Tom's Guide Verdict
Trend Micro’s Maximum Security package provides many useful extra features, acceptable protection and fast scanning for malware, although it tends to rack up too many false positives and can place a heavy burden on a system.
Pros
- +
Fast system scanning
- +
Adequate malware protection
- +
Secure browser for online shopping
Cons
- -
Too many false positives on some tests
- -
No Windows webcam protection
- -
Heavy performance hit during scanning
Why you can trust Tom's Guide
Malware protection: Adequate
System impact, background: Light
System impact, scans: Heavy
Windows compatibility: Windows 8.1, 10, 11
Anti-theft: No
Backup software: No
File encryption: Yes
File shredder: Yes
Firewall: No
Game mode: Yes
Hardened/secure browser: Yes
Parental controls: Yes
Password manager: Yes
Performance scanner: Yes
Ransomware rollback: Yes
System optimizer: Yes
Webcam protection: No
Virtual keyboard: No
VPN: Yes
Wi-Fi scanner: No
Support options: Business-hours phone, email, chat
Extra: Post installation email with all the details
With four different Windows-based antivirus suites, from the inexpensive AntiVirus+ Security to the flagship Premium Security, Trend Micro seemingly offers something for everyone. Each program provides good foundational defenses with the same underlying malware-detection and eradication technology, a hardened web browser and a game-friendly Mute mode, while Maximum Security includes extra security-minded features that range from file encryption to a password manager to identity protection. The flagship Premium Security adds virtual private network (VPN) access.
Its scanning for malware is fast, but it extracts a lot of system resources and its effectiveness is a step behind that of Bitdefender and Kaspersky by flagging suspect software first and asking questions later, resulting in frustratingly high false-positive rates. Plus, the company’s products lack webcam protection for Windows computers as well as an unlimited plan for large families.
Can Trend Micro Maximum Security’s mix of a password manager and cross-platform protection, including Chromebooks, and a secure browser make it a winner? Our Trend Micro review will help you decide if this is the best antivirus software for all of your devices.
Trend Micro review: Costs and what’s covered
Trend Micro doesn’t have a free scanner for malware, but each product can be used for a month before having to pay. Its entry-level Antivirus+ Security costs $40 and is a bargain with amenities like Mute Mode to prevent interruptions during gaming, movies or Zoom calls as well as the Pay Guard secure browser for more secure online banking and shopping. It covers a single Windows computer and can be found online for $20.
Trend Micro Internet Security extends the coverage to three Windows computers for $80 although is often as cheap as $40. It includes extra ransomware defenses, protection for email scams, parental controls and a social media scanner and system optimizer.
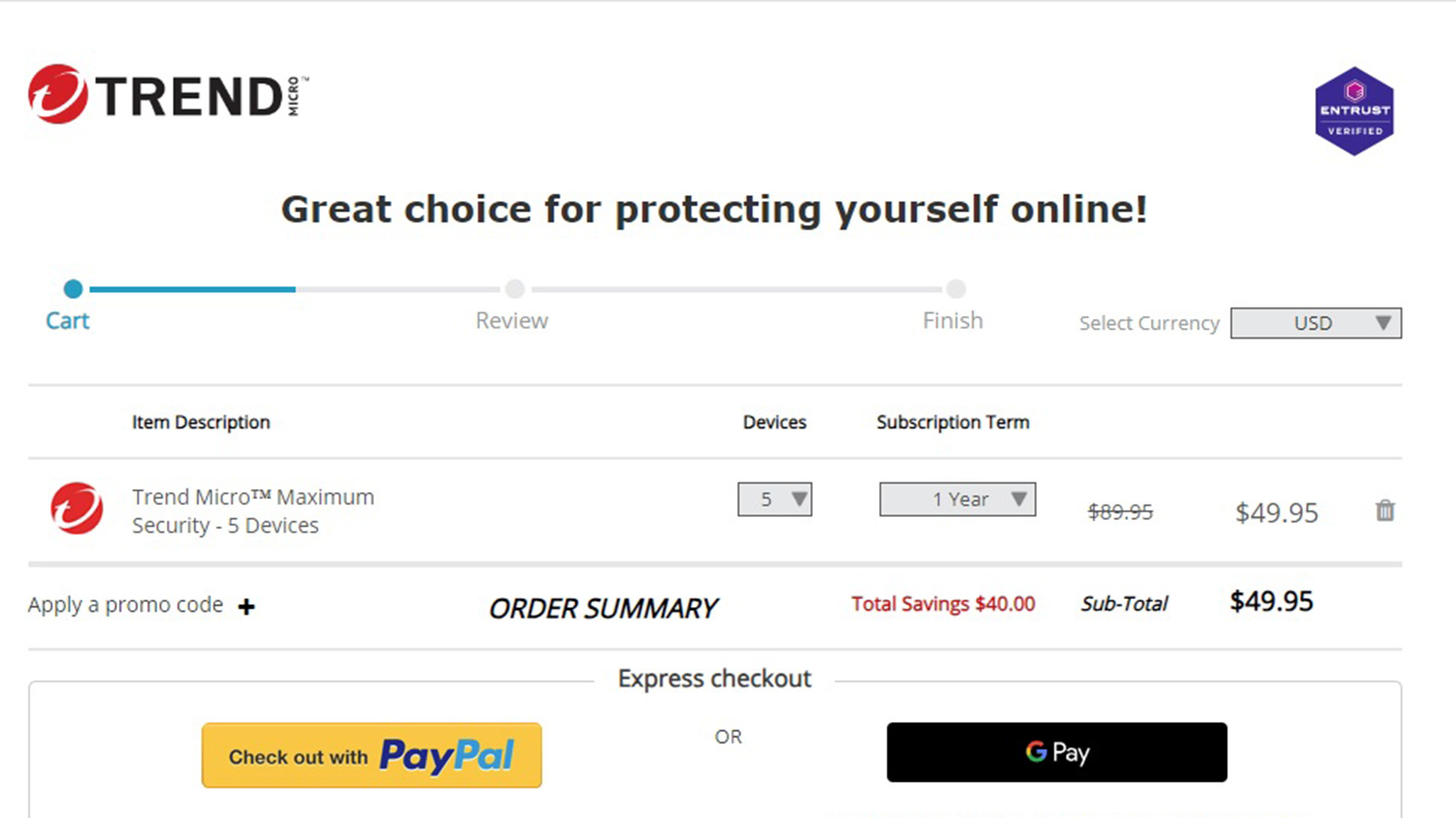
If you want to go beyond Windows computers to protect Macs, Androids, iPhones, iPads and Chromebooks, the $90 Maximum Security package covers any mix of five systems; it can be bought online for as little as $50. Maximum Security has a password manager that stores an unlimited number of log-in credentials. The Password Manager and mobile apps on their own cost $50 and $30 each, respectively.
Trend Micro Premium Security consists of Maximum Security for 10 systems with ID Security dark web scanning (for phones and tablets) and unlimited access to the company’s VPN for five users. Both are add-ons that require separate downloads and installations, however. It also includes 24/7 premium support, something we think all customers deserve. It costs $150 but shop around to get it for $60.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Trend Micro’s antivirus programs work with Windows 8.1 through Windows 11, and the top suites support macOS 10.14 or higher, Android 5.0 or newer, iOS 11 or later. Unlike many of its peers, Trend Micro software has compatibility with Chromebooks; with Chrome OS version 79 or higher.
Trend Micro review: Antivirus protection
All Trend Micro security programs start with the basics: scanning for known malware and monitoring system activities using heuristic behavioral analysis to spot the early signs of an attack. Anything suspicious gets uploaded to the company’s labs for analysis. If this is too much information, feel free to opt out of this data collection on the online portal.
To stay up to date with current threats, each protected system gets periodic downloads of new malware signatures, sometimes several times a day. Trend Micro has tens of millions of client devices in use.
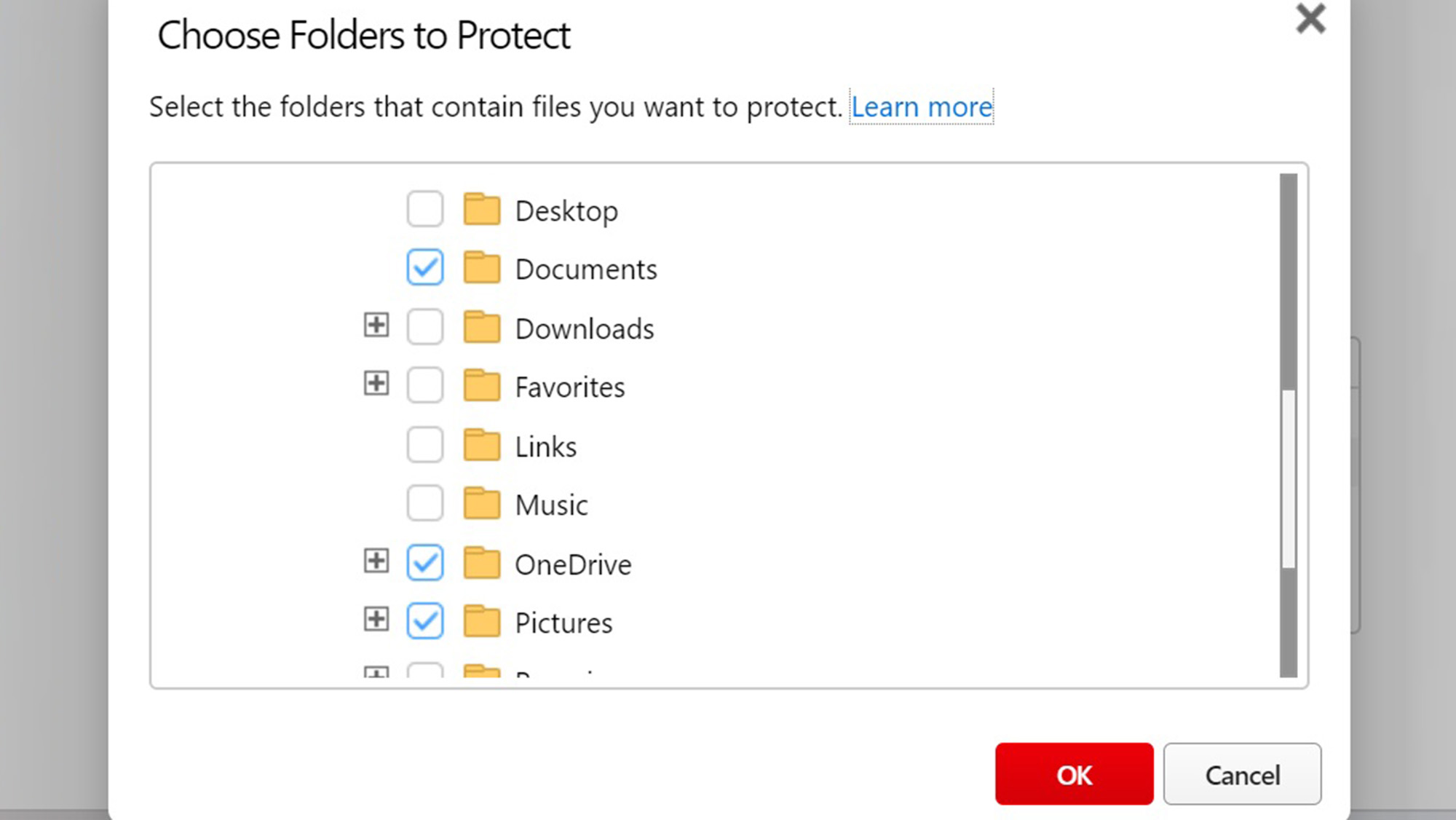
Trend Micro software has dedicated defenses against specific threats such as fileless malware that attacks a system’s memory, tech-support scams, phishing and cryptocurrency-mining malware. Meanwhile, Folder Shield protects key files from being encrypted by ransomware with the Documents, OneDrive and Pictures folders protected by default; it’s easy to add others.
