Can You Trust Apple with Your Data?
After the celebrity-nude tsunami, can you trust Apple's security? No -- and you shouldn't trust anyone else's either.

Following the very public leaks of private intimate photos of celebrities, many of whom are also iPhone owners, some security experts say Apple may have made it too easy for thrill-seekers to guess celebrities' usernames and then "restore" backed-up photos to their own iPhones. That's just one reason many people are worried.
Various reports claim that Apple's next iPhone can be used as a credit card, and that the company is making a fitness band that will collect data about the wearer's health. In the wake of the celebrity nude-photo leaks, can anyone trust Apple with their private photos or health or financial data?
The answer is no, but don't blame Apple alone. You shouldn't trust any company — Apple, Facebook, Google and Microsoft included — with your private data. Instead, you should take control of it yourself, because that's the only way to be sure it doesn't fall into unauthorized hands.
MORE: Apple to Improve Security Following Celeb Selfie Thefts
The iCloud 'hack,' and how it might have happened
Most of the nude celebrity photos exposed on Sunday were "selfies" taken by the subjects themselves using smartphone cameras, and many of those smartphones were Apple iPhones. The starlets — all the affected celebrities were young women — may not all have realized that their iPhones automatically backed up every photo to Apple's iCloud service, or that all those photos could be copied to another device.
"You have all sorts of important stuff on your iPhone, iPad and iPod touch, like your photos and videos," Apple explains on its own site. "iCloud automatically backs it up daily over Wi-Fi ... You don't have to do a thing."
"When you set up a new iOS device," the site adds, "iCloud Backup does the heavy lifting. Connect your device to Wi-Fi and enter your Apple ID and password. Your personal data — along with your purchased music, movies, TV shows, apps, and books — will appear on your device, automatically."
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
That makes it pretty easy to get someone else's iPhone backups. All you need is their email address.
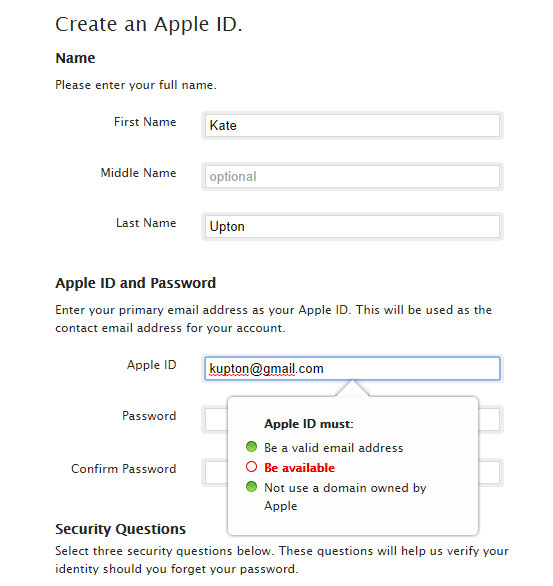
Say you're targeting model and actress Kate Upton, but you don't know her email address. In that case, go to the My Apple ID website to try to set up an Apple account in her name.
Enter some email addresses that she might actually use, such as "kupton@yahoo.com" or "kate.upton@gmail.com." Apple will tell you which ones are already registered. One of those may be hers, so make a list.
You may be wondering: What about Kate's Apple password? That's easy to get around.
You could bombard the Apple ID website with commonly used passwords, such as "Zaq1xsw2," which meets Apple's password standards and looks complicated, but is really just two columns of adjoining keys on a keyboard. There's no penalty for multiple wrong guesses.
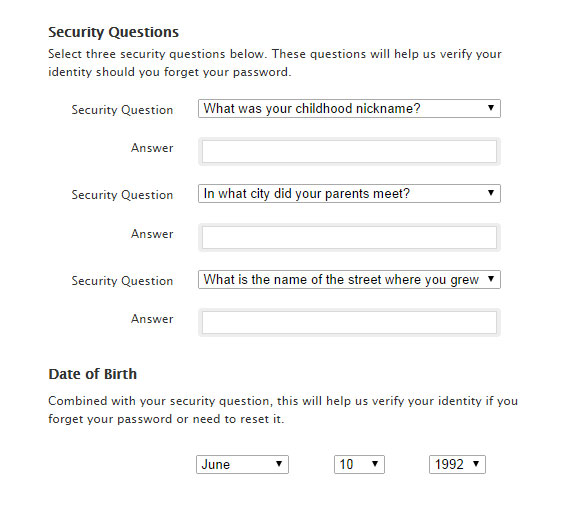
Or, you could go to iforgot.apple.com, enter one of Kate's possible Apple IDs and select "Answer security questions." You'll first have to enter her birthdate, which for many celebrities is a matter of public record. If you enter Kate's real birthdate and get to the next page, you'll know you've found her Apple ID. If not, keep trying.
