Verizon Users Targeted with Nasty Phishing Scam
A sophisticated phishing campaign aims for Verizon Wireless customers, asking them for their passwords in exchange for a "discount."
Look out, Verizon Wireless customers. There's a new phishing campaign trying to take over your accounts.

The crooks behind it have not only crafted phishing websites that look more convincing on a mobile browser than on a desktop one, but they've also registered dozens of URLs meant to mimic Verizon domains, and even have a pretty good knowledge of Verizon's network infrastructure.
"When the phishing link is opened on a desktop, it doesn't look legitimate," wrote Lookout Security researcher Jeremy Richards in a Lookout company blog post. "But when opened on a mobile device, it looks like what you would expect from a Verizon customer support application."
MORE: Best Android Antivirus Apps
The fake Verizon websites vary in what they want you to provide, but both examples Lookout gave asked users to "Complete Your Information For The Discount."
One, hosted at "verizonwireless-plans [dot] com", demanded a full name and phone number, which wouldn't get a crook too far. But the other, "vzwcustomer-discount [dot] com", asked for your "Mobile Number or User ID" and "Password", which would enable full account takeover. (The first URL is offline, but the other is only "Suspended".)
The scam begins with a phishing email, and the attackers have gone to the trouble of closely imitating the legitimate domain used to send email messages to Verizon customers: "ecrm.verizonwireless.com".
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Bogus variations on this include "ecrmverizon [dot] com", "ecrmverizonwireless [dot] com", "ecrmemail-verizonwirelesss [dot] com", "ecrmemail-verizonwirelesss [dot] info" and "ecrmemail-verizonwirelesss [dot] net" (note the triple "sss" in the last three examples).
As for the phishing pages that the emails lead to, more than 70 bogus Verizon website addresses have been registered in the past three months, Richards wrote. You can see a full list on Pastebin.
"This campaign shows that not only did the attackers research what Verizon’s infrastructure looks like, but that they were relentless in their attack," Richards wrote.
So we entered our 'information'
Richards wrote about this campaign in the past tense, but it doesn't seem to be completely over. We checked a few of the bogus websites and found most of them are offline or unused, but at least one — "http://myvzwcustomer-discount [dot] com/" — was active as of noon ET today (April 3), and itcontained dozens of identical Verizon-themed phishing pages.
In one of the live phishing pages, we typed in our phone number as "917-555-1212" and our password as "password", and were redirected to a page that asked us the name of our first roommate and our PIN.
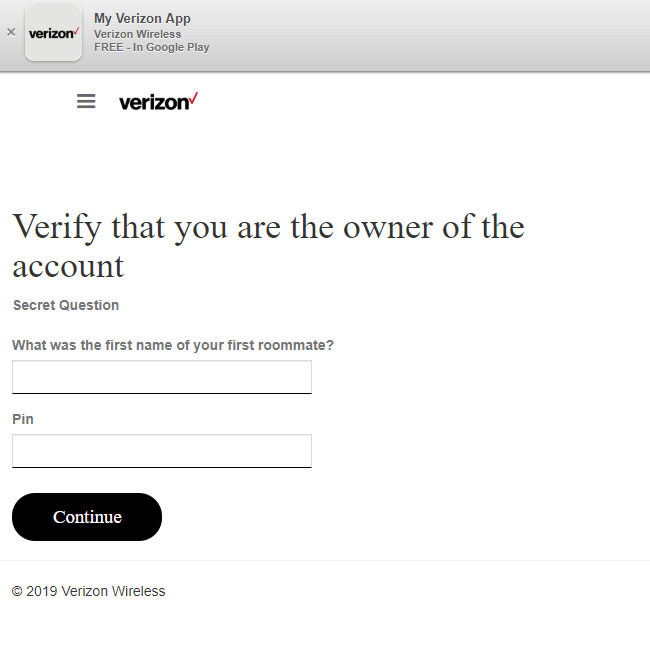
"Jane" and "1234" took us briefly to a page that told us "Thank You. Your Discount Will Apply in 48 Hours." We then were bounced to the real Verizon Wireless website.
Why crooks want your mobile-phone account
Mobile phone account takeovers are especially dangerous because the accounts hold a ton of information about you, and because mobile phone numbers, rightly or wrongly, have become proofs of identity although they were never designed for that purpose.
In 2018, a minor epidemic of T-Mobile account takeovers led to crooks using other people's Apple Pay and similar phone-connected payment services to rack up huge fraudulent purchases.
"For anyone that fell victim, there is a very real risk of identity theft or account takeover," Richards wrote, "further compounded by the fact that mobile devices are frequently used in two-factor authentication."
No gloating, AT&T customers
Not to be outdone, AT&T Wireless may have its own phishing campaign to deal with. Microsoft's Windows Defender Security Intelligence Twitter account announced Monday (April 1) that "an active phishing campaign is targeting AT&T customers."
"Malicious PDF documents attached to email messages pose as payment conformation [sic] and have a link pointing to a phishing site, typically hosted on a compromised website," the Microsoft tweets elaborated. "The documents may use file names like AT&T_Online_03_29_19.pdf, AT&T_03_29_19.pdf, ATTBusiness_03_29_19.pdf, AT&T_Account_03_29_19[22512].pdf. "

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
 Club Benefits
Club Benefits





