Phones
Latest about Phones
-
-

iOS 26 has an awesome Wi-Fi upgrade for your iPhone
By Dave LeClair Published
-

iOS 26 beta is freezing FaceTime when it detects nudity — what we know so far
By Tom Pritchard Published
-

New Galaxy S26 Ultra battery and camera rumors have me worried — here’s why
By Josh Render Published
-

The iPhone Fold just hit a major milestone on path to launch in 2026
By Tom Pritchard Published
-

Finally! Real-life images of the Galaxy Z Fold 7 leak to show us the foldable's new design
By Richard Priday Published
-

Early Amazon Prime Day phone deals — some of my favorite phones are already on sale
By Philip Michaels Published
-

Best cell phone plans for seniors in 2025
By Philip Michaels Last updated
-
Explore Phones
Android Phones
-
-

New Galaxy S26 Ultra battery and camera rumors have me worried — here’s why
By Josh Render Published
-

Finally! Real-life images of the Galaxy Z Fold 7 leak to show us the foldable's new design
By Richard Priday Published
-

CA jury finds against Google in idle cellular data case — and it’s being fined $314 million
By Josh Render Published
-

Galaxy Z Flip 7 FE tipped for Unpacked release thanks to new case leak — get ready for a cheaper foldable
By Tom Pritchard Published
-

Massive leak reveals Google Pixel 10 Pro specs — plus, Pixel 10 Pro XL updates
By Scott Younker Published
-

I just went hands-on with the Nothing Phone 3 — and it’s the most unique flagship of 2025
By Richard Priday Published
-

Samsung Galaxy Z Fold 7 rumors and leaks — everything we know so far
By Richard Priday Last updated
-

Galaxy Z Fold 7 — we just got bad news about the design right before Unpacked
By Philip Michaels Published
-
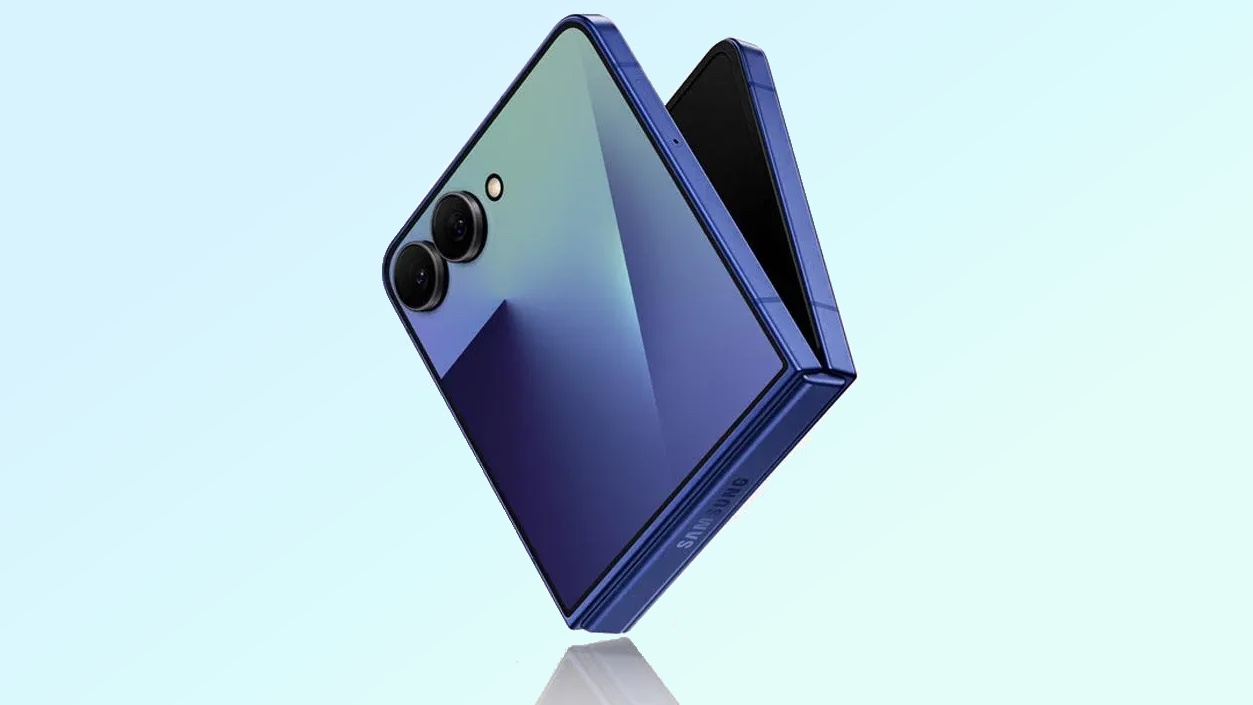
Samsung Galaxy Z Flip 7 vs. Flip 6: Biggest rumored upgrades
By Philip Michaels Last updated
-
Network Carriers
-
-
 50% OFF
50% OFFTello Coupon Codes
By Louis Ramirez Published
-
 $5 OFF
$5 OFFAT&T Promo Codes
By Louis Ramirez Published
-

