Peloton fixes bike-hacking flaw — how to make sure your model is safe
Flaw would let attacker seize full control of your ride

Exercise-equipment maker Peloton recently fixed a software flaw in its Bike+ and Tread models that could have let an attacker with physical access to the machines gain complete control. The attacker could then have spied on the Peloton user with the built-in camera and microphone, or could have installed malware on the Peloton machine itself.
"An unsuspecting gym-goer taking the Peloton Bike+ for a spin could be in danger of having their personal data compromised and their workout unknowingly watched," warns a blog post by McAfee's Advanced Threat Research team, which discovered the security flaw.
- Peloton data leak exposes users' personal data
- The best exercise bikes for your home
- Plus: Windows 11 leaks in full online — here's your first look
All affected Peloton units should have received an over-the-air security update earlier this month that fixed the flaw and took the software to version PTX14A-290.
"If you own a Bike+ or a Tread, we recommend that you log into the tablet on your device," says a Peloton blog post about the issue. "If you're not already on the latest software, you will be immediately required to update your software upon logging in."
How to make sure your Peloton Bike+ or Tread is updated
To make sure your Peloton Bike+ or Tread model has the update, follow these instructions, as detailed on Peloton's support page. The Peloton Bike and Tread+ models are not affected.
1. Tap Settings in the upper-right-hand corner of your Peloton screen, then tap Device Settings in the pop-up menu.
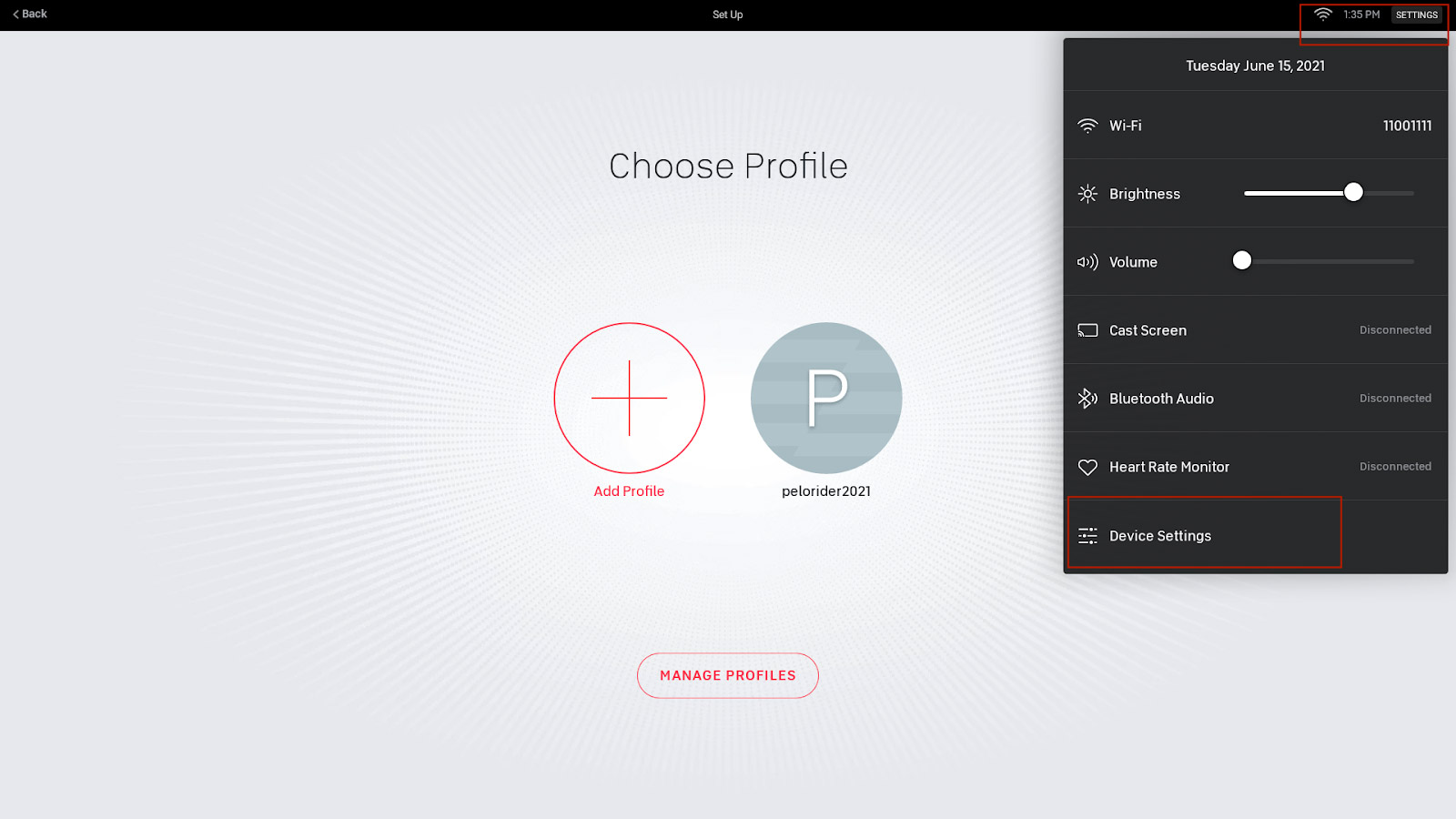
2. Tap System in the Settings screen.
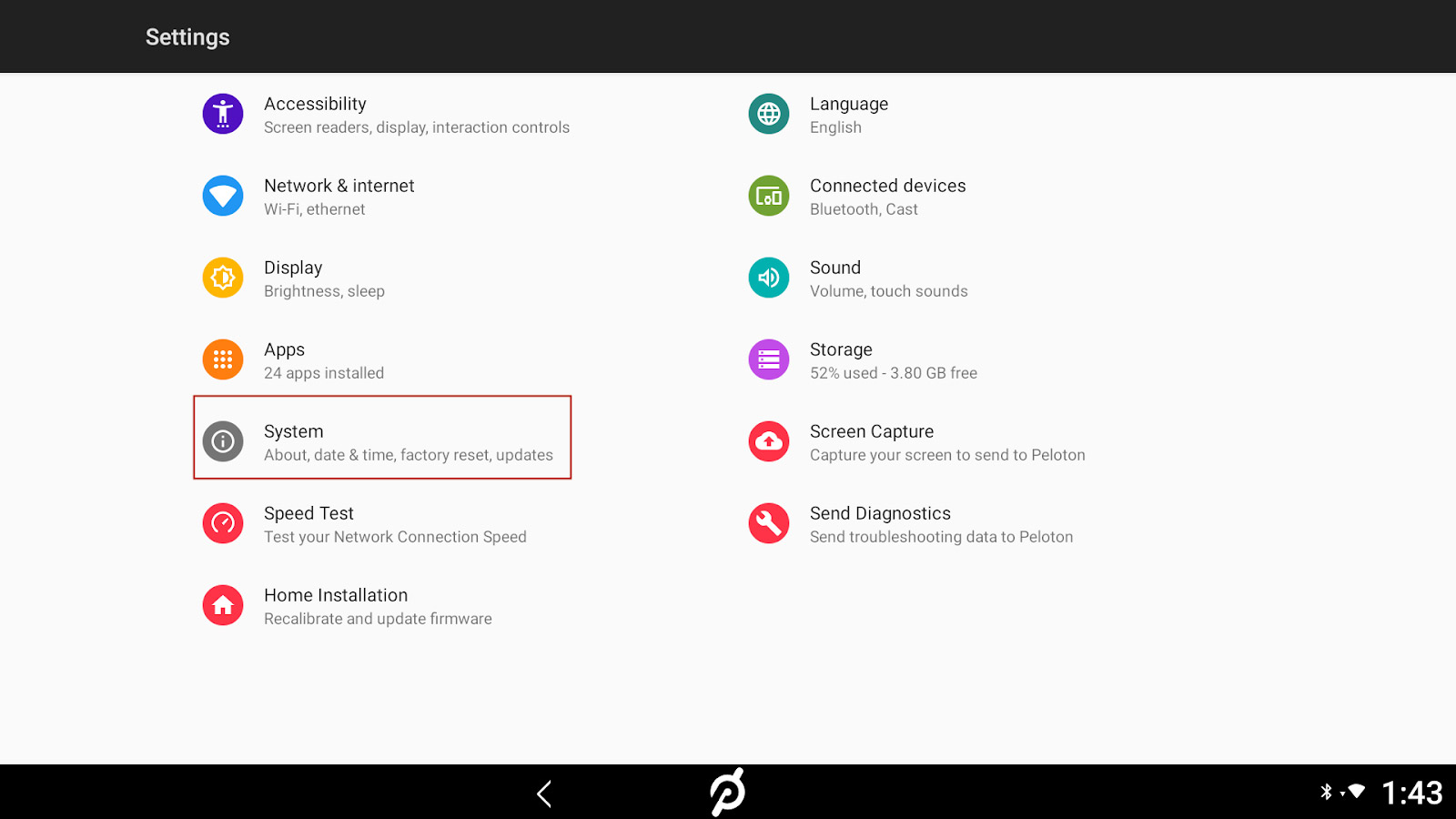
3. Tap System Updates in the System screen.
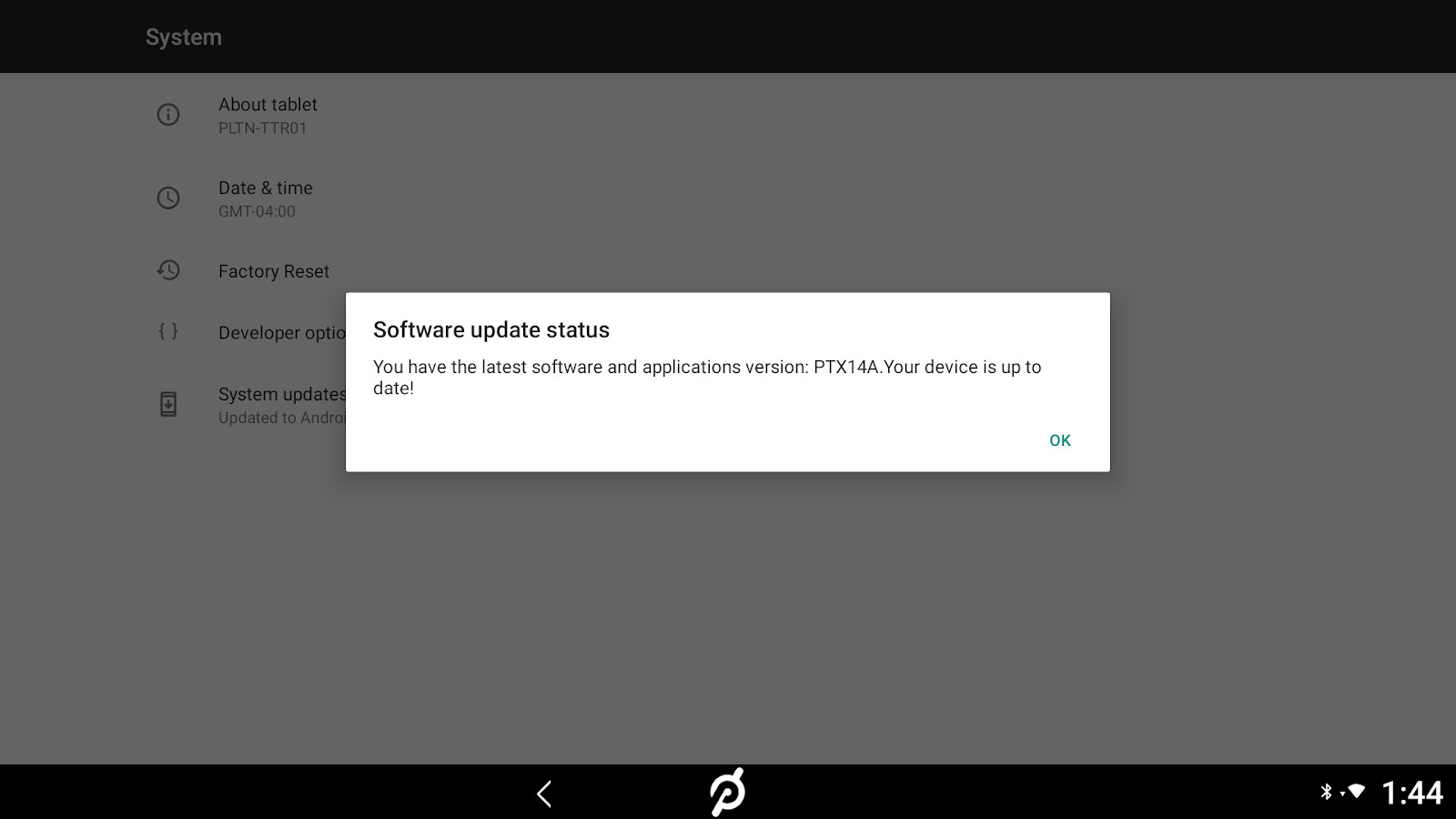
A dialogue box will pop up that tells you either that your device is up-to-date, or that an update is available. In the latter case, you will be prompted to begin the update process.
The Bike and Tread+ models, which are not affected by the flaw being discussed here, can be updated in more or less the same way, except that in Step 2 you tap About Tablet rather than System.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
What happened with this Peloton security flaw
Without getting too far into the weeds, the McAfee hack was rather simple and was found via trial and error. (The technical details are in this separate McAfee blog post if you're interested.)
