Your Mac may be vulnerable to hackers, and it can't be patched — here's why
The T2 security chip inside your Mac may be at risk, and the exploit can't be patched right away
Remember the days when a big selling point of Macs was that they allegedly couldn’t get viruses and weren't vulnerable to other security flaws? That time is long gone, and these days there are plenty of ways to target Macs and their users.
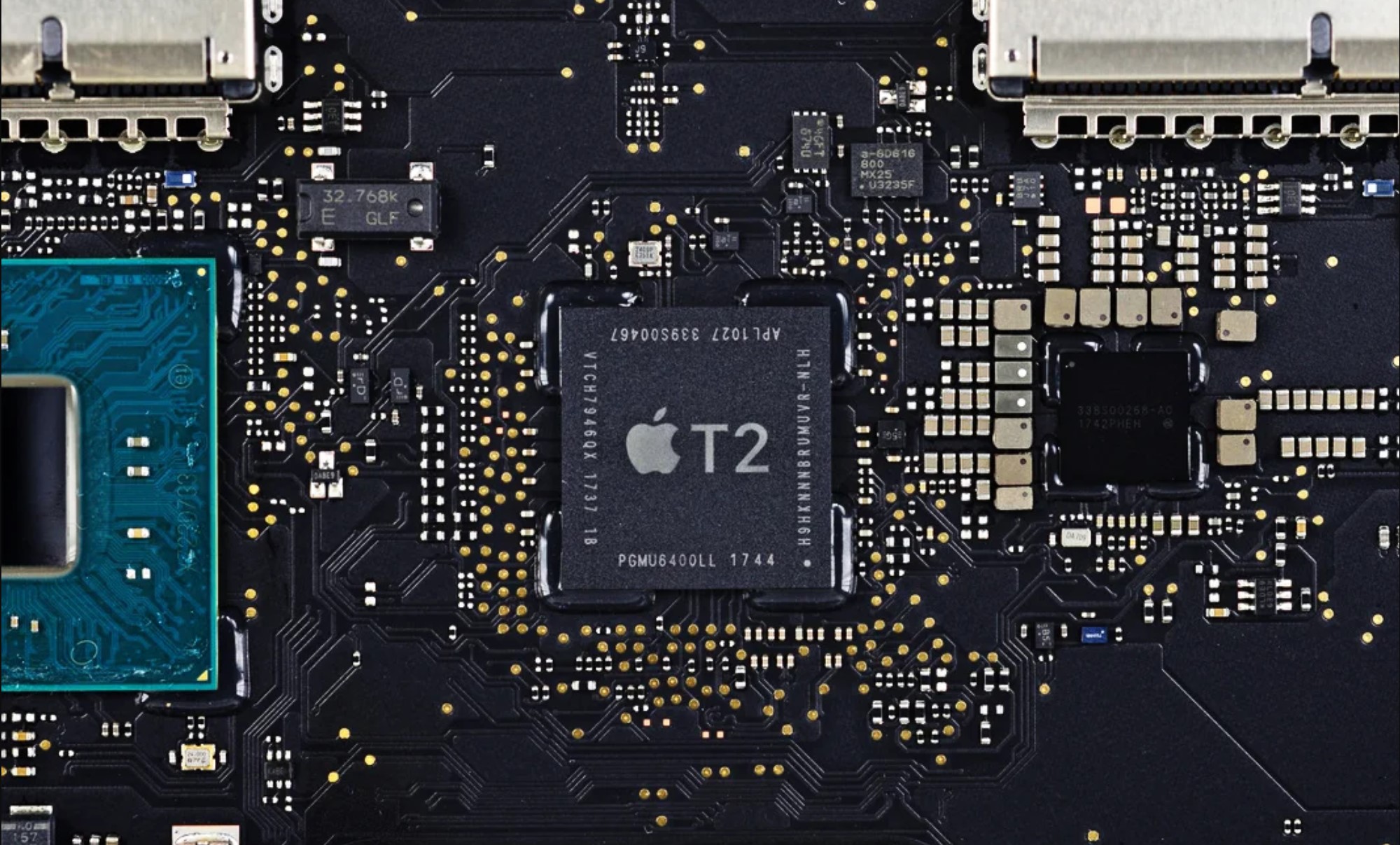
The latest way is a bit of a doozy, and it involves hacking Apple’s T2 security chip to get full access to a locked, powered-down Mac. The worst part, though, is that it doesn't seem that this problem can just be patched away.
