Worried about the 16 billion data breach? I've been hacked, and this is everything I did to fix it
Don't make the same mistakes I did

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
I have a confession to make: I used to reuse passwords.
It’s the number one security sin, but this was over a decade ago and I didn't know about the best password managers yet. This was a huge mistake. And with news that researchers just uncovered a database of 16 billion records, including passwords and other sensitive data, this could be a problem for you, too.
Details are scarce — we don't know where the data came from or who is behind it — but the most important thing is try and look past the feelings of anxiety, and take practical steps to improve your security, and I should know; I've been hacked before.
In 2013, Adobe was hacked and the attackers got a list of 153 million usernames and passwords. These passwords weren’t encrypted which allowed people to read them — they were stored in plaintext — so once the list was out, attackers had all they needed to target unfortunate Adobe users like me.
It was a stressful time and given that your email account houses some of your most sensitive information, once they had access to that account, they could reset your passwords to lock you out of other websites and services too. But I kicked them out and learned pretty quickly how to protect myself from then on.
More than a decade later, there are still attackers trying to get into my account, but there’s an important difference — they can’t now. So, now feels like the perfect moment to share how I learnt from my mistakes and how you can easily improve your security to stop the same thing happening to you.
How to protect your accounts: in short
- Don't reuse passwords
- Enable Two-Factor Authentication
- Delete unused accounts
- Sign up to Have I Been Pwned
- Start fresh
1. Don’t reuse passwords
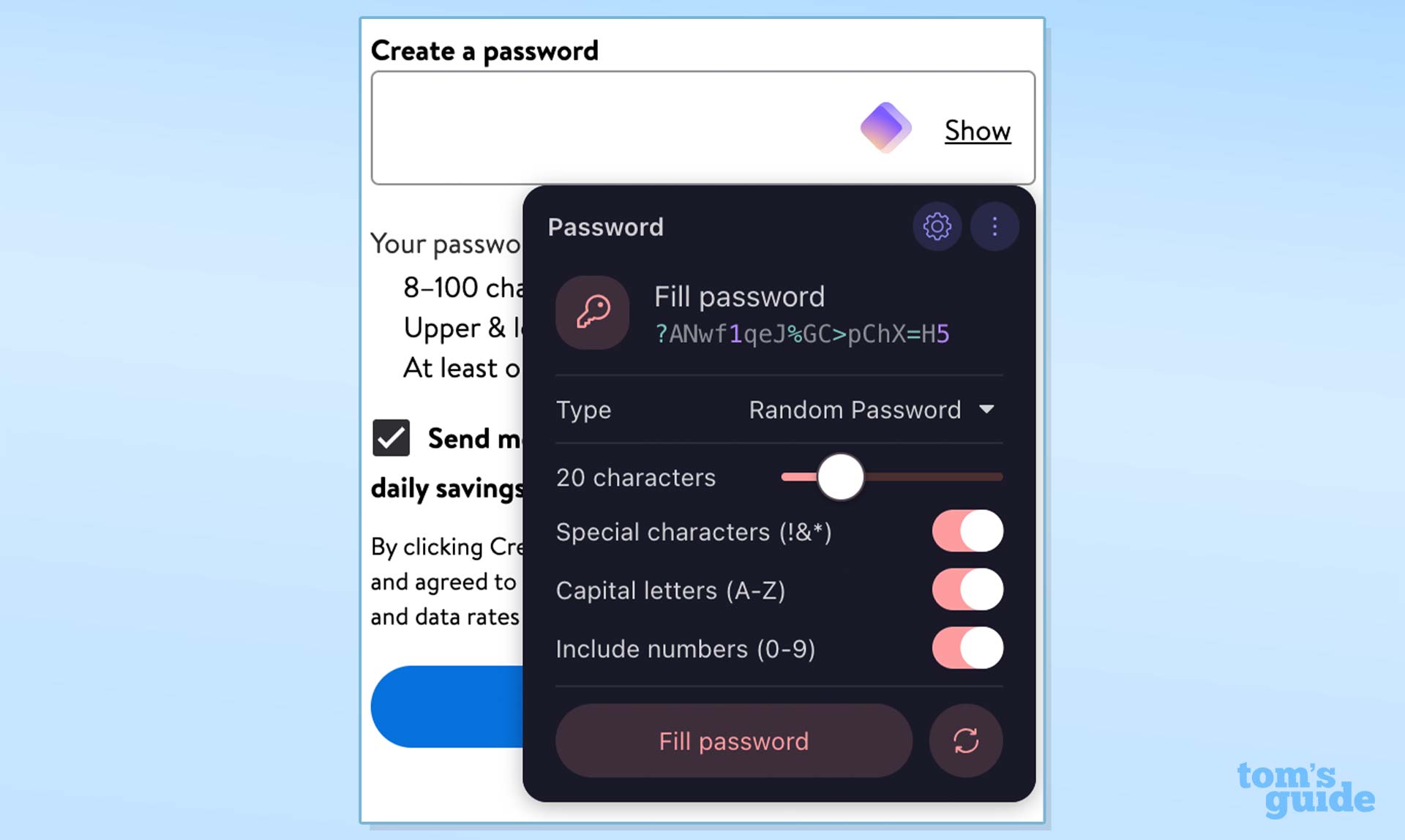
Okay, you’ve probably already guessed this one from earlier in the story, but one of the major issues I had when the Adobe hack happened was I was using the same password on multiple sites. So it was pretty easy for the attackers to use credential stuffing and break into my other accounts too.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Like others, the reason I did this is because there are a lot of passwords to remember! I obviously didn’t want to get locked out of an account, and password reset forms aren’t always that reliable, so I decided that the best course of action was a simple, easy to remember password I could use on all sites.
