Apple Lashes Out Against Google Over iPhone Hack Report — And They’re Wrong
No apologies, no explanation, just complaining about Google

Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
More than a week after Google researchers said potentially thousands of iPhones were infected by corrupted websites, Apple has responded with "the facts," but its statement was more of a lash-out at Google than an actual explanation.
"The sophisticated attack was narrowly focused, not a broad-based exploit of iPhones 'en masse' as described" in the Google Project Zero blog post, said the Apple statement, posted today (Sept. 6). "The attack affected fewer than a dozen websites."
Yet Apple's statement is full of holes, and it ignores what the Google researchers may have truly revealed -- that the much-admired security of iOS may be more myth than reality.
MORE: Mass iPhone Hack Is Huge Wake-Up Call for Apple
The Google report "creat[ed] the false impression of 'mass exploitation'" and "stok[ed] fear among all iPhone users that their devices had been compromised," Apple said. "All evidence indicates that these website attacks were only operational for a brief period, roughly two months, not 'two years' as Google implies."
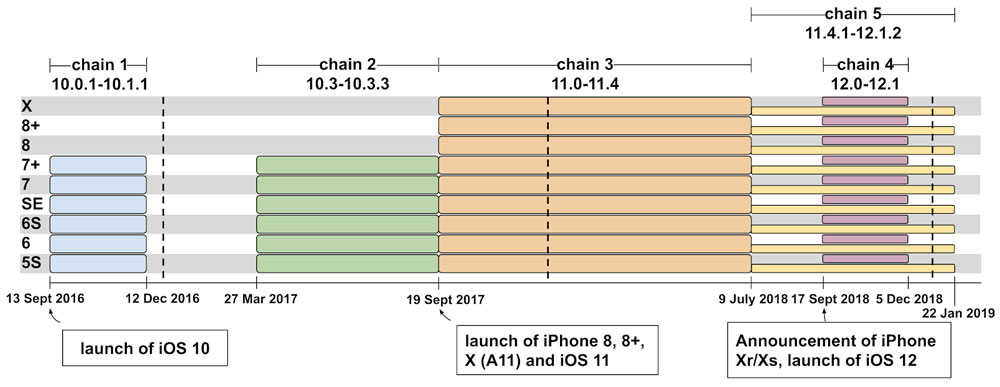
That's not exactly true. The exploits, 14 in all, were part of five different attack campaigns, each corresponding to different versions of iOS, that began in late 2016.
One of the most recent attack campaigns, against iOS 12.0 and 12.1, lasted less than three months in the fall of 2018, but two others lasted six months, and another nine months.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
These were classic "watering hole" attacks, predicated on the notion that certain types of people will be regular visitors to certain websites.
In this case, Apple said, the malware was placed on sites "that focus on content related to the Uighur community" of western China, seemingly confirming rumors and speculation that arose as soon as Google released its report.
Well, that's just your opinion, man
But that's still a mass attack, not a targeted one. Any iPhone, whether used by a Uighur or not, that navigated to the corrupted websites could have been successfully infected. Anyone who discovered the malware implant in those sites' code could have copied it and used it elsewhere.
"We fixed the vulnerabilities in question in February -- working extremely quickly to resolve the issue just 10 days after we learned about it," the Apple statement says. "When Google approached us, we were already in the process of fixing the exploited bugs."
Apple does deserve kudos for issuing a patch for the most urgent of the flaws, affecting iOS 12.0 and 12.1, fairly quickly. But of course, it had already patched most of the earlier bugs exploited over the previous two years with earlier iOS updates. The attackers just kept finding new bugs.
That's the real issue here. The attackers -- for argument's sake, let's just assume they're Chinese state intelligence -- had a seemingly endless supply of iOS vulnerabilities. Every time Apple whacked a mole, another one popped up.
Not all the flaws were unknown to Apple. Some continued to be used by the attackers in this case even after they'd been disclosed and even patched. None of the malware was "persistent" enough to keep working after an iPhone had been rebooted.
But there were enough previously unknown vulnerabilities that could be exploited to infect a iPhone that simply clicked on a link — one-click zero-day exploits, in infosec jargon — that iOS security suddenly looks a lot less solid.
If these iOS zero-day exploits were so plentiful, and apparently so cheap to obtain that the attackers would deploy them for months on public websites, then how secure is iOS really?
Cheaper by the dozen
It's no coincidence that on Tuesday (Sept. 3), Zerodium, a leading reseller of zero-day exploits, announced that it would pay up to $1.5 million for a top Android exploit, but only $1 million for a corresponding iPhone one. (The exploits used in the attacks Google chronicled would have been worth $500,000.)
"The zero-day market is so flooded by iOS exploits that we've recently started refusing some [of] them," Zerodium CEO Chaouki Bekrar told Bleeping Computer. "On the other hand, Android security is improving with every new release of the OS thanks to the security teams of Google and Samsung."
It was hard not to see Zerodium's announcement as a PR stunt. Former Facebook head of security Alex Stamos quipped that Zerodium was "exploiting a vulnerability in the security media to insert themselves into the news cycle."
But that contrarian view gained more credence when The Grugq, a pseudonymous South African zero-day broker, declared on Twitter that "Android is a much safer platform than iOS," as long as you handle Android properly.
"The iOS ecosystem is a monoculture, where security is tied to [the] latest hardware and latest software," he added. "If you're behind on either one? Vulnerable to commercial exploit chains. Multiple chains. Android has become incredibly more resilient, and due to diversity much harder to attack."
A third zero-day reseller, Andrea Zapparoli Manzoni, told Vice News that "Android is such a fragmented landscape that a 'universal chain' is almost impossible to find."
He added that some high-profile individuals had switched from iOS to Android, making an exploit that works against many Android devices "immediately more valuable."
Weasel words
To be completely fair, the iOS App Store is still much safer than Google's adware-plagued Play Store.
Apple also deserves a hell of a lot of credit for taking responsibility for keeping iPhones secure, rather than passing the buck along to the end user the way that Android handset makers and wireless carriers have done for years. (Google played that game too until a couple of years ago.)
But it's really dismaying to see Apple, the company that invented the modern smartphone, use security weasel words in today's statement. When it describes the infected websites a "sophisticated attack," it implies that no one could have stopped it.
When it says "we take the safety and security of all users extremely seriously," it sounds like a big-box superstore chain explaining how hackers managed to steal 40 million credit-card numbers.
When it says that "security is a never-ending journey and our customers can be confident we are working for them," it sounds like a company that knows it's been well and truly pwned.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
 Club Benefits
Club Benefits










