How Strangers Can, and Can't, Hack Your Cellphone
A segment on 60 Minutes suggested that it's easy to spy on an iPhone, but the truth is more complicated and less scary.
A segment on CBS News' 60 Minutes news program last night (April 17) may have scared iPhone owners concerned about losing their privacy and security to hackers. But in fact, the show demonstrated only well-known vulnerabilities that affect many cellphones, and no flaws specific to the iPhone.
The segment seemed to show that flaws in the telephone system let hackers easily hear your calls, read your email and turn on your phone's camera. Yet the hacks demonstrated were actually more varied, didn't all depend on telephone service and, in some cases, required the reporters to nearly completely disable security on their mobile devices.

For example, you may have been shocked to see German hacker Karsten Nohl tracking the location of an iPhone used by U.S. Congressman Ted Lieu, D-California, and listening to telephone conversations taking place between Lieu and 60 Minutes correspondent Sharyn Alfonsi.
But you might be less scared if you realized that Nohl could do this only because he and his team had been granted privileged access to the back-end communications system that telephone companies use worldwide.
MORE: Best Android Antivirus Apps
That system is called Signaling System Seven (SS7), and it's a set of protocols that lets telecoms around the world route calls to any landline or cellphone. SS7 makes cellular roaming possible, and also lets calls be forwarded worldwide (a feature that Nohl used to listen in on Lieu's calls).
But, like many services we report on, SS7 does not always have proper security. Each one of the 800-odd companies that make up the global telephone network has to protect its own access to the SS7 system, and not all do a good job.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
So while the average user may not be able to get into the SS7 backend, a hacker who knew his or her stuff might be able to find an entry point. Many state intelligence agencies, such as the NSA, definitely have such access, whether it's through an access hole or by being actively granted access by a cooperative telecom — as Nohl had been.
Old hacks seemingly made new
Nohl and the other hackers featured on the segment are well respected within the information-security community, and everything they said was accurate and level-headed. It was the parts that the 60 Minutes producers chose to leave out that made the piece misleading.
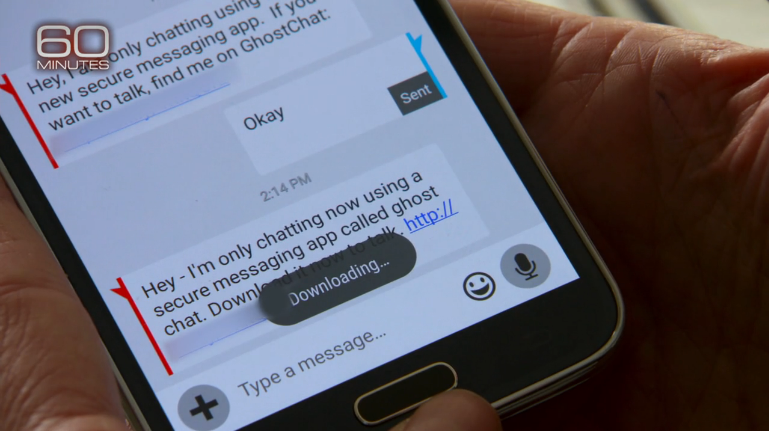
When John Hering, another hacker interviewed in the 60 Minutes piece, fooled Alfonsi into connecting her phone to a rogue Wi-Fi hotspot, then read her email messages, he was actually using a years-old trick. (Hering is one of the founders of the mobile-security provider Lookout Mobile Security.)
Hering gave his rogue hotspot a name that implied it belonged to the Las Vegas hotel in which he and Alfonsi were meeting. That's always been a trap, as many devices are vulnerable to attack from other devices on the same network — even if that network requires a shared login password.
As we reported last week, a twist on this attack takes advantage of the "feature" that many Wi-Fi enabled mobile devices will automatically join hotspot networks that they think they've accessed before. Yet the only form of verification is the Wi-Fi hotspot name, which can be changed in a second.
The fact that Hering could read Alfonsi's email made us wonder what kind of outdated email service she was using for the purposes of this news segment. It doesn't seem like it was an encrypted service, which would have rendered her messages into gibberish on Hering's laptop. Gmail or Yahoo Mail will encrypt email automatically, when they can. The catch is that the receiving email service must support encryption as well.