I thought it was secure as it has numbers, capital letters and symbols. It wasn’t quite as risky as using “password” or “passw0rd,” but it wasn’t far off.
The best way to avoid this issue is to use a password manager like 1Password or Proton Pass (my preferred option). These store all your credentials in one place securely and can generate long, complex passwords for you to use, but never need to remember.
Most have apps for your browser, computer and smartphone too, so you always have access to your passwords.
- Data breaches used to be big news because they rarely happened. But with this new leak, which could be new or repackaged from older hacks, and with more automated or AI-based tools at the hacker's disposal, it's getting even quicker and easier for them to try these details on all of your accounts.
2. Enable Two-Factor Authentication
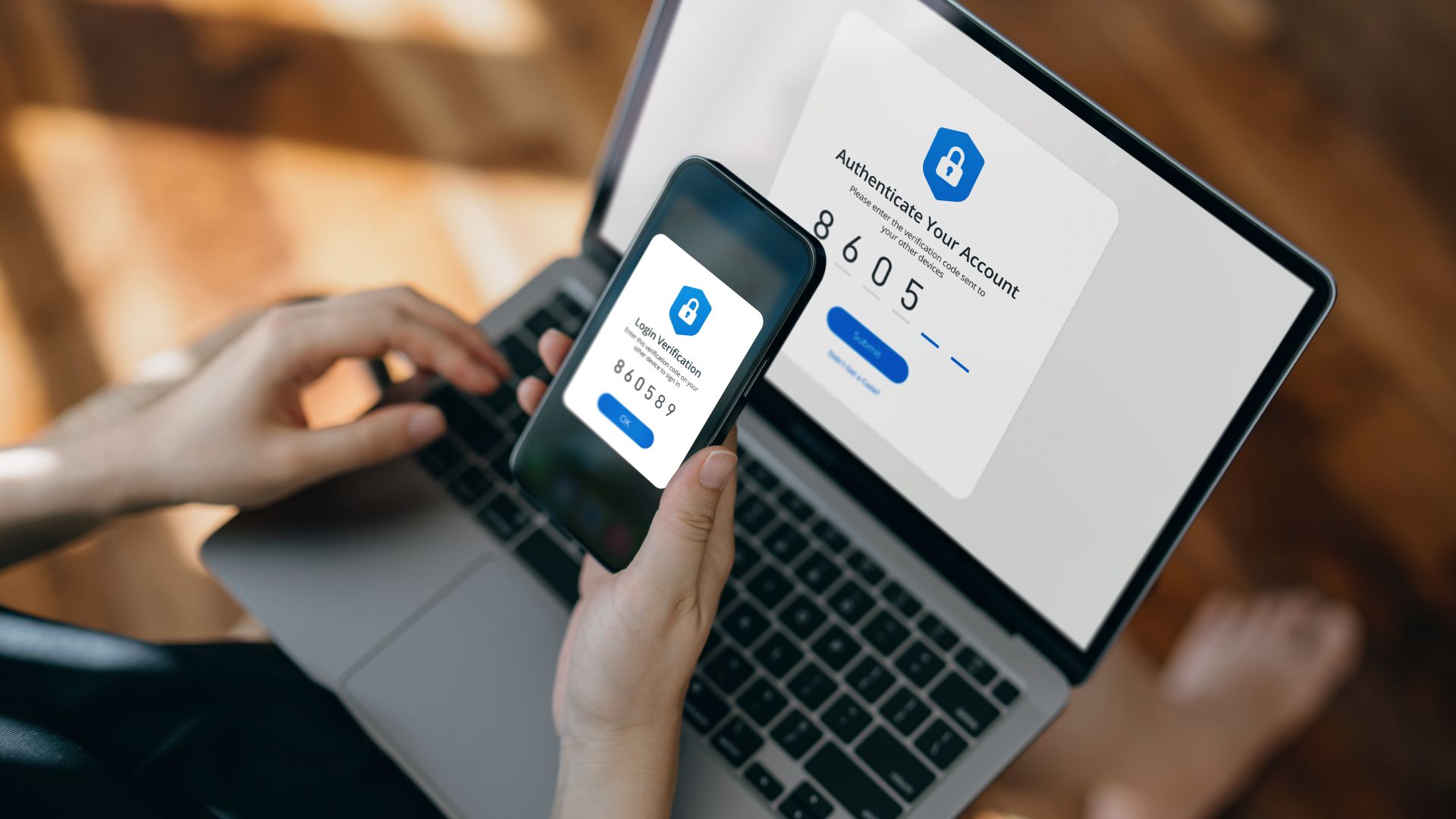
One of the reasons attackers can get into some accounts so easily is that once they have your username and password, they can just sign in as if they’re you. But what if you had a unique token to show that you are really you, and without it, someone can’t access your account?
