microsoft
Latest about microsoft

5 reasons I still love my Xbox — even if the hardware is 'dead'
By Kaycee Hill published
Microsoft’s console still deserves your love in 2025. Here's why the Xbox is as relevant as ever.

ChatGPT is reportedly building a Google Workspace and Microsoft Office rival — here's what we know
By Amanda Caswell published
ChatGPT is designing a major upgrade that rivals Google Workspace — here’s why I’m all in.

Windows 10 dies in October — 3 ways to avoid upgrading to Windows 11
By Alex Wawro published
It's easy to safely stick with Windows 10 into 2026 — here's how

Score! Microsoft Surface Laptop gets epic price cut at Best Buy
By Louis Ramirez published
This Microsoft Surface Laptop and Surface Pro with Snapdragon chips are among the most powerful AI laptops you can get. Here are my favorite models on sale at Best Buy.
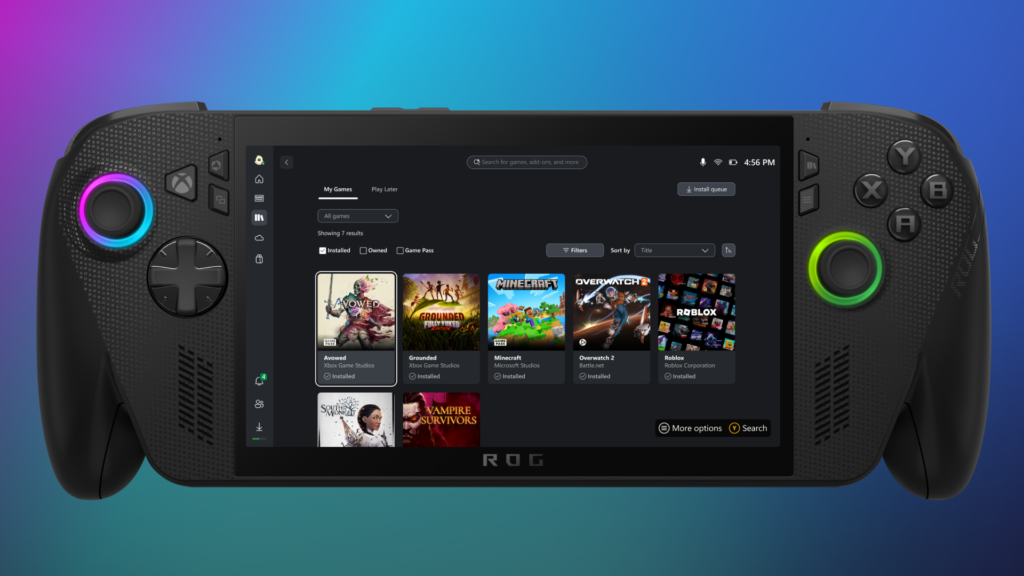
Steam is coming to the Xbox PC app on Windows — and you can try it this week
By Scott Younker published
Xbox Insiders will be able to see Steam, Battle.net and Xbox games in the Xbox PC app on Windows.

Fixing your broken Windows 11 PC is about to get even harder — here’s why
By Anthony Spadafora published
Microsoft is shortening the amount of time System Restore points will be available for your Windows PC, which means you’ll need to create them more often.

Meta Quest 3S Xbox Edition image leaks and it could arrive this week — here's what we know
By Darragh Murphy published
A leaked image of a Meta Quest 3S Xbox Edition has shown up, with the new VR headset rumored to release this week. Here's what you need to know.

Microsoft offers a glimpse at the future of Xbox gaming alongside AMD and Windows
By Scott Younker published
Xbox President Sarah Bond shared a short video teasing the future of Xbox gaming with AMD-based consoles and Windows

Forget Switch 2, ROG Xbox Ally has Steam Deck in its sights — here's why
By Darragh Murphy last updated
The Asus ROG Xbox Ally is Microsoft's big push into handheld gaming, but it isn't gunning for the Nintendo Switch 2. It's got Valve's Steam Deck in its sights.

ROG Xbox Ally: Everything we know about the two new gaming handhelds from Microsoft and Asus
By Jason England last updated
The ROG Xbox Ally has just been announced — a new Xbox gaming handheld created in partnership by Microsoft and Asus! Here's everything you need to know about it!
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