At one point, Hering showed that he could hijack the user-facing camera on Alfonsi's smartphone to spy on her. But eagle-eyed users may have noticed a clever bait-and-switch by the 60 Minutes crew. In most of the segment, Alfonsi used an iPhone, but for this part she suddenly, and without any notification to the viewer, switched to a Samsung Android phone. That makes all the difference.
Android phones will let anyone install software from anywhere — but only if you manually go into the Settings menu, change a toggle switch to override the system default and allow installation of apps from "unknown sources" outside the Google Play store, and ignore the warning window that pops up. Hering's attack on Alfonsi's Samsung phone probably wouldn't have been possible otherwise, and especially not if the phone was running Android antivirus software of the kind that Hering's own company makes and markets.
Hering's attack also requires social engineering, because he tricked Alfonsi into clicking on a link sent via text message, thereby installing unknown software without thinking twice. This is what can happen when you install random software without verifying its origins. But no matter how gullible a phone's user was, Hering's camera-hijacking attack wouldn't work on Apple devices that haven't been "jailbroken."
Finally, Nohl pointed out that he could track Rep. Lieu even if the congressman turned off GPS on his phone. Alfonsi seemed surprised, but this shocking flaw is exactly how cellphones are supposed to work.
When you move about a city, your phone, whether it has GPS or not, is constantly pinging nearby cell towers and saying, "Here I am." Cellular carriers keep logs of each phone's movements as its signal is handed off from one cell tower to the next. If the phone is roaming out of its home area, then the local carrier and the home carrier will exchange information about those movements for billing purposes — using the SS7 system that Nohl had privileged access to.
What to do if you're truly paranoid
The 60 Minutes segment didn't expose any new points of attack, but it should give users some pause about what they say or do on their devices, at least if they're paranoid enough to suspect a targeted attack by a malicious hacker or nation-state with a bone to pick. An easy way to avoid eavesdropping by hackers or criminals on calls or text messages is to use an end-to-end-encrypted service such as WhatsApp, Signal, Silent Circle or even Apple's own iMessages.
To avoid having your email read, don't connect to any unfamiliar Wi-Fi hotspot, even one in a hotel or airport. Use your phone's 4G connection instead.
Are you on a tablet or laptop that requires Wi-Fi to connect, and don't want to use your phone as a hotspot? Then sign up for a virtual-private-network (VPN) service such as PhantomVPN, HideMyAss or TunnelBear, some of which have free options.
To avoid spyware being installed on your phone, you don't necessarily need to use an iPhone. You can use an Android device as long as you keep "Unknown sources' turned off, and you make sure it's running the latest possible version of Android for that model of device.
To avoid cellular carriers knowing where you are at all times — well, you might as well leave the cellphone at home. The carriers have to know where you are so that you can send and receive calls and texts.
Of course, all these guidelines are useless if you, like Will Smith in Enemy of the State, are targeted by the NSA. In that case, turn the phone off and toss it into a lead-lined box (or an unpowered microwave oven).
"The average person is not going to be exposed to the type of attacks we showed you today," Hering told Alfonsi, using wise words that should toss a bucket of water on any scared users. "Our goal was to show what's possible, so people can really understand if we don't address security issues, what the state of the world will be."

Henry was a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom's Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He's also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
-
jakjawagon A mostly balanced and fair article about smartphone security. Quite unusual these days.Reply
The only thing I would say is, rather than disabling 'unknown sources' on an Android phone, only install apps from sources that you trust (the same advice I've been giving people about Windows PCs for years). The unknown sources switch won't let you install apps from Amazon or other legit non-Google app stores. -
henrytcasey Reply17841943 said:A mostly balanced and fair article about smartphone security. Quite unusual these days.
The only thing I would say is, rather than disabling 'unknown sources' on an Android phone, only install apps from sources that you trust (the same advice I've been giving people about Windows PCs for years). The unknown sources switch won't let you install apps from Amazon or other legit non-Google app stores.
Of course, but our advice is more for the average user, who may not know any better. Experienced users can enable installation of apps from unknown sources, but if the device is victim to an attack, attackers can attempt to whatever programs they want. A better solution would be to enable and disable installation via unknown sources when you need to add or update an app from a credible source.
 Club Benefits
Club Benefits