That’s the idea behind two-factor authentication (2FA). If you haven’t used this on your personal accounts, you may have done at work. It comes in various forms, but the most common are six-digit codes generated by an app or sent to your phone by SMS.
Requiring one of these codes along with your login details shows that not only do you know the username and password, but you have a known physical item with you that helps to verify it’s really you trying to log in.
This is one of the most effective ways to cut attackers off from your accounts, even if your passwords gets leaked. After I set this up for my Microsoft account (using the free Authy app on my smartphone), hackers kept trying to get into my account, but they never can. It’s an easy way to shore up your defences.
I only know this, though, because Microsoft has a really useful Account Activity page which shows when and where sign in attempts come from and whether they were successful.
If you want even more security for your online accounts, you may also want to consider using a physical security key instead.
3. Delete unused accounts
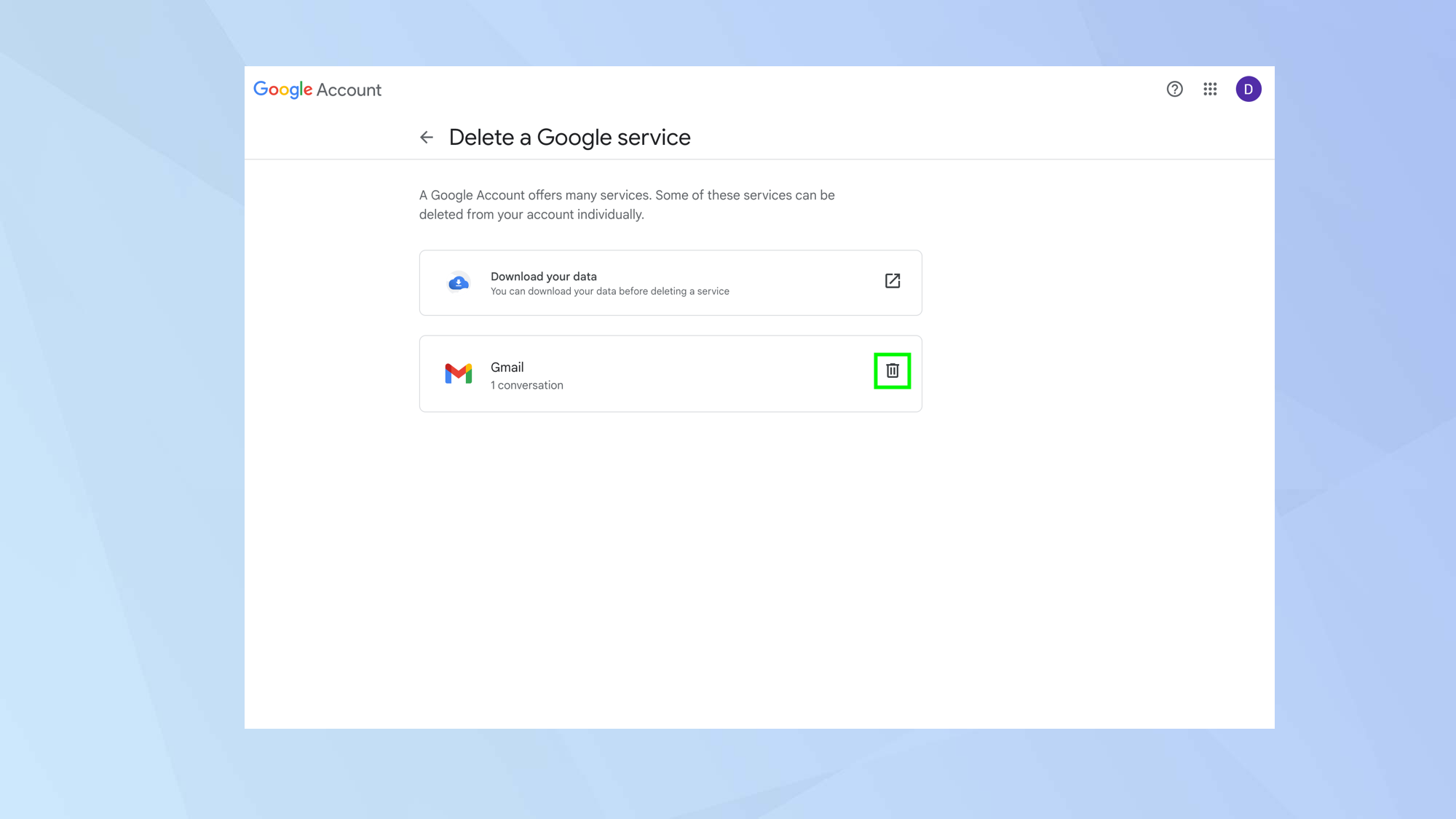
There’s not really a lot to say on this one: if you don’t use an account anymore, delete it. It’s good to have a cleanup from time to time, and getting rid of old or dormant accounts means less clutter and fewer opportunities for your data to go awry.
Not every site gives you an easy “Delete account” button, but if you head to the company’s privacy policy (usually linked in the footer at the bottom of a website), you can find a privacy contact and send an email to request they delete your data.
Plus, in the years since I was hacked, authorities around the world have strengthened privacy regulations, so in many places, there’s now a legal obligation for the business to comply with your request. This is why you can do things like delete your Google account so easily these days.
4. Get notifications from Have I Been Pwned
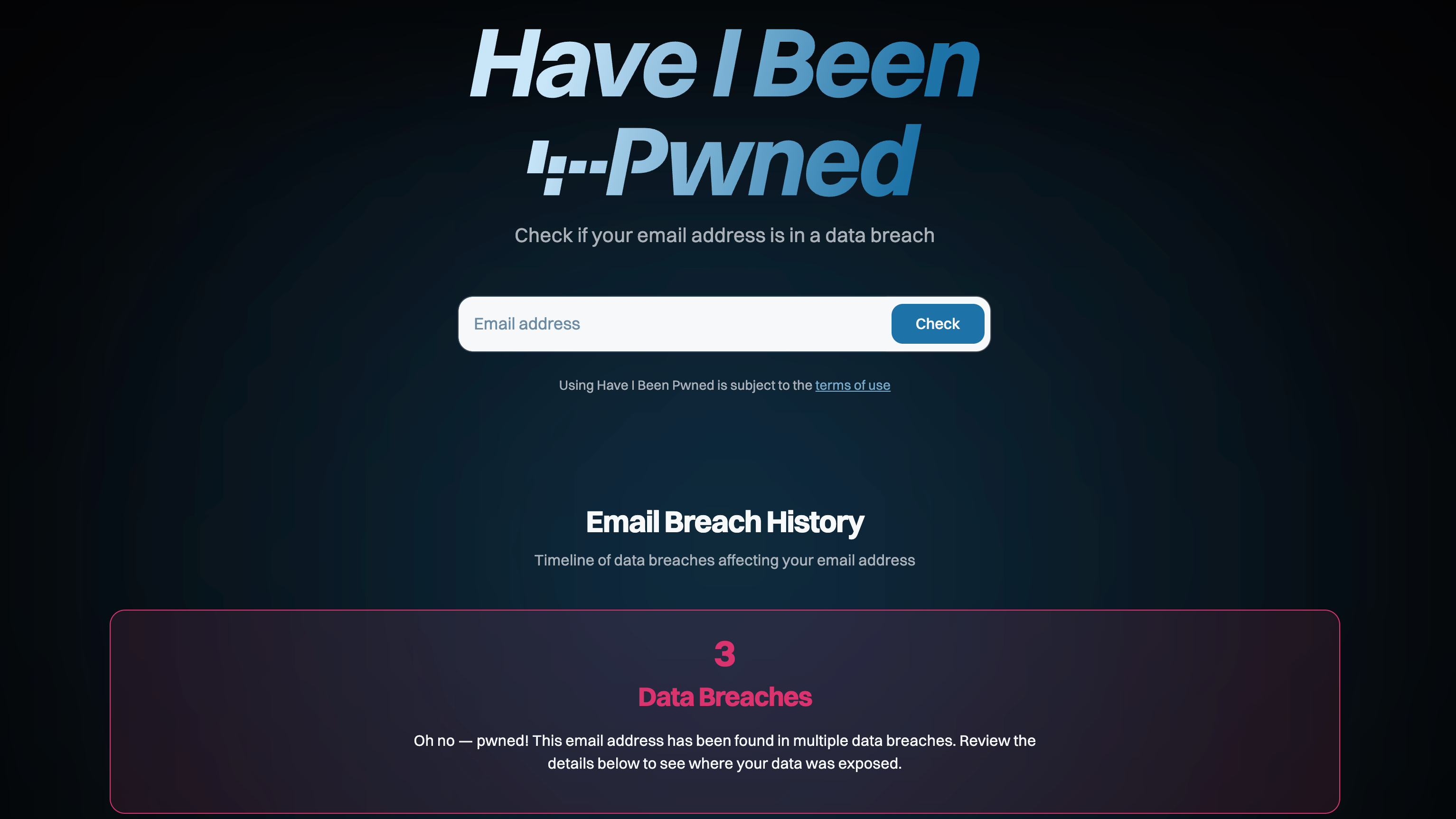