Best cell phone plans for seniors in 2025
By Philip Michaels Last updated
-

T-Satellite with Starlink is launching next month — what you need to know about T-Mobile's satellite-to-mobile service
By Philip Michaels Published
-

Best Verizon phone deals for June 2025
By Philip Michaels Last updated
-
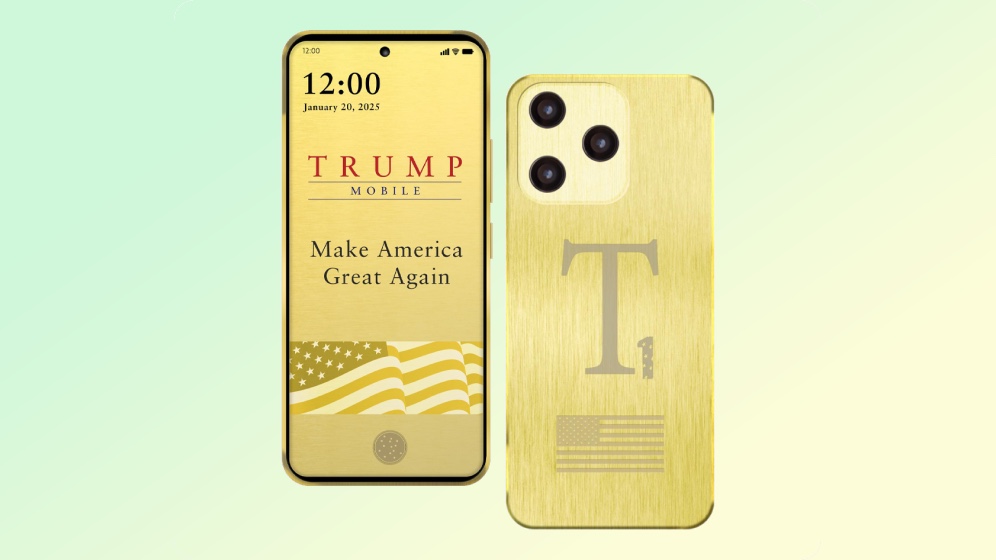
Trump Mobile launching with gold T1 phone and unlimited data — here's how they stack up
By Philip Michaels Published
-

The best prepaid phone plans in 2025
By Philip Michaels Last updated
-

The best cheap cell phone plans 2025
By Philip Michaels Last updated
-

Hurry! Metro by T-Mobile is offering one line of unlimited 5G for just $40
By Olivia Halevy Published
-
iPhones
-
-

iOS 26 beta is freezing FaceTime when it detects nudity — what we know so far
By Tom Pritchard Published
-

The iPhone Fold just hit a major milestone on path to launch in 2026
By Tom Pritchard Published
-

Apple just delivered a smackdown to the EU over iOS 26 rollout — they won't be getting new features
By Jeff Parsons Published
-

Apple could hand Siri's AI upgrades to OpenAI or Anthorpic — what we know
By Tom Pritchard Published
-

Total Wireless deal knocks $300 off iPhone 16e — here's how to get it
By Louis Ramirez Published
-

Apple reportedly has more iOS 26 features in the works — here's what's coming to your iPhone
By Scott Younker Published
-

Apple has announced 13 car makers that are offering iPhone car keys — but when are they coming?
By Scott Younker Published
-

iPhone 17 Pro — all the rumors and leaks so far
By Philip Michaels Last updated
-

iPhone 17 Pro Max — all the rumors so far
By Tom Pritchard Last updated
-
