Cryptolocker-Like Ransomware Spreads to Android Devices
The ransomware targets visitors to porn sites, then locks up infected Androids, claims to be law enforcement and demands a fine.
Have you been looking at child pornography on your Android phone??! Quick, pay this fine or the FBI will arrest you!
That's how a new type of Android ransomware is tricking people into paying up. Once installed, the malware, dubbed "Koler.A," locks up the phone, preventing users from accessing the home screen and effectively holding the phones ransom until users pay $300.
MORE: 7 Scariest Security Threats Headed Your Way
"Koler.A," first detected Sunday (May 4) by the pseudonymous French security blogger Kafeine, is one of the first discovered examples of Android ransomware, and the first known "police Trojan" for Android. Fortunately, its bark is worse than its bite.
Ransomware is a type of Trojan horse that encrypts, or sometimes only pretends to encrypt, user files, rendering infected devices partly or completely useless until owners pay up to receive the decryption keys. Police Trojans are forms of ransomware that, instead of ransom notes, display warnings that purport to come from local or national law-enforcement authorities.
Malware tailored just to fit you
Koler.A spreads using malicious traffic-distribution systems (TDS) — short pieces of software placed on websites, often through ads, that redirect visitors to other sites. Malicious TDS's detect visitors' browsers, operating systems and countries of residence, and redirect them to malicious Web pages with embedded browser exploit kits tailored to each victim.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
In the case of Android devices, the visitor's browser will be redirected to a fake pornography website that will try to trigger a drive-by download (which won't work if the device is set to reject any app from outside the Google Play store).
However, even if the download succeeds, the Android user will have to manually approve the app's installation. The malware creators have to trick users into thinking the malicious app is harmless.
How do the ransomware creators trick these discerning porn site visitors? By promising more porn, of course! Kolar.A presents itself as BaDoink, a video player app that often needs to be installed to view streaming porn on mobile devices.
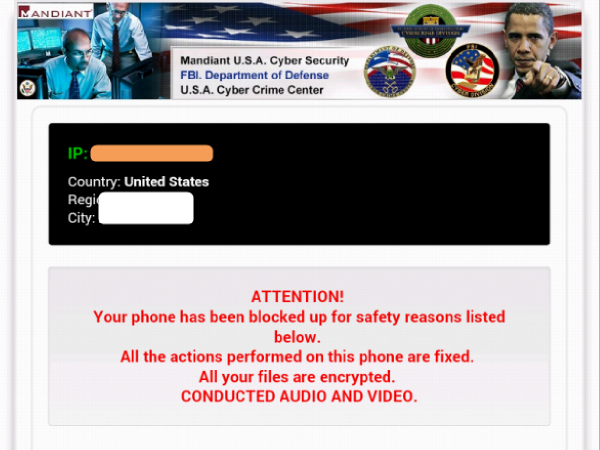
If users are tricked into installing Koler.A, their phone or tablet's homescreen will be replaced by a browser overlay that purports to be a "notice" from the authorities, informing the victim that he or she has viewed, stored or distributed illegal pornography containing images of children, bestiality or rape — and that the device has been "blocked for safety reasons" as a result.
The "warning" demands that in order for the device to be "unblocked," users must pay a "fine" of $300 via MoneyPak, a service for reloading prepaid payment cards, or via other online payment systems.
The Queen is not amused
Because the malicious browser redirect has already detected the visitors' IP addresses and grouped them by residence, Koler.A will present different police warnings and languages to victims in different countries.
American victims will see an FBI logo and a picture of President Obama angrily pointing his finger; French victims get Prime Minister Francois Hollande; British ones get a stern policeman, a suspect pinned down on a patrol car and a bemused-looking Queen Elizabeth II.
Bogdan Botezatu, a malware analyst with Bucharest, Romania-based Bitdefender, told Ars Technica that if the user tries to escape the "police" warning by hitting the device's home button, the warning will simply reappear after 5 seconds. That normally wouldn't be long enough to uninstall the ransomware app, unless it happened to be in the first screen of the device's applications list.
As is standard with police Trojans, the fake law-enforcement notification claims that all files on the victim's device have been encrypted, rendering them inaccessible, and that the "law enforcement" will only decrypt them if the fine is paid.
However, neither Kafeine nor Botezatu found no evidence that Koler.A actually does encrypt any files. Rather, it seems to be playing on fears of the infamous PC ransomware Cryptolocker, which does encrypt infected devices' files.
Bitdefender told Ars Technica that 68 people worldwide had already fallen for Koler.A, mostly from the United Arab Emirates and United Kingdom.
Kafeine discovered Koler.A in the wild earlier this month, after having seen Russian-language ads for very similar malware on black-market websites back in February. He theories that the cybercriminal gang behind the Reveton ransomware has paired up with another ransomware group to develop this threat.
The ad from February, which Kafeine translated into English using Google, is yet another example of how cybercrime has become diversified and organized. It offers a full-service malware package for rent to prospective criminals, just as a legal app developer might sell subscriptions. The ad even offers customer support and statistical analysis.
Koler.A needs users to manually install it onto Android devices, so you can easily protect yourself by going into your device's security settings and making sure it won't allow installation from "unknown sources" outside the Google Play store.
As of today, most Android anti-malware apps detect Koler.A, offering another layer of protection should common sense fail you.
Email jscharr@techmedianetwork.com or follow her @JillScharr and Google+. Follow us@TomsGuide, on Facebook and on Google+.
Jill Scharr is a creative writer and narrative designer in the videogame industry. She's currently Project Lead Writer at the games studio Harebrained Schemes, and has also worked at Bungie. Prior to that she worked as a Staff Writer for Tom's Guide, covering video games, online security, 3D printing and tech innovation among many subjects.
-
jimmysmitty Reply13248647 said:68 people worldwide? What a massive threat...
It will spread. If this is anything like the more advanced Cryptolocker, the one that sends the decryption key to a private server, then this is going to be nasty. The last one would encrypt all files on any HDD connected to the system be it SATA, USB or even network then encrypt the hash then send to decryption key to a private server. If you didn't have a recent backup, paying was the only way to get the key. -
makaveli316 You don't need an antivirus or antimalware on your smartphone, you need a functional brain...Reply -
abbadon_34 Reply68 people worldwide? What a massive threat...
The rest really were doing something "bad"
-
Alec Mowat I haven't used an anti virus in many years. And I haven't had a virus in just as many. At some point in your life, you learn not to install software that's obviously a virus.Reply -
clonazepam I removed the Windows PC version of this malware from my brother-in-law's computer lol... I had so much fun role-playing along with the threat as I removed it... scared him pretty good.Reply