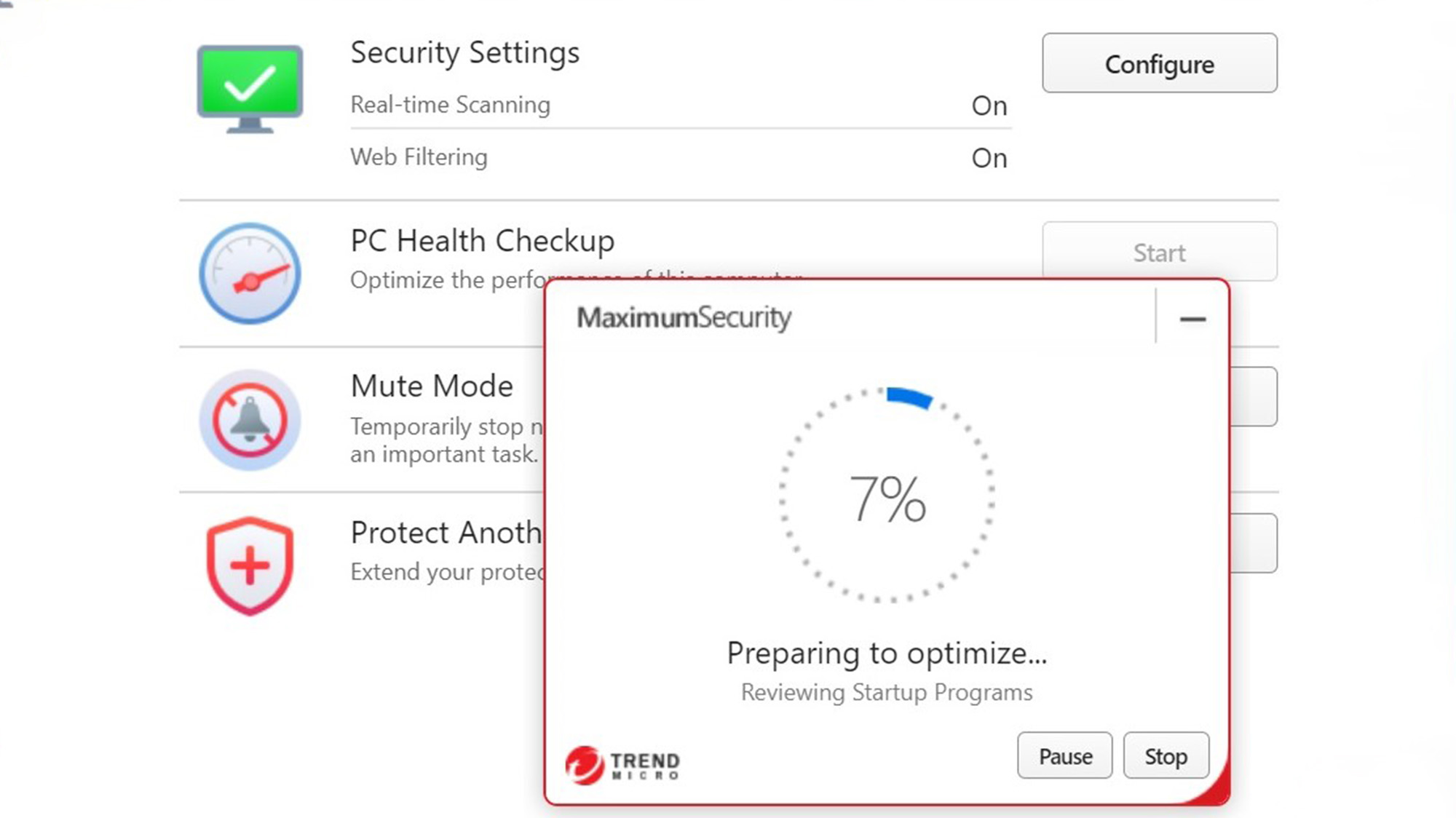
Meanwhile, the PC Health Checkup optimizes your system while flagging vulnerabilities, although it’s a not-too-subtle path to upgrade to the company’s $60 Cleaner One Pro. The included scanner took 37 seconds to go through my test machine and found places to cut duplicate and unneeded files.
It has Trend Micro’s Fraud Buster built in. The defense uses AI to warn of scams hidden in emails, while the browser extensions advise of known malicious websites. There are extensions for Google Chrome, Microsoft Edge, Internet Explorer, Apple Safari and Mozilla Firefox.
Finally, Trend Micro’s Rescue Disk can help recover a system that’s overwhelmed with malware. It’s downloadable from the company’s website and needs to be installed onto a CD, DVD or USB drive. It works with Windows computers but acts independently of the operating system to find pesky problems in hidden files, system drivers and the Master Boot Record (MBR).
Trend Micro review: Antivirus performance
Trend Micro’s Windows malware scanner, shared among all four of its security programs, does well in most third-party lab tests. On the downside, it can be overeager, racking up a huge number of false positives, which is annoying because it can cut into confidence that the program is accurate, efficient and dependable.
To start, the Trend Micro scanner found everything that AV-Test threw at it in the June 2023 testing round. That’s in accord with the others, which also had perfect capture scores. On the other hand, Trend Micro – along with Kaspersky, McAfee, Norton and Sophos – had no false positive results. By contrast, Bitdefender had five false positives while McAfee had a single incorrect identification of safe software as dangerous. ESET didn’t participate in this round of testing.
The pros and cons of Trend Micro’s scanner was shown with AV Comparative’s May 2023 survey. It was excellent with a 100% success rate at finding and killing all the dangerous software the group used. Bitdefender and Kaspersky matched this flawless score.
On the other hand, Trend Micro’s malware hunter was trigger happy, with a massive 39 false positives in this round of tests. That makes it potentially inaccurate and frustrating to use. The closest competitors were McAfee and Norton’s 99.6% rating, although the former had 13 false positives while the latter had 14 false positives, combined less than Trend Micro’s false positive score on its own. By contrast, Kaspersky and Bitdefender had 100% scores and only Kaspersky ended the testing without a false positive; Bitdefender had two.
Trend Micro does not participate in SE Labs malware testing.
