Evil Charging Cables Can 'Video Jack' Your Smartphone
A new charging-cable attack on smartphones can steal info by simply broadcasting it on a screen, and there's no easy defense against it.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Daily (Mon-Sun)
Tom's Guide Daily
Sign up to get the latest updates on all of your favorite content! From cutting-edge tech news and the hottest streaming buzz to unbeatable deals on the best products and in-depth reviews, we’ve got you covered.

Weekly on Thursday
Tom's AI Guide
Be AI savvy with your weekly newsletter summing up all the biggest AI news you need to know. Plus, analysis from our AI editor and tips on how to use the latest AI tools!

Weekly on Friday
Tom's iGuide
Unlock the vast world of Apple news straight to your inbox. With coverage on everything from exciting product launches to essential software updates, this is your go-to source for the latest updates on all the best Apple content.

Weekly on Monday
Tom's Streaming Guide
Our weekly newsletter is expertly crafted to immerse you in the world of streaming. Stay updated on the latest releases and our top recommendations across your favorite streaming platforms.
Join the club
Get full access to premium articles, exclusive features and a growing list of member rewards.
Frequent travelers know they have to be careful about where they plug in USB-connected devices to recharge. Security researchers have long warned that USB charging cables at conferences, airports and other public places can steal smartphone information, but the latest twist on this attack is absolutely beautiful in its simplicity — it can steal your info by simply broadcasting it on a screen.
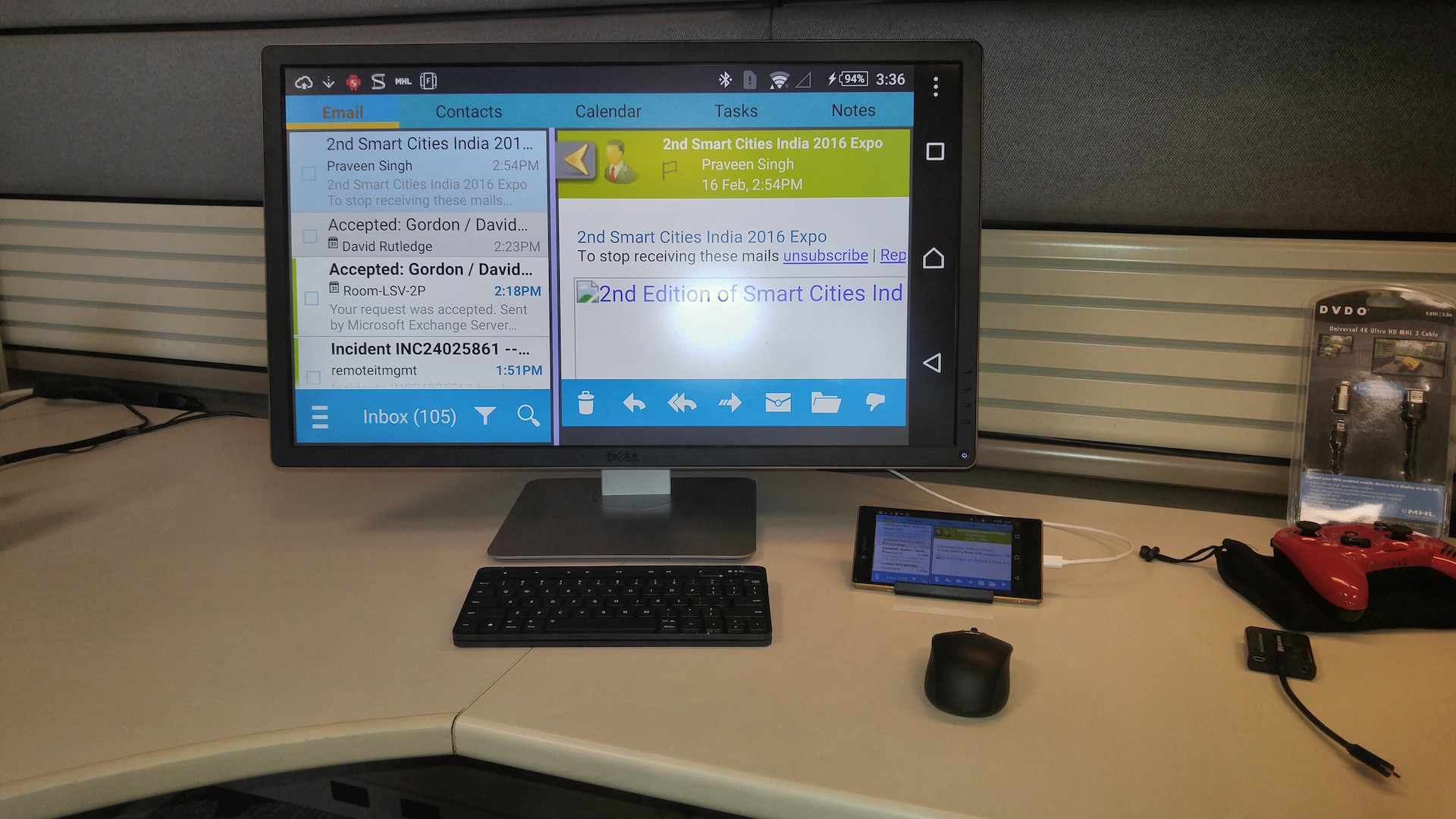
Independent security journalist Brian Krebs took a deep dive on the proof-of-concept attack, which he saw demonstrated informally at the DEF CON 24 hacker conference in Las Vegas earlier this month. The attack is so delightfully straightforward, it's a miracle no one's ever thought to use it before.
As you may be aware, many high-end smartphones running on both iOS and Android can transmit their screen displays or video to an external monitor via HDMI. The exact technology varies by phone, and not all phones have the built-in hardware, but you can buy a USB-to-HDMI adapter — usually on the cheap — and mirror your phone’s screen on a TV without using unreliable wireless protocols.
MORE: Best Antivirus Software and Apps
