Lenovo Releases Superfish Removal Tool
Lenovo has posted a tool to remove the Superfish adware, which breaks secure Web connections of Lenovo consumer laptops.

Chinese PC maker Lenovo late yesterday (Feb. 20) released a removal tool for the dangerous Superfish adware that Lenovo had pre-installed on many of its consumer laptops. Hours later, a security researcher demonstrated how easily the adware could be used to hack into online financial transactions.
The Lenovo Superfish removal tool can be found at http://support.lenovo.com/us/en/product_security/superfish_uninstall. It must be downloaded first, but will run without installation. Lenovo has released the tool under a public license and placed the source code on the developer website Github so that security experts can analyze and possibly improve on it.
(If you have a Lenovo laptop, you can check whether it is affected by using each installed Web browser to visit https://filippo.io/Badfish/.)
MORE: Lenovo's Security-Killing Adware: How to Get Rid of It
Early today (Feb. 21), Robert Graham, CEO of Atlanta-based Errata Security, posted detailed instructions on his blog on how to create a malicious Wi-Fi hotspot to exploit the security vulnerability that the Superfish adware creates on Lenovo laptops.
"This example proves that this exploit is practical, not merely theoretical, as claimed by the Lenovo CTO," Graham wrote.
Graham used a Raspberry Pi 2, which is a minicomputer that costs about $35, a $10 Wi-Fi adapter and a microSD card, which can be had for as little as $4. The software was all freely downloaded from the Internet, and it took Graham about 3 hours to build the device and get it running.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
To demonstrate the flaw, Graham used a laptop on which the Superfish adware had been installed to connect to the Internet using his malicious hotspot. He tried to log into the Bank of America website using a fictitious name, and showed that the hotspot intercepted the connection and logged the fictitious name. It would also have logged the password, had there been one.
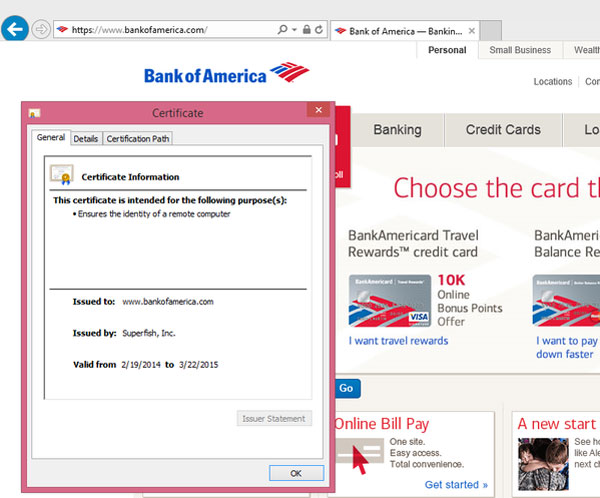
For about $50, a malicious hacker could build a similar hotspot, name it "Starbucks HotSpot" and bring it into your local coffee shop. Any user of an affected Lenovo laptop who connected to the Internet using that hotspot could have all her or his banking, social-media and shopping sessions intercepted and decrypted, and the associated accounts broken into and taken over.
How Superfish works, and why it's dangerous
Superfish is an American-Israeli company, and its adware, called Visual Discovery, analyzes images of retail products displayed in a Web page, then adds advertisements showing similar or identical products for sale at other locations online. This is done without the consent of the website operator or the laptop user.
Many forms of unwanted adware can pull off this trick on unencrypted Web pages, but Superfish goes further. By breaking the Web browser's system of secure connections, it can inject ads even into encrypted "HTTPS" websites, such a secure retail site -- or a banking website.
Superfish can do this because Lenovo pre-installed the adware and added Superfish's digital signature to the list of "root certificates" that Windows trusts to guarantee a secure Web connection. As a secure Web page's information travels from the network connection (either an Ethernet port or Wi-Fi card) to the Web browser, Superfish intercepts it, decrypts it, adds its own ads and then re-encrypts it using its root certificate.
The laptop user will be none the wiser, and will believe he or she is still viewing a secure Website. Because this "man-in-the-middle attack" takes place entirely within the computer, the website operator will not be aware that the secure connection has been broken.
That's arguably unethical, but wouldn't be inherently dangerous had every Lenovo laptop used an entirely different certificate to re-encrypt the connection.
But they don't. Every Lenovo installation of Superfish uses the same private key to verify the connection. On Thursday, Graham decrypted that universal private key and revealed that its password was "komodia."
Komodia is the name of an Israeli company that makes two pieces of software, called SSL Digestor and Redirector, which Superfish apparently used to decrypt and then re-encrypt the secure Web connections.
Security researcher Marc Rogers analyzed other pieces of software made by Komodia, including a parental-control product called "Keep My Family Secure." Rogers wrote on his blog that the private keys for the other pieces of software also always used the password "komodia."
Problem? What problem?
Lenovo's first response when the Superfish flaw went public Thursday (Feb. 19) was to deny that there was anything to worry about.
"We have thoroughly investigated this technology and do not find any evidence to substantiate security concerns," the company said in its initial statement.
But by the end of the day, the company had changed its tune.
"We're sorry. We messed up," the Lenovo U.S. Twitter feed said. "We're making sure it never happens again."
Lenovo reiterated that the Superfish adware had been installed only on consumer laptops manufactured between September 2014 and January 2015, and would no longer be used. However, the Superfish company itself was adamant about the safety of its products in a statement to Ars Technica's Dan Goodin.
"Despite the false and misleading statements made by some media commentators and bloggers, the Superfish software does not present a security risk," a company representative told Goodin.
The Superfish company has not made any other public statement about the Lenovo situation.
- Your Router's Security Stinks: Here's How to Fix It
- Best Antivirus Software and Apps
- 10 Best Mobile Browsers
Paul Wagenseil is a senior editor at Tom's Guide focused on security and gaming. Follow him at @snd_wagenseil. Follow Tom's Guide at @tomsguide, on Facebook and on Google+.

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
LordVoldemoo I just found superfish on my Lenovo bought in January 2014. Are the dates in the article correct?Reply -
Paul Wagenseil ReplyI just found superfish on my Lenovo bought in January 2014. Are the dates in the article correct?
That's very interesting. So you bought the computer a year ago, and you're sure Superfish is on it? Let me ask: Over the course of that year, did you install any software updates pushed out by Lenovo?
