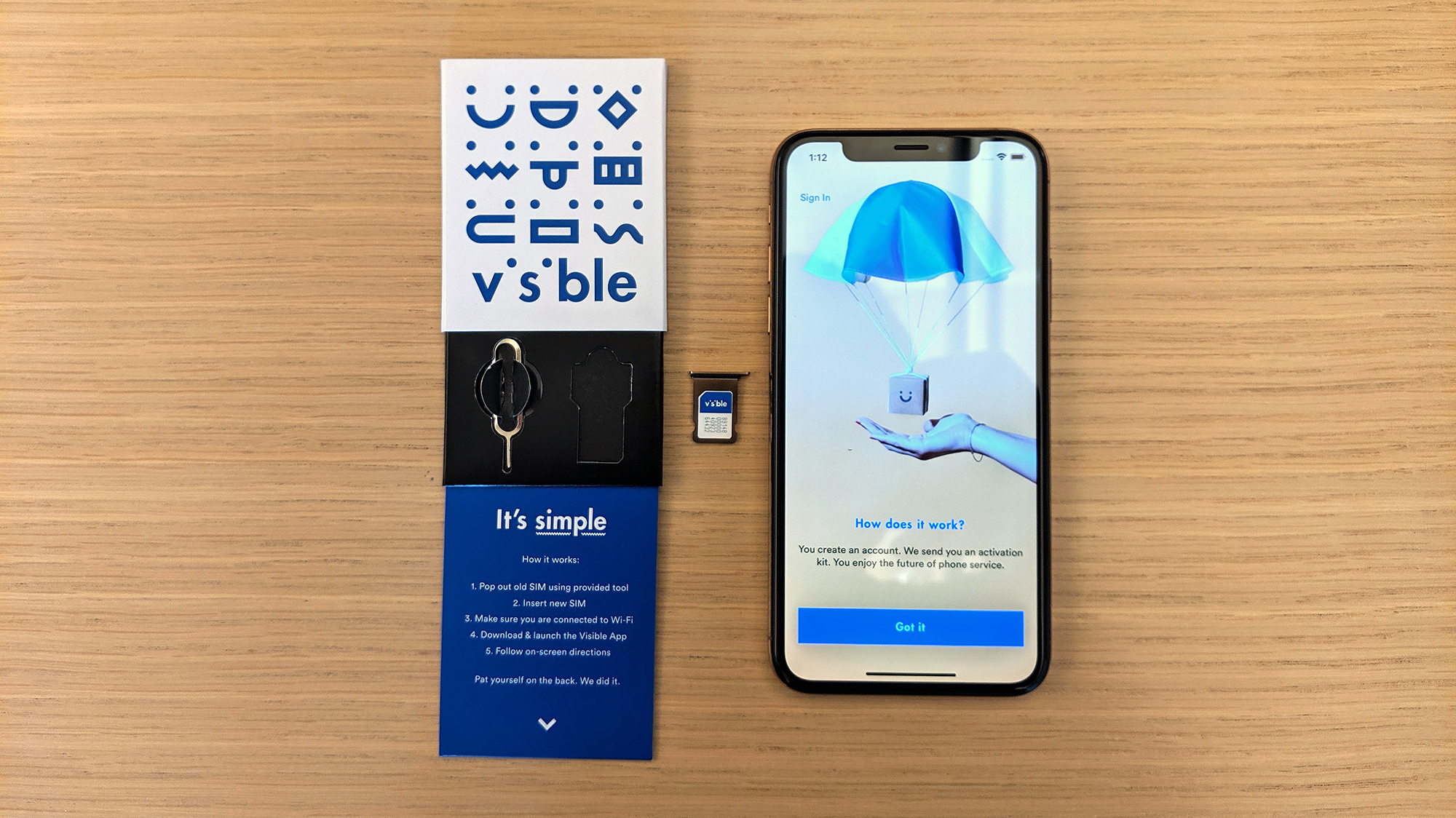
Best Visible deals in July 2025
By Louis Ramirez Last updated
-
iPhones
-
-

Total Wireless deal knocks $300 off iPhone 16e — here's how to get it
By Louis Ramirez Published
-

Apple reportedly has more iOS 26 features in the works — here's what's coming to your iPhone
By Scott Younker Published
-

Apple has announced 13 car makers that are offering iPhone car keys — but when are they coming?
By Scott Younker Published
-

iPhone 17 Pro — all the rumors and leaks so far
By Philip Michaels Last updated
-

iPhone 17 Pro Max — all the rumors so far
By Tom Pritchard Last updated
-
I’ve been testing Adobe’s Project Indigo camera app — and I might ditch the iPhone's camera app for good
By Richard Priday Published
-

iPhone 17 Pro could get a huge unexpected design change — what we know
By Richard Priday Published
-

iPhone 17 colors: Here's what's rumored for this fall's new iPhones
By Philip Michaels Published
-

iOS 26 brings big changes to your iPhone lock screen — what to expect
By Philip Michaels Published
-