Trend Micro: Security and privacy features
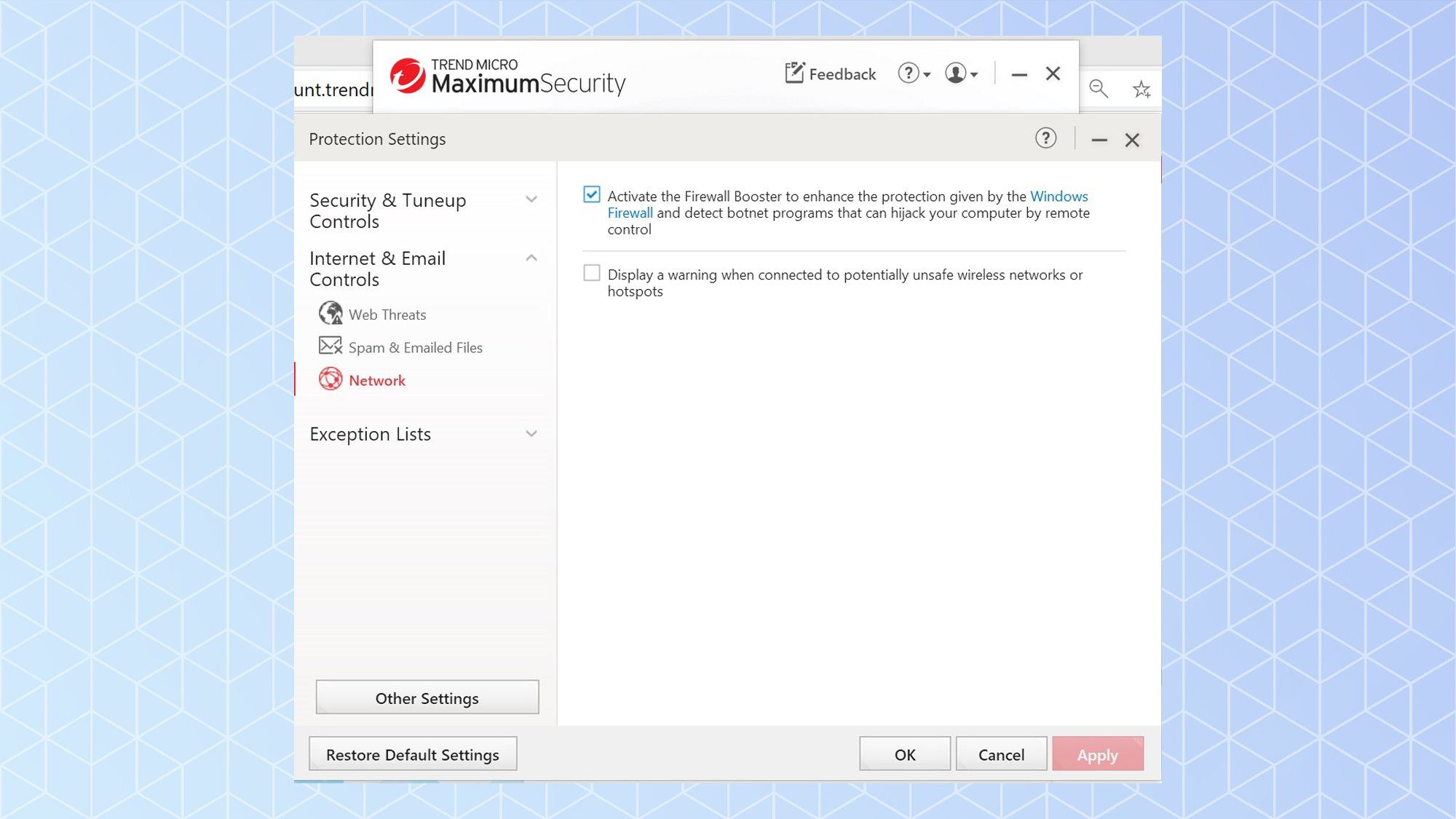
While just about all of Trend Micro’s competitors include a firewall in their top suite to replace Microsoft Defender Firewall, Trend Micro stops short. It does have what the company calls a Firewall Booster that monitors web traffic for evidence of intrusion and botnets.
All four Trend Micro security suites include the company’s Pay Guard hardened browser, something that many other antivirus brands reserve for their top programs. The Pay Guard browser doesn’t allow browser extensions, requires encrypted connections and recognizes financial sites. However, it lacks an onscreen keyboard to thwart keylogger malware.
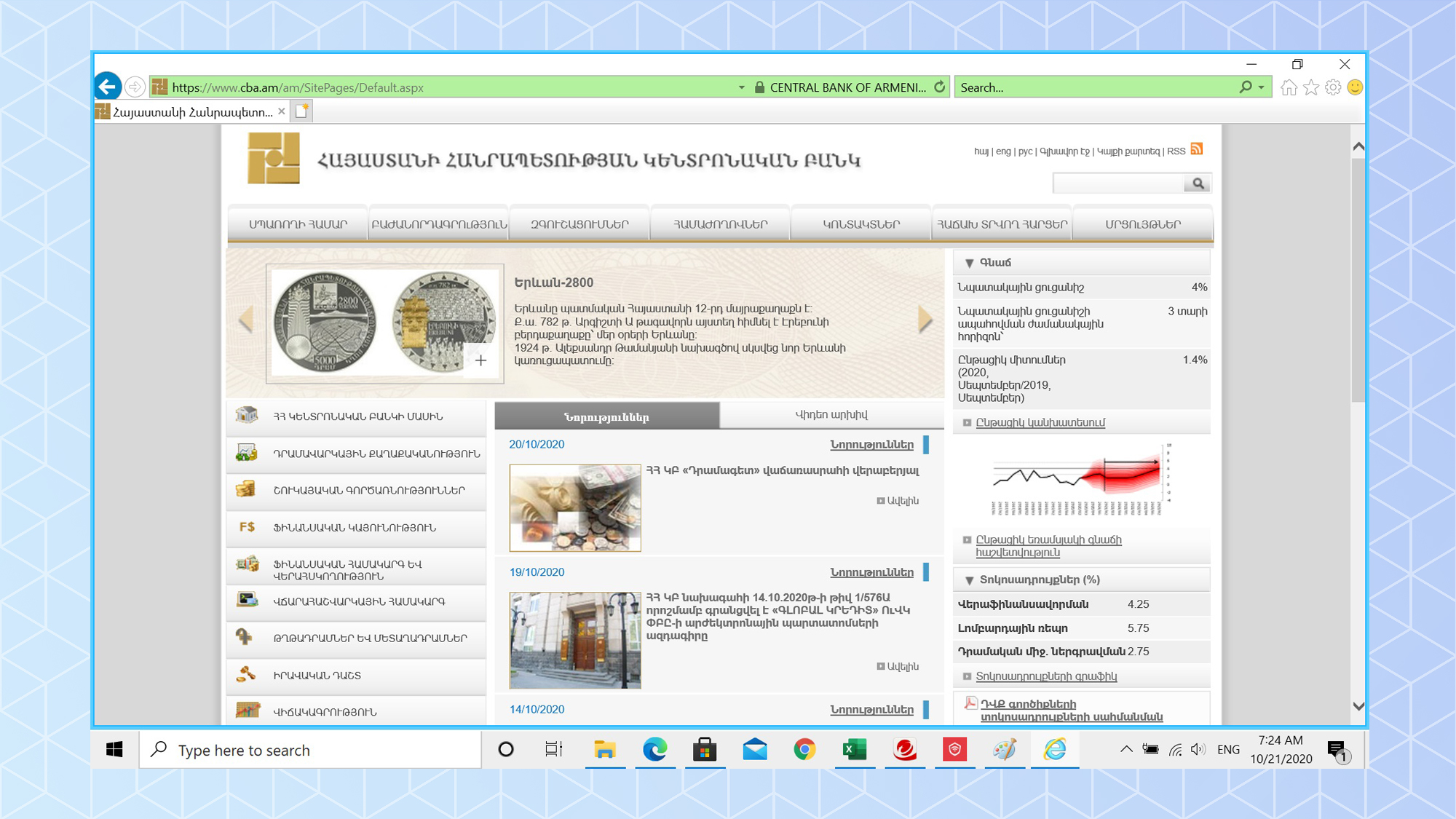
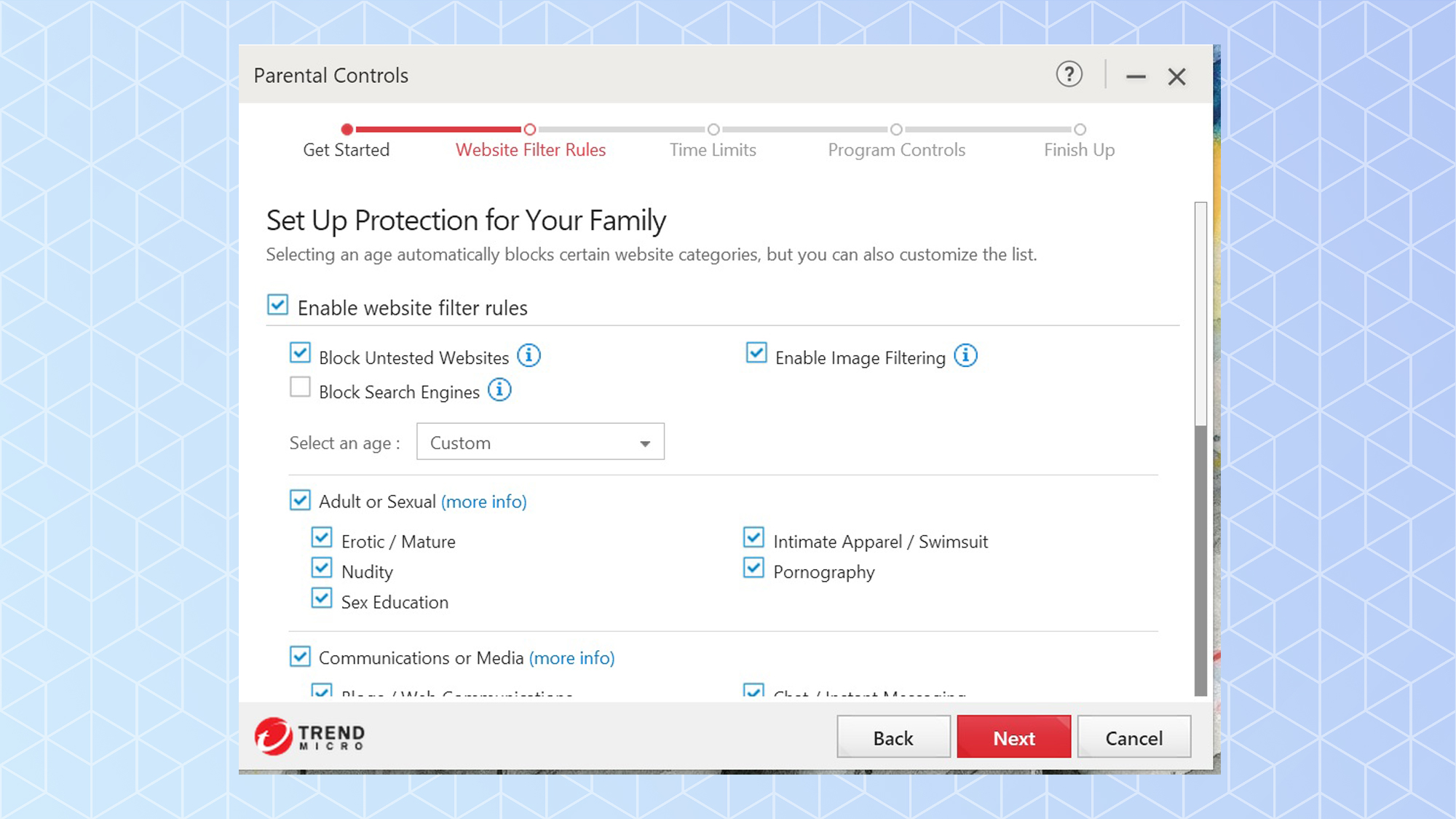
Maximum and Premium Security include potent Parental Controls to keep impressionable eyes away from online dangers. It allows scheduling of computer use, filters out objectionable subject matter and lock-out preselected apps.