Yes, Have I Been Pwned is a strange name for a security website (pwn is hacker slag for gaining unauthorized access), but it is easy one of the best free security resources for protecting your accounts. Troy Hunt, the man behind the site, collates data from hacks and can send you alerts when your account is involved.
This is how I would later find out my details were leaked in the MyFitnessPal, NetGalley, LinkedIn and Last.fm breaches, alongside many, many more — usually random sites I had no memory of even signing up to (and had probably stored my details for at least a decade without my realizing).
It’s easy to use and gives you a very early heads up when you need to change passwords on a hacked account. Hacked data can be messy and difficult to verify, so if you want to check if a specific password has been compromised, there’s a searchable Pwned Passwords database too.
As things stand right now, Have I Been Pwned hasn't loaded this database into its system (the researchers said the data was only exposed briefly, so it's not publicly accessible, and HIBP does thorough verification checks before adding any breach).
- You can perform a manual check of your email address on Have I Been Pwned, but I recommend using the Notify Me service to get an email notification as soon as a hack includes your details.
5. Consider a clean start
By the time hackers were knocking at my virtual door, I’d used my Hotmail email account for almost 15 years. It had built up a long history, and now it was a target, I decided it was time for a fresh start. That’s when I switched from Outlook to Gmail, and more recently, to Proton Mail (which we rate as the best email service for security).
It was a lot of work — I won’t lie to you about that. Going through every account that I had, changing the email address, creating a new password, and setting up 2FA was a big time suck. But it was worth it. My current address has only been involved in one leak (thanks, Twitter), and so there’s less of my data floating around.
