MacBook security alert: Update to macOS 11.3 right now
Upgrade to macOS 11.3 as soon as possible to protect yourself

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
Apple macOS users are being urged to update their Macs to ensure they're protected against a zero-day vulnerability that’s been exploited by attackers since at least January.
The flaw lets hackers bypass a whole suite of macOS security protocols, allowing them to deploy malware on affected machines. It may be one of the worst vulnerabilities to hit Apple’s computers in many years.
- The best password managers in 2021
- The best Mac antivirus software
- Plus: New iMac 2021 release date, price, specs, colors, keyboard and more
Security researcher Cedric Owens identified the security bug back in March and noted it affects “all recent versions of macOS,” including macOS versions 10.15 Catalina, released in October 2019, to 11.2 Big Sur.
Normally, macOS security mechanisms like Gatekeeper and File Quarantine would block malicious or unsigned files and software from being installed on Macs. But Owens found that this zero-day flaw allowed these obstacles to be bypassed, letting him craft malicious files that, when clicked on, didn't throw up a security alert in macOS and would run.
Owens attributes this to the system miscategorizing the malware because of a logic error in macOS’ code, which creates a workaround to Apple's defenses.
Kudos to Apple for quickly fixing the bug I reported to them. Here is my blog that delves into how I weaponized this bug with a payload: https://t.co/Bj8bQbpLx5. Thanks @patrickwardle for helping dive into the vuln as well 🙏🏽 pic.twitter.com/tnMo3is0K8April 26, 2021
Apps as an avenue of attack
As we’ve before, such "Trojan" apps that appear benign play a key role in letting malware snatch the keys to your machine.
We've seen seemingly innocuous kids' apps harboring crypto-casinos on the App Store, not to mention recent news of a fake Netflix app spreading malware on Android phones.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The point is: Apps are attractive to crooks as they often provide an easy entry point to exploit users' machines if they can convince a user to download or run an app that's not in the App Store, or is nestled between other App Store apps to appear legitimate. That's where built-in security measures come into effect, basically protecting users from themselves.
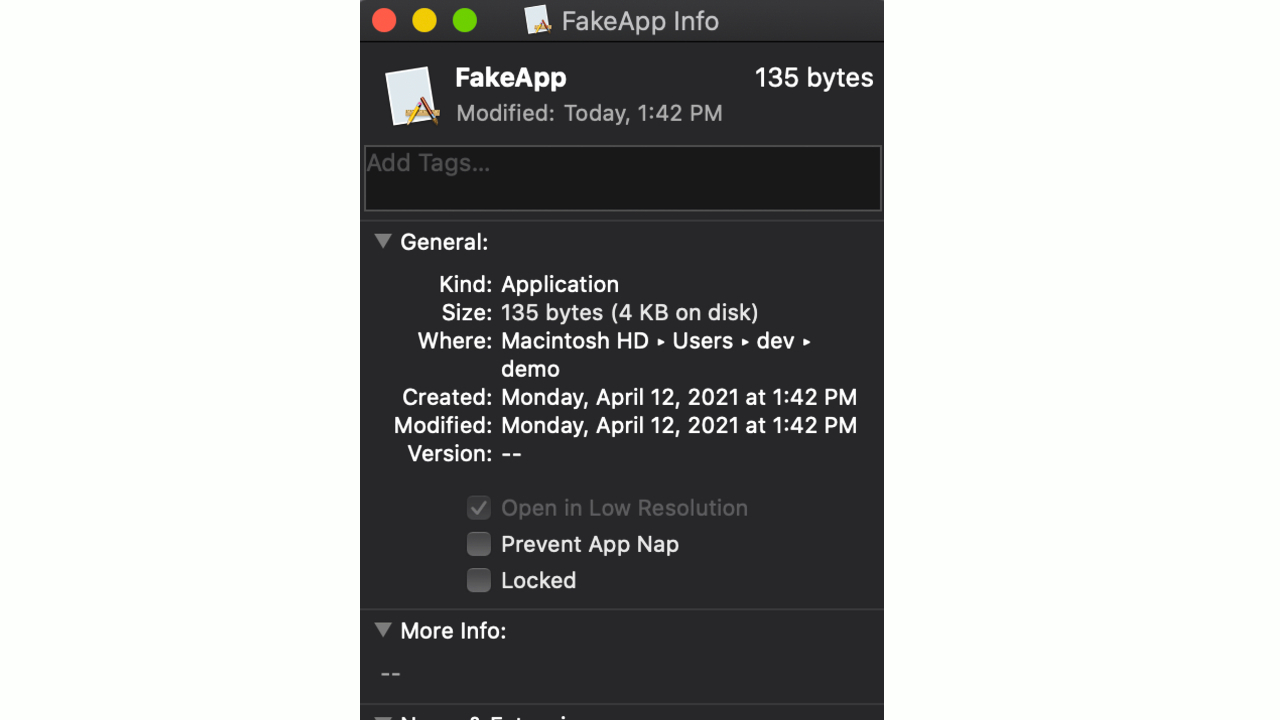
On this occasion, Owens found that Gatekeeper failed to properly check specific scripts within apps. He used a tool called Appify, which had circumvented Gatekeeper checks all the way back in 2011 and offers a legitimate tool to enable developers to create basic apps with just a script.