Personal security is front and center with the ID Security mobile app that comes with Premium Security. It scans the dark web for your personal information and can be like an early warning system by detecting fragments of your data before an attack takes place.
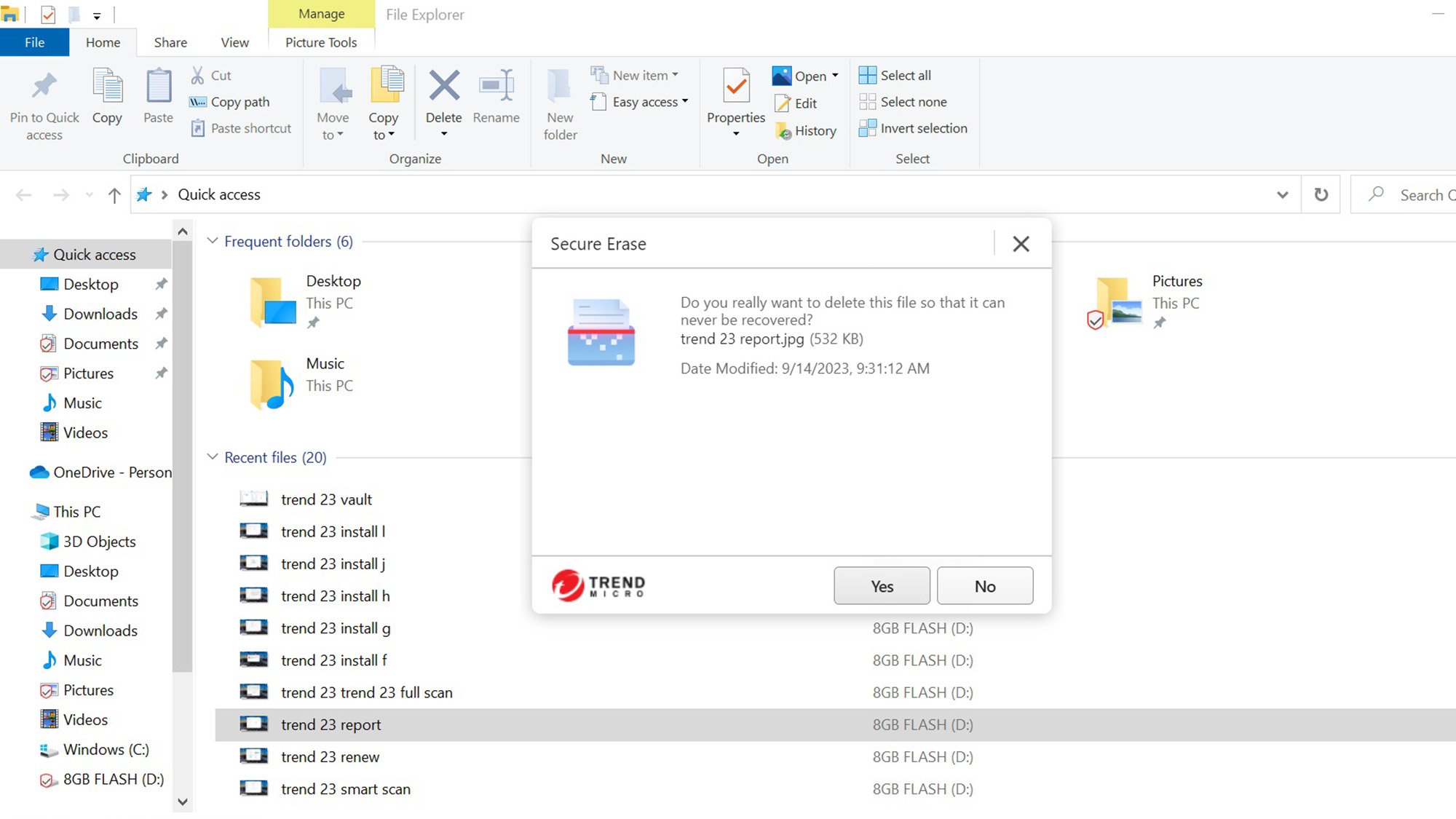
Meanwhile, Trend Micro Premium includes the Vault, a 128-AES file encryption program to hide things in plain sight. There’s also Secure Erase to wipe any file from the drive and is available with a right click on the Windows File Explorer file or folder entry. The program offers Quick Erase (single pass overwrite) or Permanent Erase (which makes seven randomizing passes to fully obliterate it).
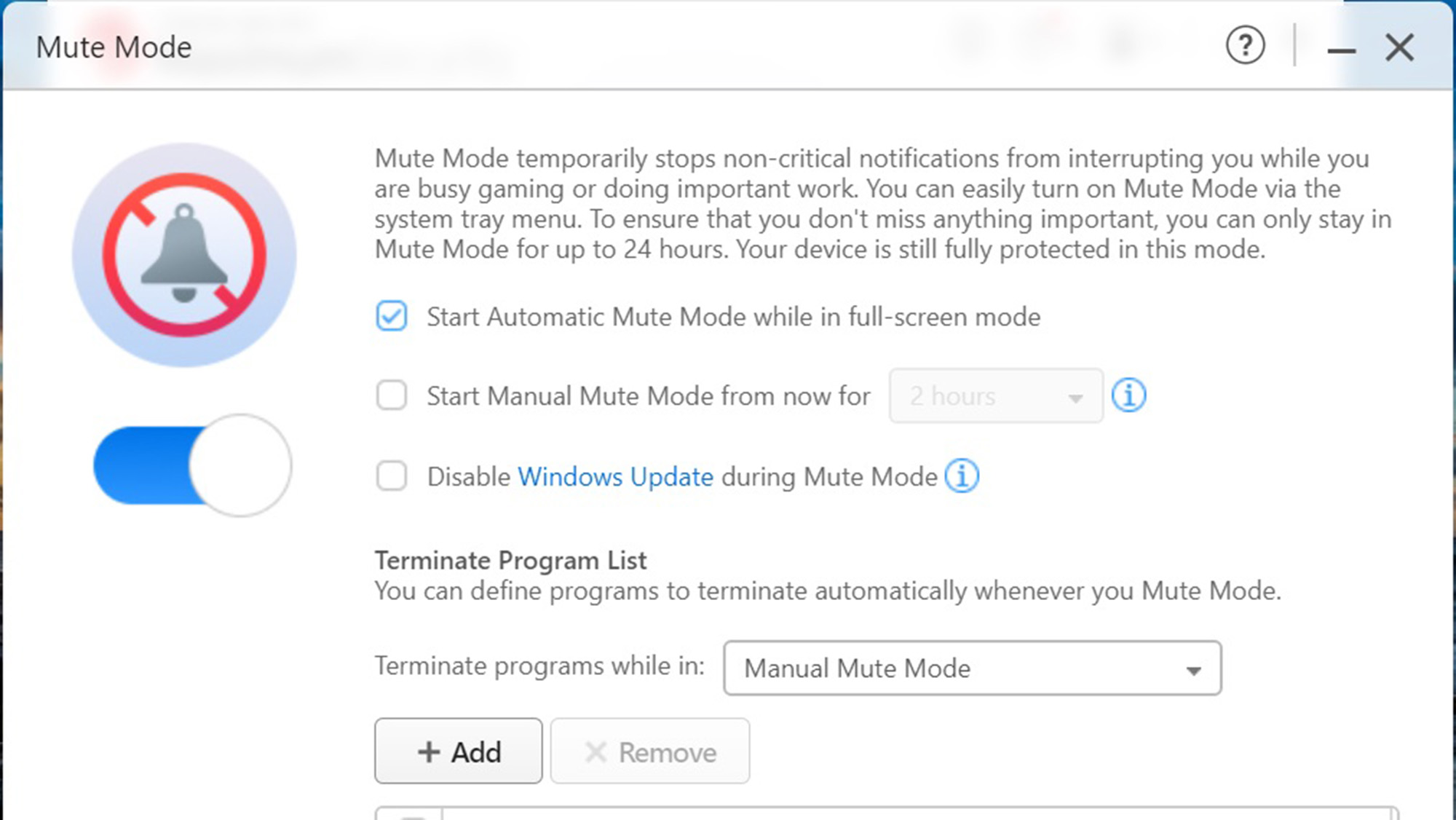
All Trend Micro security plans include a gamer-friendly Mute mode to reduce interruptions by delaying updates, notifications and noncritical scans. It can be set to start when any app runs full screen, Trend Micro has registered more than 50 programs and lets you add your favorites. On the downside, the Trend Micro programs fall short by not defending a Windows computer’s webcam; the Mac program has this protection.
Trend Micro review: Performance and system impact
Trend Micro’s scanner may be fast, but it eats up system resources. To test the software’s system impact, we used our custom benchmark test, which measures how long it takes to match 20,000 names and addresses on an Excel spreadsheet. Our Lenovo ThinkPad T470 test bed had a 2.5GHz Core i5-7200U processor, 8GB of RAM and 256GB of solid-state storage with 50.7GB of files.
Prior to installation of Trend Micro Maximum Security, the ThinkPad took an average of 9.8 seconds to complete the Excel benchmark test. That rose to 10.0 seconds after Trend Micro was installed, an undetectable 2% loss in performance potential. This makes it one of the most efficient security apps when it’s monitoring but not scanning the system.