The only trouble is that an HDMI-capable USB cable or plug is often indistinguishable from a regular USB cable. Brian Markus, CEO of Aries Security worked with Joseph Mlodzianowski and Robert Rowley, two other accomplished researchers, to see how cheap and easy it would be to steal people's information via video hijacking.
The answer: very cheap and very easy. Using a $40 monitor and about $220 worth of equipment, the researchers devised a USB splitter for use at a public charging station setup at DEF CON. They were good enough to warn users what they were signing up for; actual malefactors probably wouldn't be so kind.
When a user connected his or her phone to the rig, the device would, indeed, start charging. But it would also transmit an exact copy of everything happening onscreen to Markus’s monitor. In a more elaborate version of this setup, the monitor could be in a remote location rather than right next to the charging port, which might make the con a little obvious.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The most common kind of USB-to-HDMI transfer involves standard microUSB plugs, or modified microUSB plugs with more internal pins, but USB-C and Lightning ports can also transfer HDMI signals. Following the DEF CON demonstration, Markus went to an Apple Store and had an employee demonstrate Apple's Lightning-to-USB cable by outputting the screen display from her own iPhone 6 to a video screen -- complete with passcode entry.
Unlike transmitting data via USB, which both Android and iOS warn users about, there's no notification for picking up a video signal. Everything from entering a phone's PIN to logging into banking apps would be ripe for the plucking.
This, of course, is also the hijack's fatal weakness: How many people actually log into sensitive information while using public charging ports? People are just as likely to turn their phones off and wait awhile. Social media and e-mail apps don't require constant logins. And if you're at a busy conference, the last thing you're going to do is stop to pay your credit card bill.
As such, Krebs doesn't think the average person needs to worry about this clever hack too much. Still, if you travel frequently and use public charging spots, you may want to keep your phone off, or restrict your activities to apps that don't require logins or display sensitive information. After all, if you do something embarrassing, there could be video evidence of it.

Marshall Honorof was a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.
-
Daekar3 Public charging ports? Good gravy, who would use such a thing? That's like plugging a random USB key you found into your computer, or leaving your home wifi open.Reply
 Club Benefits
Club Benefits