Plus, starting from scratch meant that I could make more deliberate security choices. I became more mindful which services I chose to sign up to, where I put my details and how I protected the account. I rarely use my actual phone number unless I have to, and I make sure I opt out of marketing lists.
These aren’t fool-proof techniques that’ll keep your account secure forever; your data is at the mercy of whichever company controls the account. But it does mean I’ve had fewer security issues, I don’t need to worry that someone will get into my account (as they can’t) and I barely get any spam emails now too.
- While it's always a good idea to get rid of unused email subscriptions, risks that way lie too. Some email unsubscribe links direct you to a malicious page to either steal data or download malware. Instead, click the "Unsubscribe from newsletter" buttons that your email provider puts at the top of the email.
More from Tom's Guide
- New AT&T data leak links previously exposed info to Social Security numbers, birth dates
- Meta called out for tracking Android users across the web without their consent — what you need to know
- Microsoft Authenticator will shut off the password autofill feature in July — here’s how to save them

James is Tom's Guide's Buying Guide Editor, overseeing the site's buying advice. He was previously Fitness Editor, covering strength training workouts, cardio exercise, and accessible ways to improve your health and wellbeing.
His first job at as a sales assistant in a department store, and this is where James learned how important it is to help people make purchasing decisions that are right for their needs, whether that's a fountain pen to give as a gift or a new fridge for their kitchen.
James is an advocate for sustainability and reparability, and focuses his reviews and advice through that lens to offer objective insights as to whether a specific product or service will be right for your needs.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits










