Microsoft
Latest about Microsoft

Don't buy a new PC for Windows 11 just yet — this lightweight version can save your old Windows 10 PC
By Darragh Murphy published
Microsoft is ending Windows 10 support this October, but this lightweight Tiny11 Builder is giving old PCs another way to upgrade to Windows 11.

Want to keep Windows 10? Here’s the one thing you must do before the October deadline
By Darragh Murphy published
Microsoft is officially ending Windows 10 support on October 14, and if you plan on staying on the OS, there's one crucial way to extend its life.

OpenAI to launch a LinkedIn competitor — here’s what CEO Sam Altman revealed at the White House tech dinner
By Amanda Caswell published
OpenAI is launching a LinkedIn-style job platform and certification program to train 10M Americans in AI by 2030. Here’s what that means for jobs.

TP-Link router flaws lets botnets attack Microsoft 365 accounts — check yours now
By Amber Bouman published
Two vulnerabilities in end-of-life TP-Link routers are linked to a botnet that is being used to attack Microsoft 365 accounts.

Microsoft's next big Windows 11 25H2 update isn't going to make anyone happy — here's why
By Darragh Murphy published
Microsoft has revealed its big Windows 11 25H2 update, but don't expect a full OS upgrade, as it doesn't add any new features. It actually takes some away.
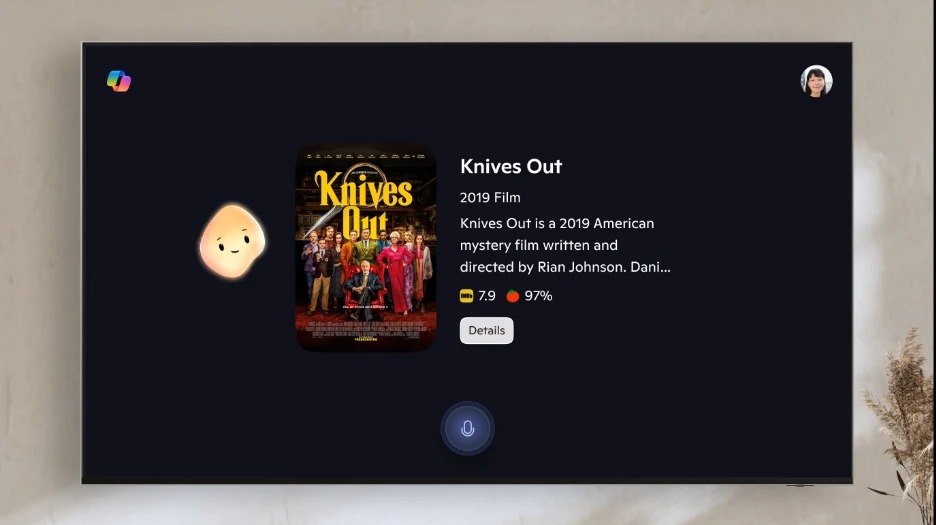
No, not Bixby — Microsoft's AI assistant invades Samsung smart TVs and monitors
By Scott Younker last updated
Samsung and Microsoft partner up to offer Copilot AI on Samsung TVs and monitors — and you can use it right now.

Microsoft is Making it Even Easier (and Cheaper) to Stream Games via Game Pass — Everything You Need to Know
By Scott Younker published
Xbox Cloud Gaming is coming to Game Pass Core and Standard subscribers, and more.

I just tested the ROG Xbox Ally — here's 3 things I love about it (and 2 that I don't)
By Jason England published
Not yet ratedI just played games on the ROG Xbox Ally and ROG Xbox Ally X, and after testing them, we could be looking at two of the best gaming handhelds you’ll be able to buy.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!