With knowledge of these previous vulnerabilities in tow, Owens mocked up a test program to hide a harmless-looking document that concealed malware.
Owens was able to sail past up-to-date macOS software, even with Gatekeeper cranked up to its most stringent security settings. No warnings were triggered and the malware snuck past Apple's defenses to provide Owens with remote control over the Mac.
Here's a tweet by Mac security researcher Patrick Wardle with an animated GIF showing the attack in action. The calculator app popping up means a remote attacker has taken full control of the machine. (Wardle also wrote an in-depth blog post about how the flaw can be abused.)
PoC.gif 🔥 pic.twitter.com/xpKq5Cjue0April 26, 2021
Update macOS right now
Owens quickly informed Apple of the bug. Cupertino yesterday (April 26) released macOS Big Sur 11.3 with a patch to squash the bug, along with several other fixes.
The new macOS Big Sur 11.3 update can be freely downloaded on all eligible Macs using the Software Update section of System Preferences.
If you use a macOS machine then we suggest you update it as soon as possible. It's particularly important as the zero-day flaw is actively being exploited.
Actively exploited bug
It tends to be the case that zero-day flaws are discovered and patched before they're exploited. But in this case the bug has been harnessed by hacklers.
Security firm Jamf Protect reported that the flaw has been actively exploited since January 9, 2021. Shlayer, an infamous piece of macOS malware, was the preferred route of attack by cyber-attackers using the zero-day vulnerability.
Jamf's security teams observed the "exploit being used in the wild by a variant of the Shlayer adware dropper."
Like most avenues of attack that deliver adware payloads, the malware was deployed to earn money for crooks through fake clicks and bogus advertisement views.
Despite the findings from the research, it's still unclear just how many machines were affected overall, and it shows just how quickly hackers can and will capitalize on exploits in the wild to earn money.
The advice, as always, is to never download anything from untrusted sources and always ensure your system is up-to-date with the latest OS version. But even then, it's not always enough to deter a sophisticated and determined hacker intent on pillaging access to your system.
More: Chrome and Edge hacked by new zero-day flaw — what to do
Luke is a Trainee News Writer at T3 and contributor to Tom's Guide, having graduated from the DMU/Channel 4 Journalism School with an MA in Investigative Journalism. Before switching careers, he worked for Mindshare WW. When not indoors messing around with gadgets, he's a disc golf enthusiast, keen jogger, and fond of all things outdoors.
 Club Benefits
Club Benefits