As it ran a Full Scan of the entire system for malware, the ThinkPad computer took a big hit, however, with the benchmark score falling to 13.0 seconds, a 33% decline in performance possibilities. That’s not quite as bad as Sophos Home Premium’s nearly 40% decline in performance potential but they both impose too much of a performance penalty. On the same test, ESET Smart Security Premium’s benchmark scoring indicated an acceptable 6% fall in performance.
When it came to Quick Scans, the software was even more resource hungry. Its benchmark scores averaged 14.0 seconds, a 43% decline compared to the baseline. Only McAfee’s 70% decline on quick scans was worse.
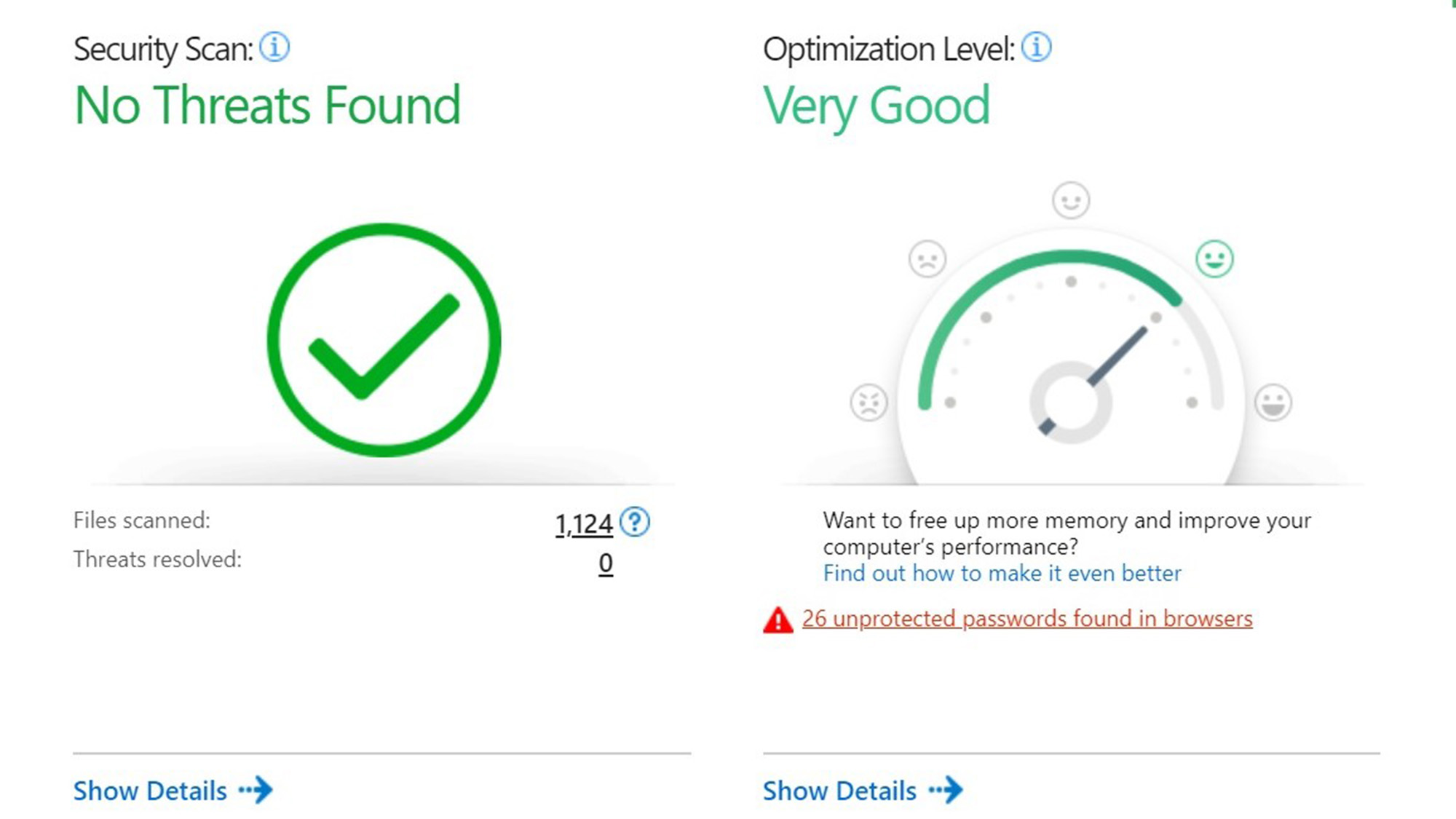
The payoff is very fast scanning that is world class with an initial scan taking all of 10 minutes and 4 seconds; only Sophos Home Premium was faster at 7:16. Along the way, the Trend Micro scanner looked at 441,511 files. By the third pass, it was down to 1:59 and just 4,342 key infectable items. This makes it among the quickest to sift through a large pile of files while focusing on those that are the most appealing to hackers.
In fact, it’s on a par with the quickest scans of other security suites, like Bitdefender Total Security. Trend Micro Maximum Security was just as fast during Quick Scans, which ran 59 seconds to examine 1,124 files, making it one of the fastest malware detection systems around.
Trend Micro review: Interface
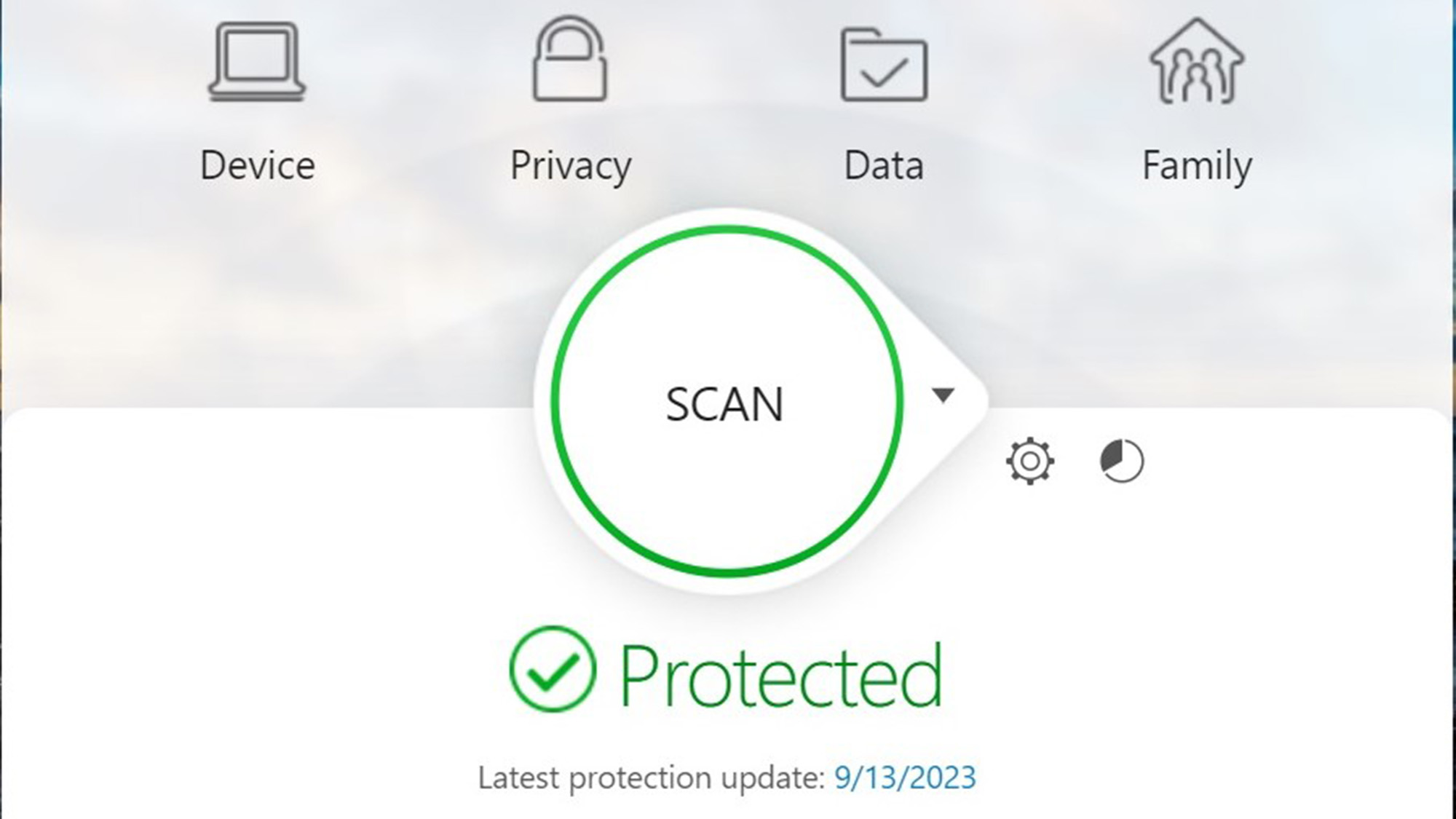
Trend Micro’s interface is functional, well-designed and takes up about one-third of an HD display but can’t run full screen. The in-your-face Scan button is complemented by the program’s green checkmark to show no current threats.
The prominent Scan button starts a Quick Scan while the downward arrowhead leads to the choice of running quick, full or custom scans. The top of the main screen has lots of customization potential with links for Device (security settings), Privacy (Pay Guard and Data Theft Prevention), Data (File shredding, encryption and password manager) and Family (parental controls) categories. The subsidiary pages are simple, well-organized and lead to detailed configuration choices.
