iOS Malvertising Scam Tricks Millions of Users
A cybercriminal group known as ScamClub recently redirected millions of American iOS users to shady phishing sites.
Malvertising is nothing new. But a malvertising campaign that targets specifically iOS users in the United States, then racks up more than 300 million impressions in about two days – that's something we haven't seen before.
A cybercriminal group known as ScamClub recently redirected millions of users to shady phishing sites, all through seemingly legitimate advertisements that had been vetted by a major ad exchange.
The story comes from Confiant, a New York-based security firm that studies the confluence of online ads and cybercriminality, with additional information from ZDNet.
MORE: Here's the One Gmail Setting You Should Activate Now
The method of attack is tried-and-true; the interesting thing here is the scale. For Nov. 12 and 13, ScamClub worked through a major online ad exchange (both sources were too gentlemanly to name it), and got a bunch of malicious advertisements to show up on iOS-optimized websites. The malicious ads have been removed from this ad exchange, but it continues on smaller ad networks that have been running ScamClub ads since August.
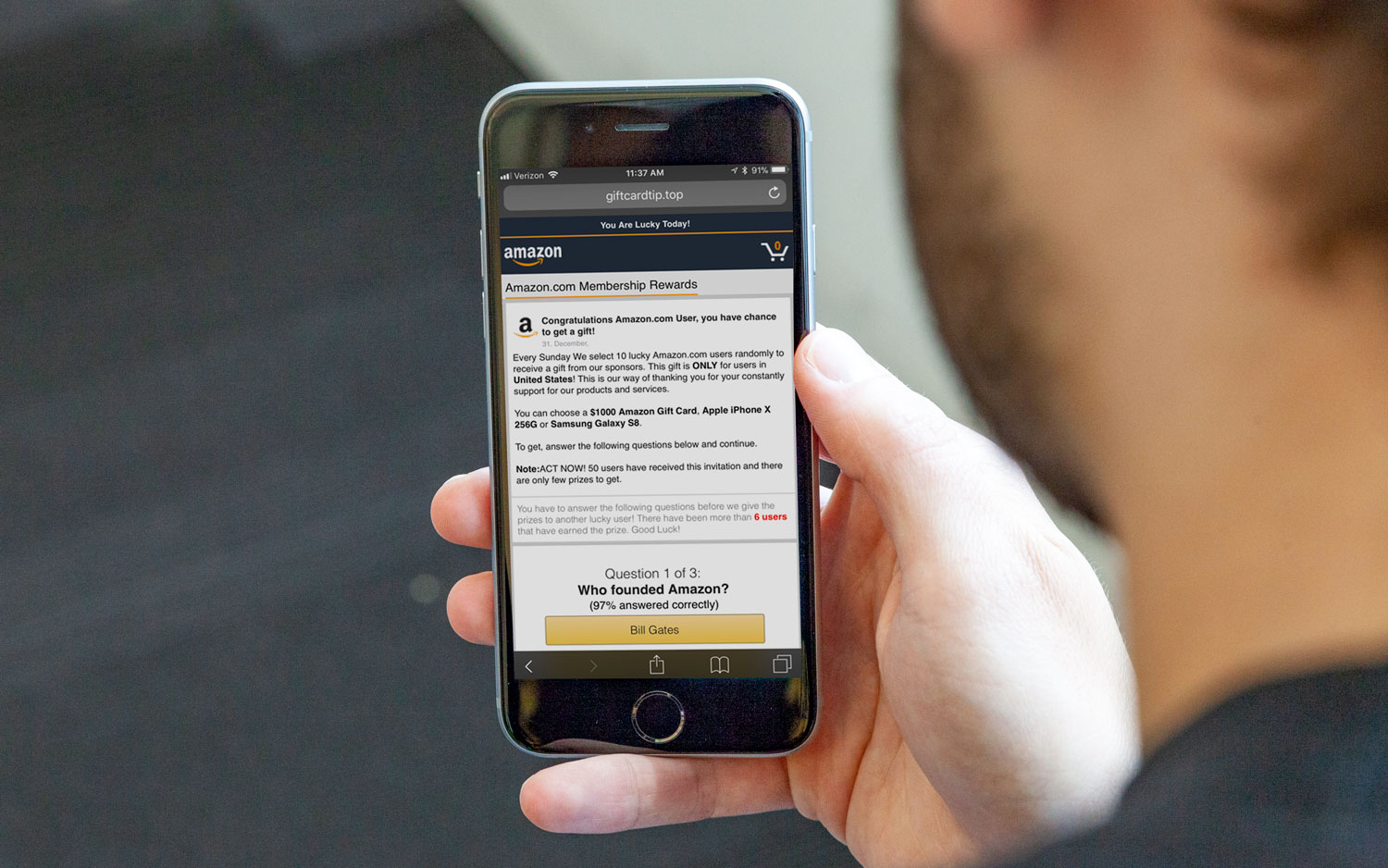
These ads redirect users, against their wills, to shady sites. (One reason why malvertising is so pernicious is because it often doesn't require user input.) Once redirected, users would face the usual gift cards and pornography. The sites promised Amazon shopping sprees and/or the promise of attractive young ladies to coax e-mails, passwords, credit card information and other personal information.
Confiant already got in touch with the major ad exchange and stopped the bulk of the campaign dead in its tracks. But as it's still going on, albeit at a lower rate, and other malvertising attacks will happen in the future, you can prevent malvertising hijacks by running an ad blocker on your phone. However, doing will prevent publishers (like this one) from generating revenue. If you get redirected to a phishing site, close your browser and don't give it any information.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
There is no infectious malware involved in this campaign, so if anyone has lost his or her information, it's because he or she volunteered it. It's not clear whether ScamClub has successfully phished anyone's data, but considering the phishing sites got 300 million impressions in two days, we'd be surprised if no one has fallen for it.
MORE: Best VPN Service - Reviews of Top-Rated VPN Providers
One interesting aspect of the attack is that 99.5 percent of impressions came from the United States, and 96 percent of them came from iOS devices. While iOS may be more secure than other OSes in general, it is clearly still susceptible to some of the most common cybercriminal tricks – as are its users. Furthermore, ad blockers are considerably more common on desktop PCs, which could lead organizations like ScamClub to turn their attention to mobile instead.
As for why a large ad exchange let this scam slip by, part of the reason is because ScamClub hid the destination websites very well. Many advertisements used "play.google.com" as their click-through URL, which suggests a legitimate app from the Google Play Store. (Why advertisers would want to push Google Play Store apps on iOS users is worth questioning, but it's not inherently suspicious.) Furthermore, Google had not yet identified the two scam-ridden domains (hipstarclub.com and luckstarclub.com) as threats, leaving Chrome users on iOS wide open.
If there's a lesson here, it's that malvertising is becoming just as dangerous as researchers feared – and as cybercriminals hoped. With two days and two domains, one enterprising group managed to capture 300 million impressions from a highly targeted demographic (American iOS users). And worse attacks could be on the way.

Marshall Honorof was a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.
 Club Benefits
Club Benefits