Your Wi-Fi Router Is Under Attack. Update It Now
A new malvertising campaign attacks 166 home Wi-Fi router models by taking advantage of brand-specific flaws. The fix is not easy to find.
This hasn’t been a good week to own a home or small office Wi-Fi router. First, a huge vulnerability strikes Netgear devices; now, a new malvertising campaign is attacking at least 166 models from multiple manufacturers.

Unfortunately, we don't know the names of most of the routers. Until we do, every administrator or owner of a home or small-office router should assume the device is vulnerable and should update the firmware immediately. Otherwise, this could effectively spell the end of your privacy and security online.
The firmware update process may be cumbersome for the average user, but we'll explain how to do it in a minute. Because the malware exploits known flaws, implementing recent firmware patches should fix the problem.
MORE: Your Router's Security Stinks. Here's How to Fix It
The consequences of a hacked router are dire. Since your router is your home’s gateway to the Internet, anyone who finds a way to access it can monitor all of your internet traffic, tap into your usernames and passwords, draft your systems into a botnet, or just redirect all of your searches to malicious pages. You could factory-reset your router every morning to oust possible attackers, but that's not much fun.
Five known infected models
There's evidence that the malware targets 166 distinct router models, but only a handful can be identified:
- D-Link DSL-2740R
- COMTREND ADSL Router CT-5367 C01_R12
- NetGear WNDR3400v3 (and likely other models in this series)
- Pirelli ADSL2/2+ Wireless Router P.DGA4001N
- Netgear R6200
Until we get a comprehensive list, assume that your model is compromised.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
How to update your router's firmware
Router firmware isn’t like Windows Updates; it generally doesn’t update automatically, and users are not assiduous about checking for new versions. The process tends to be a little complex, involving logging into your router’s software and trying to figure out where the manufacturer hid the update option.
With 166 routers (and maybe more) affected, we can't give a comprehensive breakdown of how to update every router’s firmware. But the following basics should take care of most models. (There don’t appear to be any exploits in the DNSChanger malware that target routers with fully updated firmware.)
-- Start by logging into your router's administrative interface and looking for an easy update mechanism. Some brands, such as Apple, have dedicated desktop applications that manage and update routers.
-- If you don't know how to access the administrative interface, dig out the instructions and look up how.
-- If you can't find an update mechanism in the administrative interface, then visit your router manufacturer’s website. Search for firmware updates regarding your particular model; if you find them, there should be instructions on how to download and install the new firmware.
In the second-worst-case scenario, you'll have to download something to a Windows PC, then physically connect the PC to your router with a networking cable, but the rewards will be well worth it. In the worst-case scenario, the manufacturer won't have pushed out an update for years, and you will need to consider buying a new and safer router.
How the attack works
Details about the malvertising scheme comes from the enigmatic French security researcher known as Kafeine, who wrote them up in a blog posting for Proofpoint, a Sunnyvale, California-based security firm. Malefactors buy ad space on legitimate websites, then fill ads with a subtle bit of malicious code. The code determines whether the unsuspecting web page viewer is on a home or small office Wi-Fi network, and then the real fun begins.