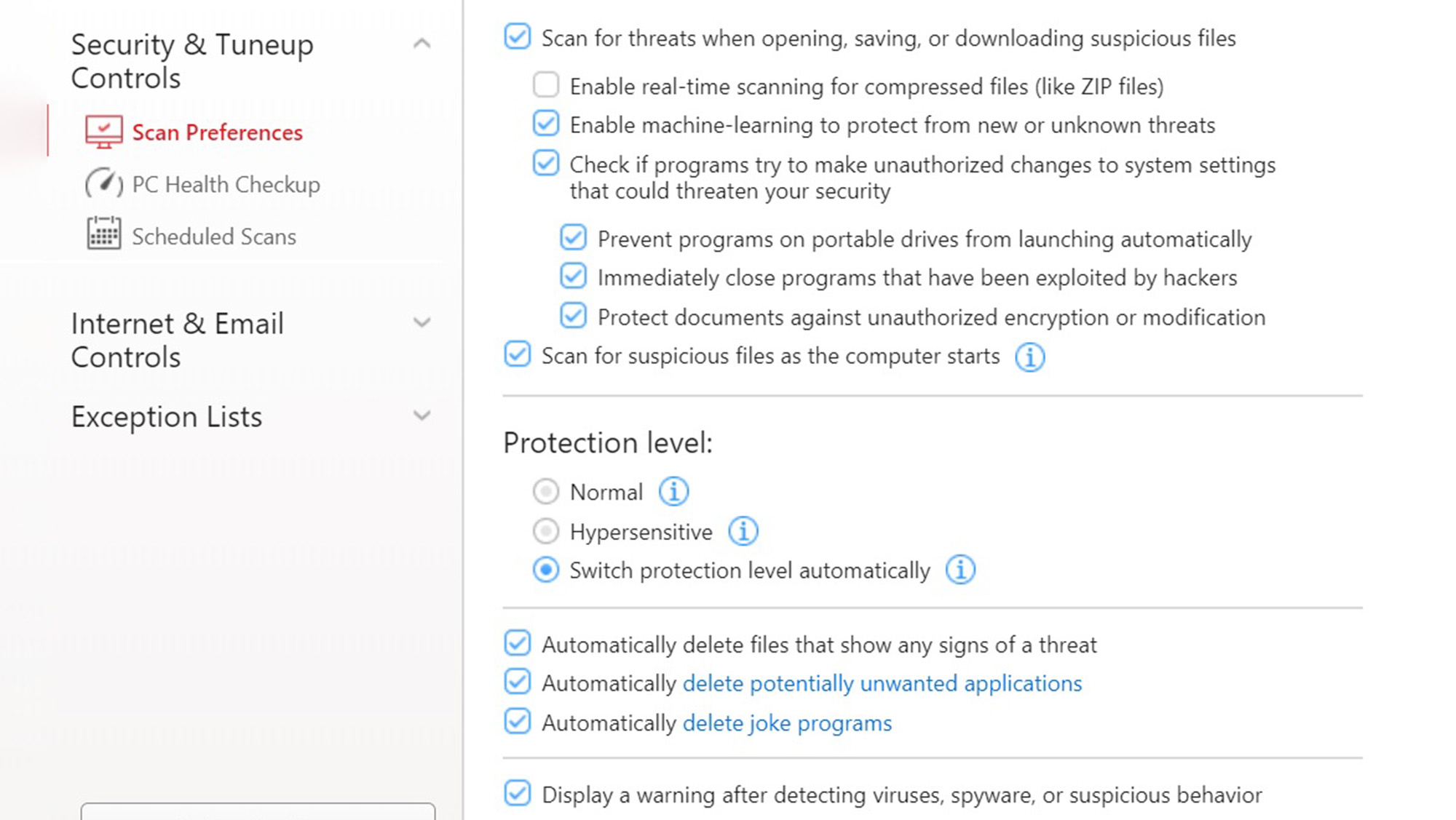
Unlike many of its peers, there’s a way to adjust the program’s overall response, with the Protection level choice between Normal and Hypersensitive. My favorite is the compromise between them where Maximum Security chooses the level that best suits current conditions and threats.
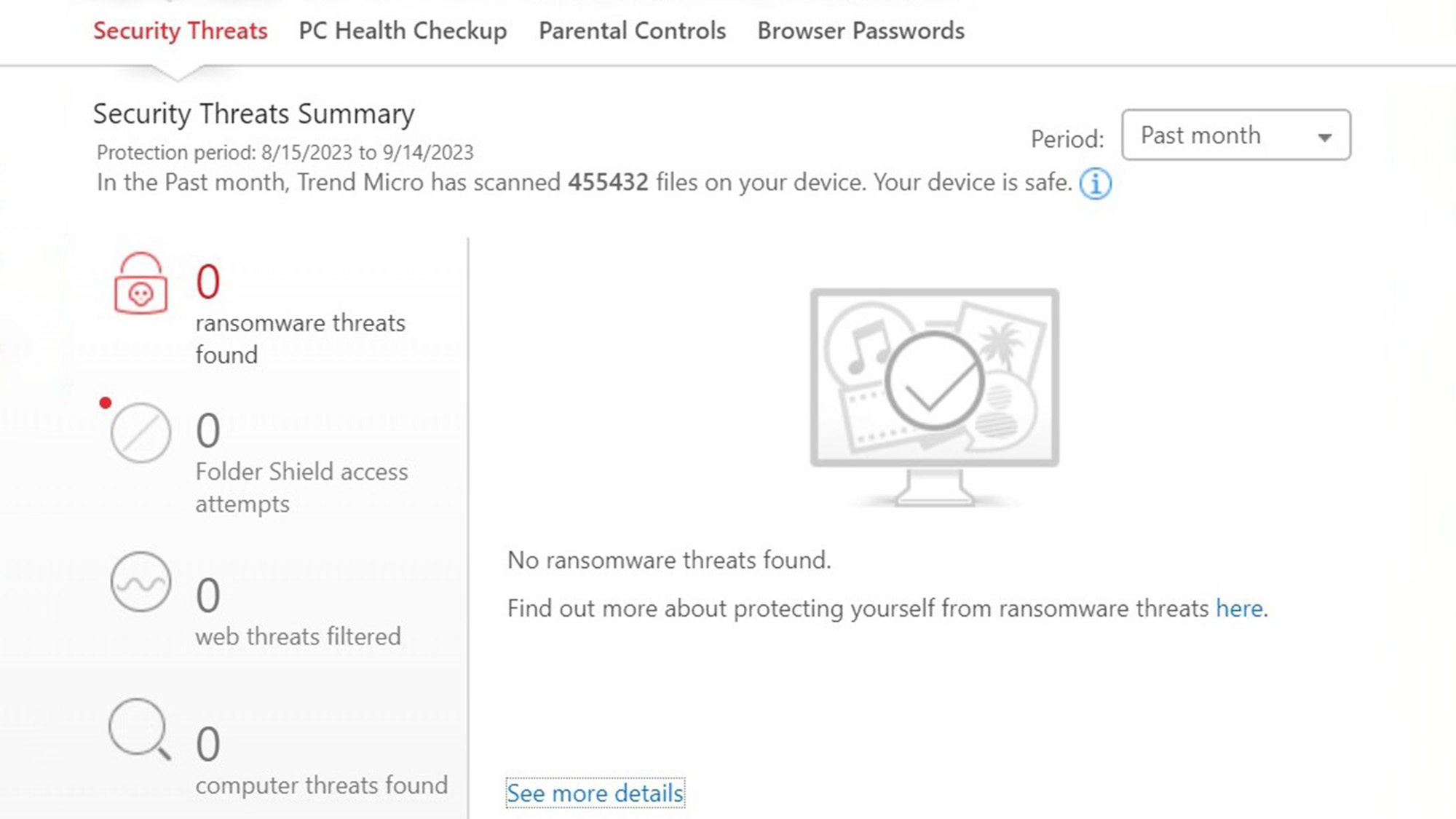
There’s one more thing Trend Micro designers put up front: a periodic Security Report. It’s the pie chart to the right of the settings logo. It is incredibly deep with aspects for overt threats as well as access to the optimizer app, parental controls and password manager.
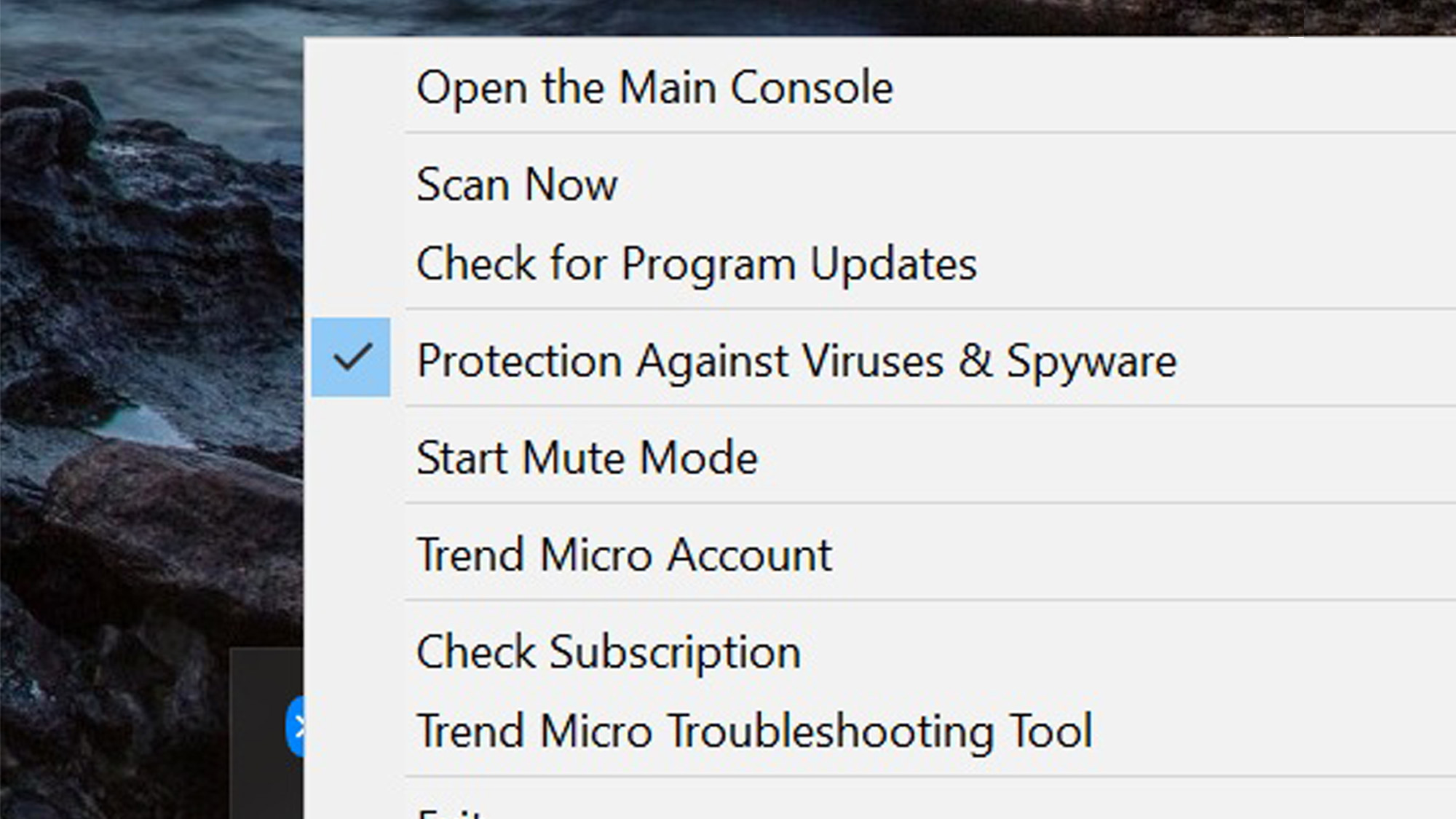
The tasktray icon is one of the most powerful ones in the security world. It not only has links for the main screen and the ability to check for updates, but it can start a scan or run the support department’s troubleshooting tool.