The touchscreens on all Peloton models are Android tablets with a modified interface. McAfee found that Peloton had indeed taken the necessary security precautions and locked the tablet bootloaders so that the Android operating system could not be tampered with.
Normally, that would mean the end of the line for an attacker. Nonetheless, the McAfee researchers were able to partly boot the tablets into a different version of Android by plugging in a USB-C drive loaded with a custom bootloader and accessing the Android tablet's recovery screen by pressing the power and volume-up buttons at the same time.
That method resulted in a black screen, but it showed that the bootloader-lock could be bypassed. So the McAfee researchers then grabbed an earlier Peloton firmware update, extracted a boot image, loaded it onto their USB drive and found they could boot the tablet from the USB drive.
From there, they were able to alter the Peloton boot image to add a "sudo" command, which grants temporary root access to any user on a Linux system, which Android is under the hood.
Root access lets the user get complete control of a system and have the power to install apps, change vital configurations or change the operating system itself.
Because the McAfee researchers were able to install their modified boot image on their Bike+ unit, they would have permanent, remotely accessible control over the machine. Here's a video of the end result.
A few big 'ifs'
This is obviously pretty serious, but there are a couple of caveats. First of all, the attacker needs a couple of minutes alone with the Peloton machine to carry out this attack. It can't just happen over the air.
Second, McAfee put forward the scenario of a criminal wandering around an empty gym sticking USB-C drives into random Peloton machines to hack them. But a Peloton spokesperson told us that the company "does not currently offer Peloton Bike+ or Tread for commercial use" — the very models susceptible to this flaw.
That does leave open the possibility of more private attacks involving Peloton machines sold to consumers. For example, the husband in that Peloton TV ad that went viral during the 2019 holiday season could have used this flaw to spy on his wife, or vice versa. But then again, either spouse could easily have spied on the other in a dozen other ways.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