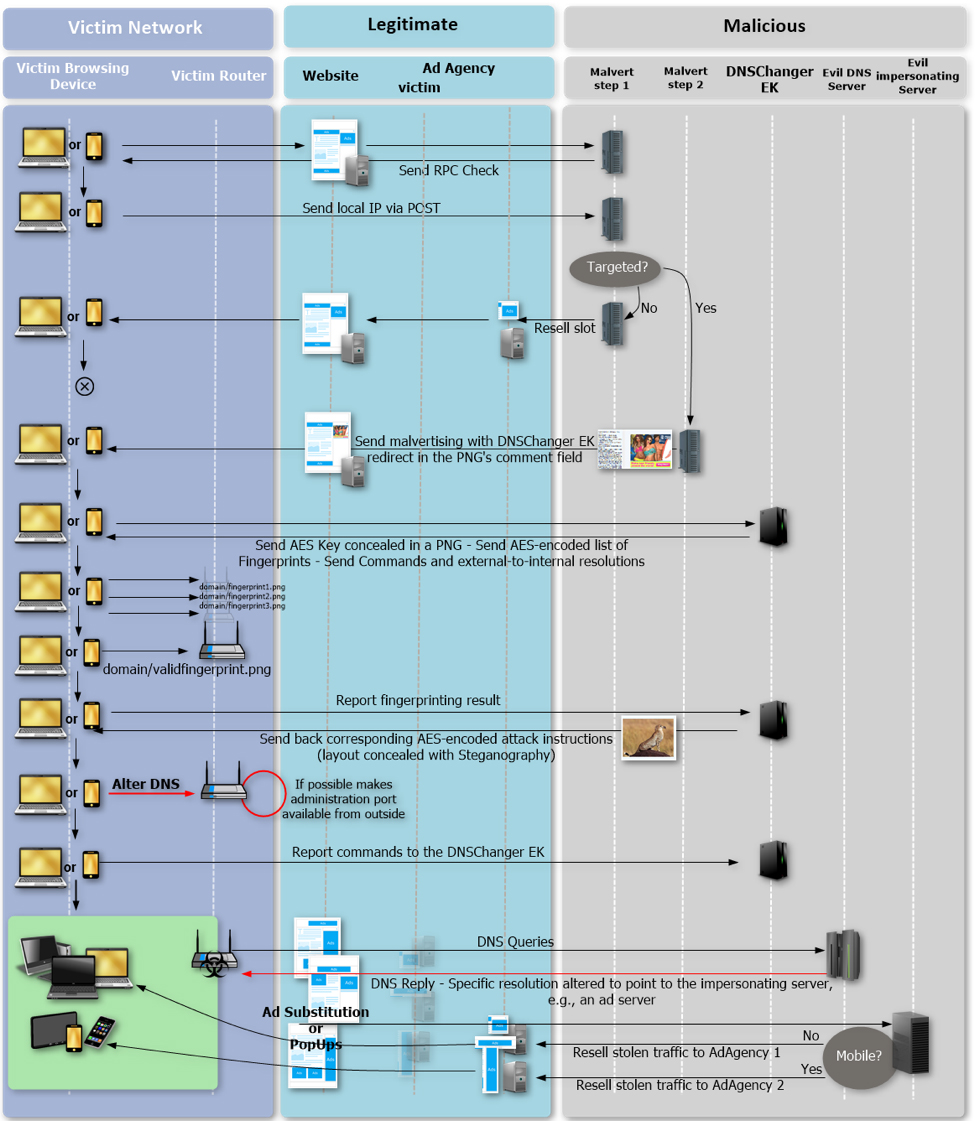
What happens next is fairly complicated, but basically, another ad is shown, this one containing the DNSChanger browser exploit kit -- a piece of malware that works on Windows and Android and can penetrate a web browser's defenses as soon as the viewer loads a web page. (If a potential victim is on an large business network, nothing of interest happens and a regular ad is sent.)
DNSChanger determines which model of router the victim is using, then looks for an exploit that matches the router. If there's no known exploit, the malware simply tries default administrative credentials instead, which will work if you didn't change your router's username and password when you first set it up. (There's no known connection between this malware campaign, which started in late October, and the vulnerabilities found last week in Netgear’s Nighthawk routers.)
What happens if the attack succeeds
If there is an exploit, the malware hijacks the router, and the criminals behind this malvertising campaign get to control your internet activities. Everything you do online -- shopping, banking, email, gaming -- may be affected, on every internet-connected device you own.
While the initial attack gets at routers through Windows or Android devices, hijacking the router means that your Macs, iPhones, gaming consoles and smart-home devices are also no longer safe.

Marshall Honorof was a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.
 Club Benefits
Club Benefits