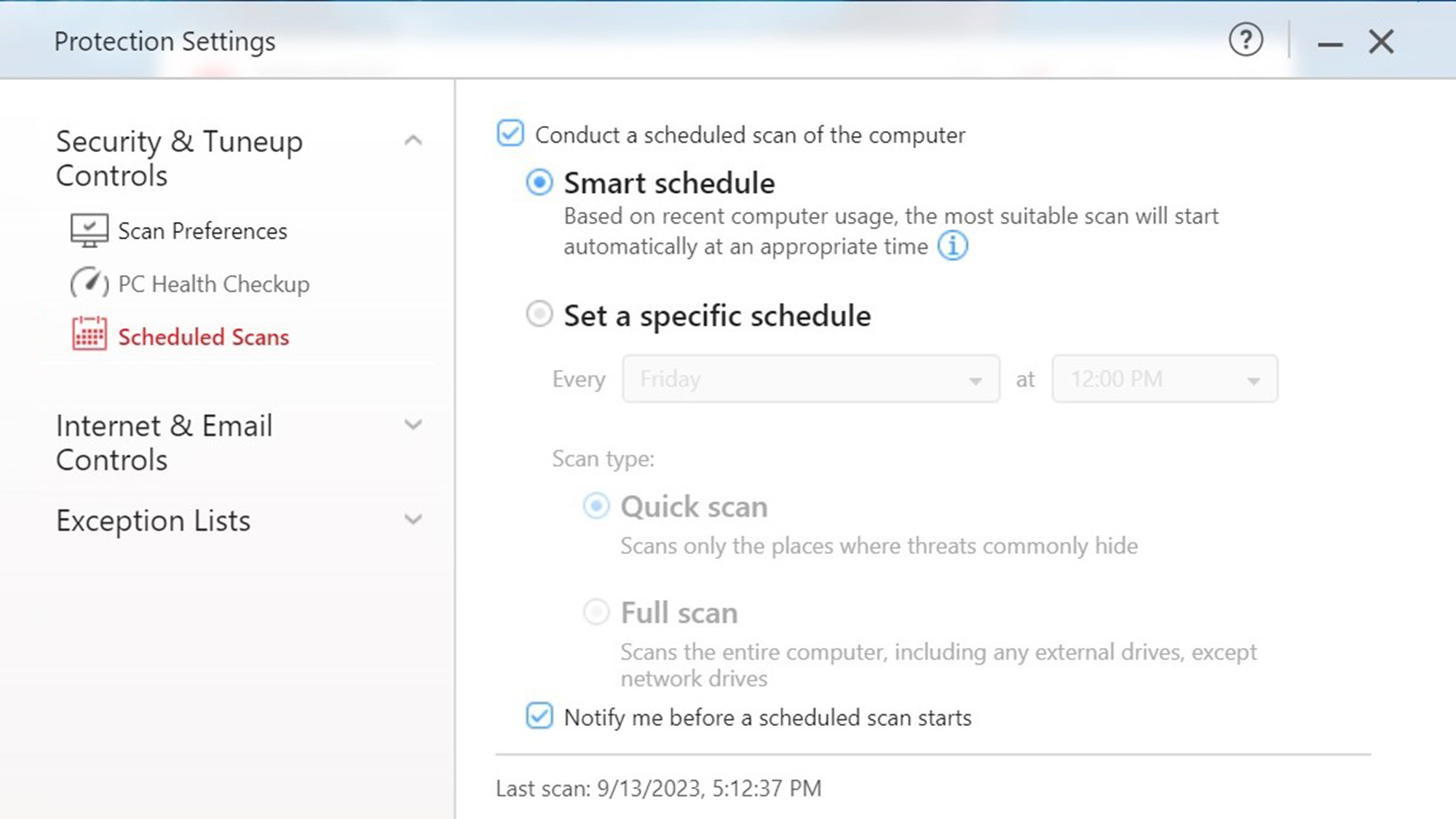
Automating system scans is easy: pick a time, how often and whether it should be a quick or full scan. I really like the Smart Schedule option that fires up the scanner to hunt for malware when the system is idle.
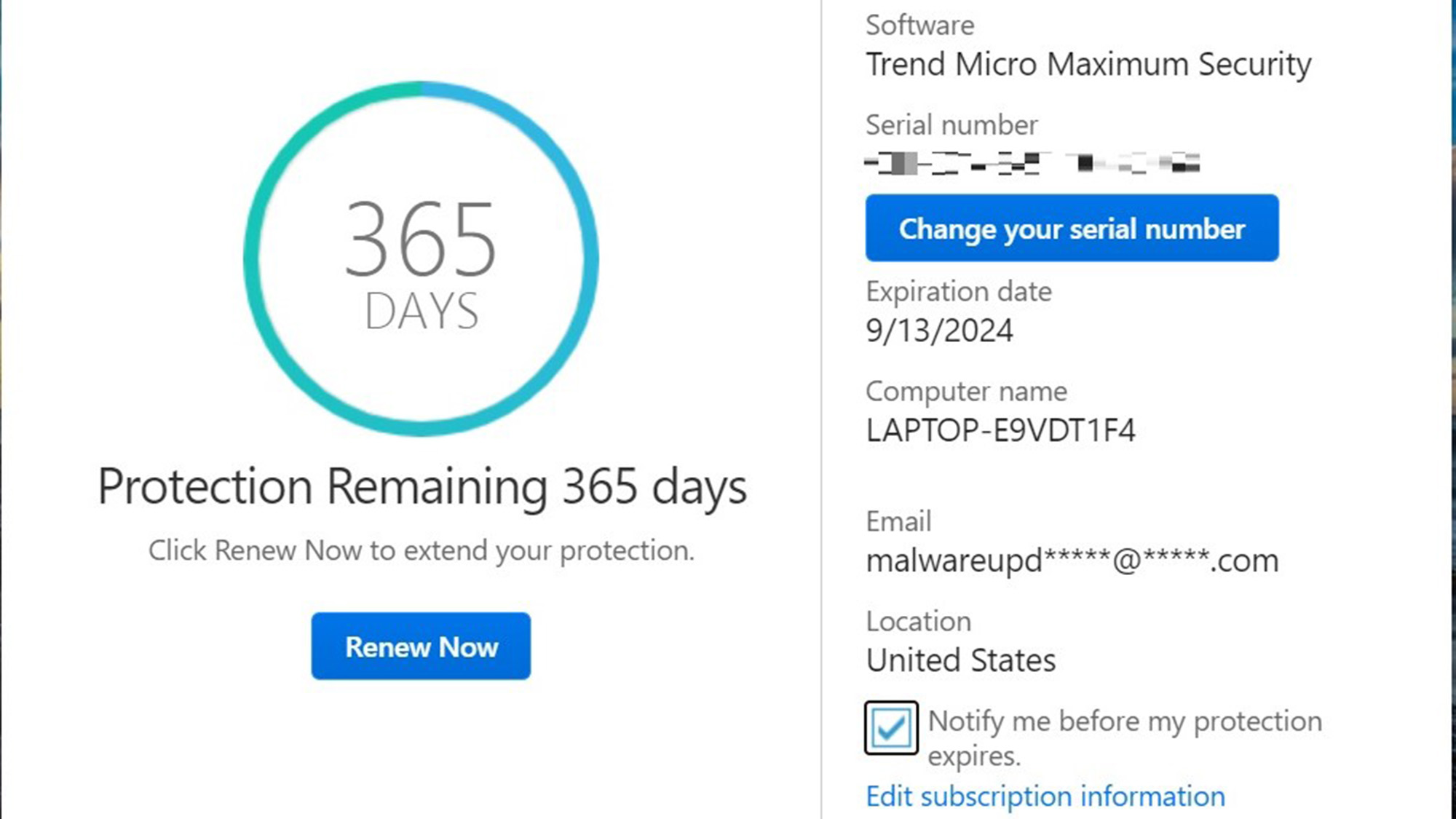
For those who put off the inevitable, the program has the subscription’s expiration date at the bottom of the main screen. Click on it to bring up a detailed report and ability to renew.