- Macbook Air vs MacBook Pro: Which one is right for you?
- The best Mac antivirus software to keep that Apple polished
- Plus: Stunning PS5 Spider-Man Design is the one we really want
The exploit itself actually involves using two jailbreak exploits, checkm8 (aka checkra1n) and Blackbird, which have previously been used for jailbreaking iOS devices. The exploit works because the T2 chip is based on the A10 chip used in the iPhone 7.
Some well-known Apple hackers seem to have known of this chained exploit for at least a month, judging by Twitter chatter found by ZDNet's Catalin Cimpanu.
With @checkra1n 0.11.0, you can now jailbreak the T2 chip in your Mac. An incredible amount of work went into this and it required changes at multiple levels.There’s too many people to tag, but shoutout to everyone who worked on getting this incredible feature shipped.September 22, 2020
checkm8 + blackbird and the T2 SEP is all yours...September 5, 2020
Belgian security consultant Niels Hofmans, writing on his blog yesterday (Oct. 5) as ironPeak, explained how he was able to jailbreak the T2 chip by running 0.11.0 of the checkra1n software via a USB-C connection while the Mac was booting up.
The jailbreak left the T2’s debugging interface open to the user, allowing them to enter Device Firmware Update (DFU) without any authentication. It also means hackers who get their hands a Mac can get root access to the chip to modify and take control of anything running on the device — including encrypted data.
"Normally the T2 chip will exit with a fatal error if it is in DFU mode and it detects a decryption call, but thanks to the blackbird vulnerability by team Pangu, we can completely circumvent that check in the SEP and do whatever we please," Hofmans wrote.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
He also included instructions and code to carry out the exploit in case you want to try it yourself.
Semi-permanent exploit
The silver lining is that the jailbreak will not survive a reboot of the Mac. The bad news is that during the jailbreak, the attacker can do pretty much anything on the Mac, including reading encrypted files, planting malware or spyware or installing remote-access software.
But Hofmans said it would be possible to create a malicious USB-C cable designed to automatically run the exploit on boot whenever it's attached to a Mac. Plus, since it’s a hardware issue, it’s not the kind of problem Apple can patch away.
"If the attack is able to alter your hardware (or sneak in a malicious USB-C cable), it would be possible to achieve a semi-tethered exploit," Hofmans wrote. "This is a perfectly possible attack scenario for state actors. I have sources that say more news is on the way in the upcoming weeks. I quote: be afraid, be very afraid."
The exploit does require physical access to a Mac rocking the T2 chip (i.e. any Mac sold after 2018), which significantly lowers the risk for ordinary users. After all, if you were a hacker that’s going to bother to try and infiltrate someone’s machine this way, you better be sure they have something worth accessing.
But this does mean any Mac that’s been left out of your sight — such as in your hotel room, in a cafe or at a border crossing — is potentially at risk, and it’s another example of why you should never plug random things into your machine without verifying what it is first.
What (little) you can do about this attack
If you are concerned your Mac has been hacked this way the only solution is to reinstall the T2 chip’s operating system, BridgeOS. However, that procedure is not for the technically illiterate, and it doesn't fix the overall vulnerability.
"Apple cannot patch this core vulnerability without a new hardware revision," Hofmans wrote.
He did add that the Apple Silicon chips Apple is introducing in 2021 should not have this problem.
Hofmans also said that anyone who thinks they’re at risk of being targeted should “verify your SMC payload integrity using .e.g. rickmark/smcutil and don't leave your device unsupervised.”
Hofmans wrote that he reached out to Apple about this exploit on August 18, but has yet to receive a response despite checking back four times and even cc'ing Tim Cook. He also said he tried to reach out to various news website and got no response (next time, try Tom's Guide!), so was making the exploit public.
Tom's Guide has reached out to Apple for comment, and we will update this story when we receive a response.

Tom is the Tom's Guide's UK Phones Editor, tackling the latest smartphone news and vocally expressing his opinions about upcoming features or changes. It's long way from his days as editor of Gizmodo UK, when pretty much everything was on the table. He’s usually found trying to squeeze another giant Lego set onto the shelf, draining very large cups of coffee, or complaining about how terrible his Smart TV is.