Next come two security questions. To Apple's credit, none are as dumb as "What was your mother's maiden name?", but given the amount of publicly available biographical data on celebrities, most of the security questions can be answered with a few good guesses. After three bad guesses, you have to start over again, but there's no waiting period to do so.
If you get past the security questions, then — boom — you'll have a chance to change Kate Upton's password to one of your choosing. Since you already know her Apple ID, you can now set up a new iPhone or iPad as her, and cackle with glee as all her photos automatically download to it.
What about two-factor authentication, which prompts the user to enter a PIN texted to a designated cellphone? Apple only sends a recovery PIN if you give up on the security questions — and, as we've seen, you can keep guessing at those till you get them right.
Don't have a spare iDevice? Then you can create a virtual iPhone on your Windows computer, using forensic software such as Elcomsoft Phone Password Breaker, and load the data onto that. Kate will be none the wiser, since Apple will not tell her another device has been set up with her account.
Once you have Kate's information downloaded, you'll have her address book too — which will be full of other celebrities' email addresses with which you can repeat the process.
In an interview with The Wall Street Journal posted last night (Sept. 4), Apple CEO Tim Cook said the company would soon notify account holders when someone tries to change their passwords or add a new device to their accounts. He also said two-factor authentication, if enabled, would be required to log into iCloud accounts from new devices, as Android already requires (see below).
It's not just Apple
It would be unfair to blame Apple entirely for the celebrity-nude leaks. Security experts who analyzed the photos' metadata found some had been taken with Android or Windows Phone devices, feature phones or stand-alone digital cameras.
Rumors abound that there's a huge underground trade in nude selfies of celebrities and non-celebrities alike. Some of these photos may come from former boyfriends; others may have been stolen directly from personal computers.
Google's Android does make it a bit harder than iCloud to steal someone else's data, but only if two-factor authentication has been enabled. In that case, a PIN will be sent to the designated phone number, which will tip off the legitimate user that someone's trying to break into his or her account.
(If you've really lost your only phone, you can have Google send the PIN to a pre-designated "backup" phone such as a friend's, or you can ask for Google's help, which "may take three to five business days.")
Without two-step verification enabled, the Android process is much the same as Apple's. The attacker can keep guessing the password, and once he or she does, all the backed-up photos from Google+ are loaded onto the new device, while the legitimate user receives no notification.
MORE: 'Don't Take Nude Selfies' Is Not Good Security Advice
Other online services are about as safe as Google's. For example, Dropbox offers to back up all user photos as well, and without two-step authentication, all you need to get in is an email address and password. Chances are that Kate, or some of her celebrity friends, will use the same credentials for Dropbox — or Facebook, or Yahoo — as they do for Apple or Google.
What the cloud really is, and how to avoid it
The real weak point in this system is not Apple, or the starlets taking nude selfies, but the cloud itself. As British security expert Graham Cluley has said, "the cloud" is just shorthand for "someone else's computer."
When you take photos with your smartphone, they're being copied to someone else's computer, and you lose control of them, just as you would if you emailed them to someone else. You're placing trust in another person, or another company, to guard your private data.
The key to keeping that data safe is to maintain full control of the data. If you're going to take nude selfies, don't use a smartphone — instead, use a stand-alone camera that's not connected to the Internet. (Better yet, use a Polaroid.)
The same goes for other kinds of sensitive information. Tax returns, financial records and anything else you don't want anyone else to see should not be backed up to online-storage or sharing services. Instead, encrypt it and then back it up to two external drives — one of which you keep at home and one you keep somewhere safe, such as in a locked office desk or bank safe-deposit box.
As for the iPhone 6's rumored digital-wallet abilities, and the rumored Apple fitness band, don't trust them. There's a reason that Google Wallet and the rival Isis/Softcard system backed by AT&T, Verizon and T-Mobile have never caught on; people don't trust phones to safeguard their data.
Fitness bands send all sorts of health information to the cloud, which may be one reason sales have leveled off. (To its credit, Apple has told developers of apps for its fitness band that they can't resell user data.)
What about encrypting private data before it's uploaded to the cloud? You could do that, but the information will still be out of your control, and you won't know if someone tries to decrypt it.
So take all the nude selfies you want, celebrities of the world — and celebrity wannabes. Just know that you can't count on anyone but yourself to keep those private photos private.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
kep55 In a word, NO! The internet or "cloud" is about as secure as a glass window in a hurricane.Reply
 Club Benefits
Club Benefits