Trend Micro review: Installation and support
Getting Maximum security loaded onto the tests system started at Trend Micro’s website. I picked the product, paid and declined the extra $40 for the Premium Service Plan, which includes virus and spyware removal and computer health checks.
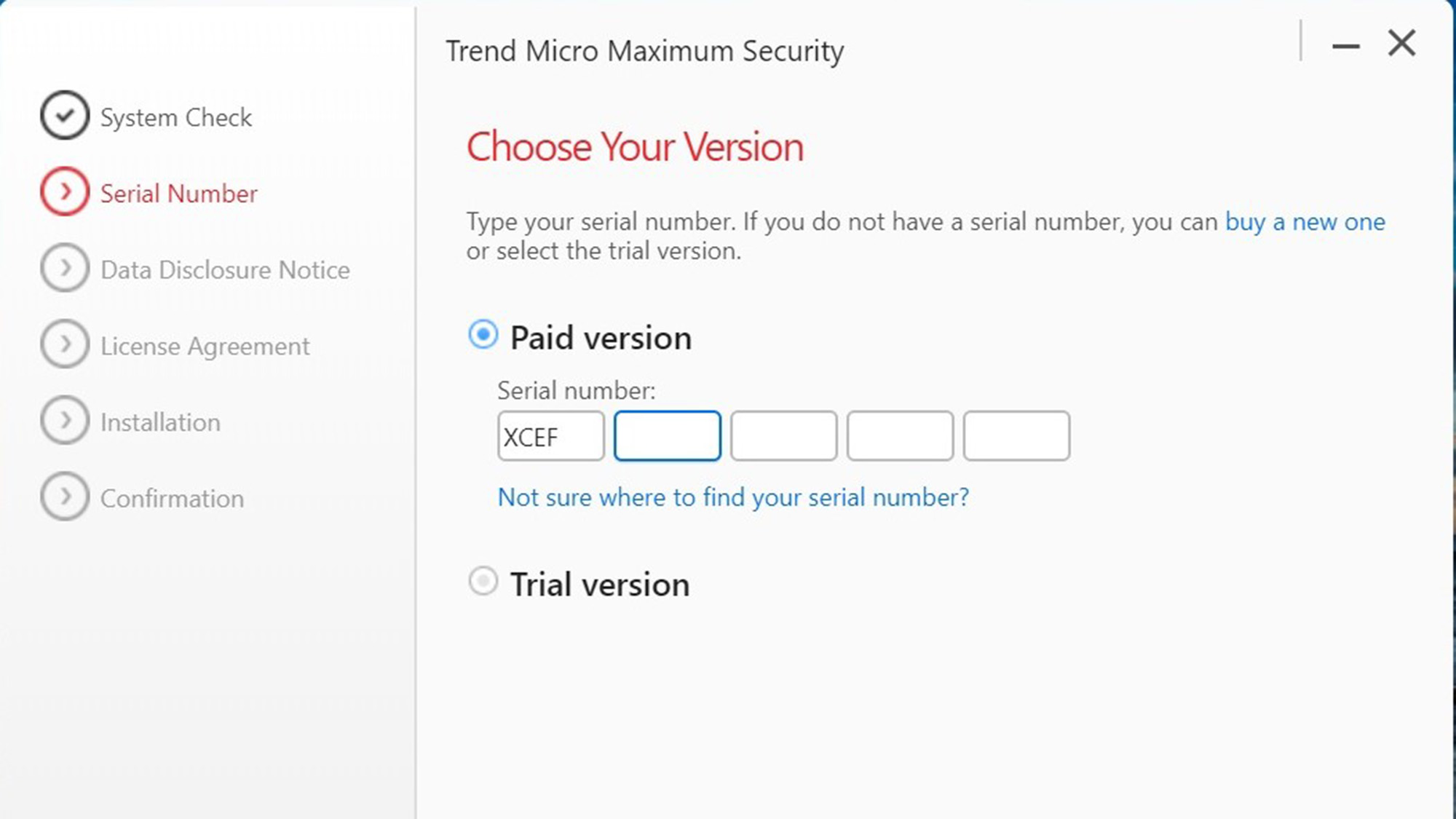
I registered and placed the order. Then, a serial number showed up, which I wrote down. Then, the program’s 433MB file downloaded and was automatically unpacked. The program checked for existing malware on my test system.
Next, I added the aforementioned serial number to the page and then checked to approve the license. There’s no way to avoid having Trend Micro copy items of security interest from your system during installation.
Finally, the real installation started, although the page for approving monthly security reports locked up and a ghost of it showed after this. I finished the process by adding an email, password and saw that everything was activated.
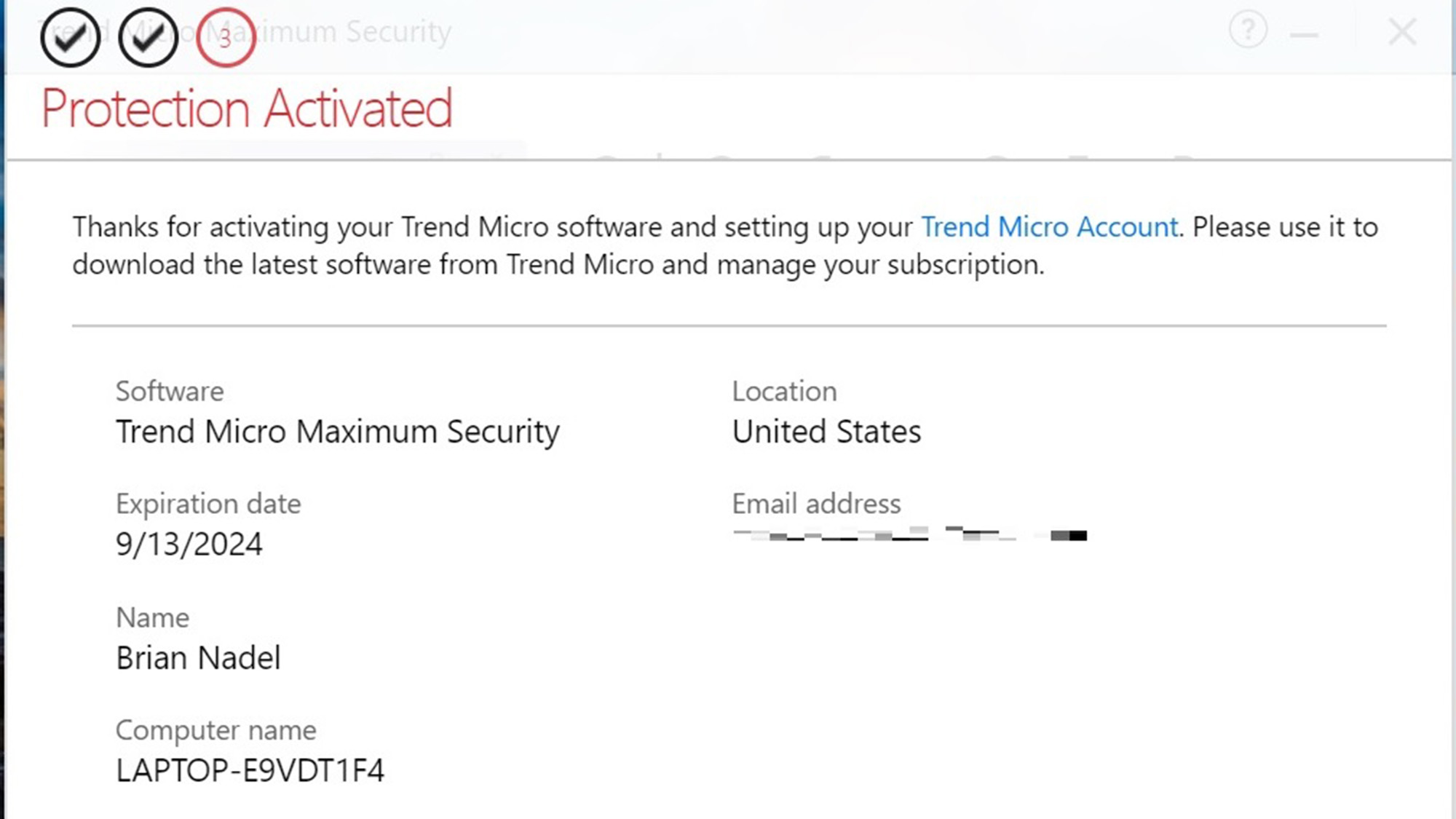
It took 12 minutes and 15 seconds, making it one of the slowest installation processes around. To its credit, Trend Micro sent me an email summarizing the transaction.
It wasn’t over yet because Trend Micro asked several questions about my computer use. This led to four suggestions of features to turn on or download followed by a quick scan with suggestions to tighten the system up.
There are Trend Micro operators waiting to talk to you Monday through Friday from 9am to 5pm (Pacific time), but if you sign up for the Premium Service Plan, you get 24/7 support. They also respond to online chat and emails.
Trend Micro review: Verdict
Trend Micro has a good variety of security products from basic to full-featured. It provides adequate if unflashy antivirus protection for Windows at a good price and will appeal to those who don’t think they need a better firewall than the one Microsoft provides. It comes with lots of extras, but its scanning engine is too resource-heavy and even the top suite had too many irritating false positive identifications of safe software as dangerous. The only saving grace is that the scans are happily very short.
While it provides most of what’s needed to keep a family’s computers clean, there’s no unlimited plan and its effectiveness a finding and killing viruses is a step below that of Kaspersky and Bitdefender. That said, it can provide a lot of peace of mind for the money.
Brian Nadel is a freelance writer and editor who specializes in technology reporting and reviewing. He works out of the suburban New York City area and has covered topics from nuclear power plants and Wi-Fi routers to cars and tablets. The former editor-in-chief of Mobile Computing and Communications, Nadel is the recipient of the TransPacific Writing Award.