CryptoLocker Malware Offers Victims 'Second Chance' to Pay Ransom
The CryptoLocker ransomware is granting victims an expensive 'second chance' to regain their encrypted files.
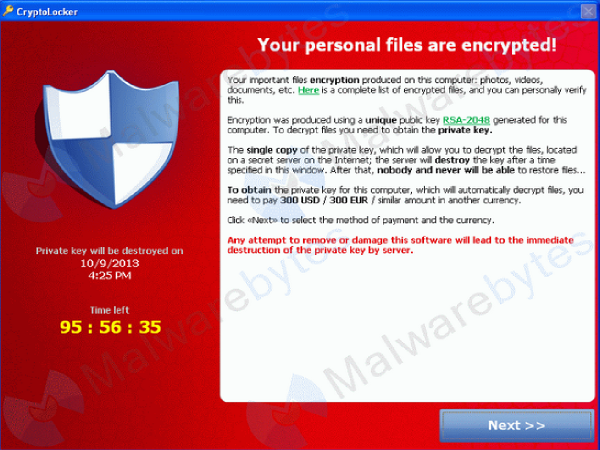
CryptoLocker, the dangerous new form of malware that's been sowing panic in America for the past few weeks, at least on local television newscasts, has added a new twist.
Victims who missed paying the ransom for their encrypted files will receive a "second chance" option to get back their data. Unfortunately, it'll also cost them much more.
Like other forms of ransomware, CryptoLocker encrypts or freezes large parts of a Windows PC's hard drive, then asks the user to pay up to regain access.
MORE: 13 Security and Privacy Tips for the Truly Paranoid
CryptoLocker's innovation has been to add a time limit — users have three days to pay the ransom of $300, 300 euros or 2 Bitcoins — before the encryption key is "destroyed" and the data lost forever. A displayed countdown clock adds to the sense of urgency.
But what if you let three days pass without paying the ransom? The new "feature," which appeared Nov. 1, will allegedly let users purchase decryption keys, but at a much higher price of 10 Bitcoins (about $2,200).
This "offer" doesn't exactly make infected users' lives any easier, but it does give them a second chance to recover their files.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The existence of the "second chance" also reveals that, despite the CryptoLocker criminals' claims that decryption keys are destroyed after three days, the criminals must actually store the keys.
CryptoLocker infects Windows PCs through malicious email attachments or through backdoors already installed by previous forms of malware.
Once it's installed on a computer, the ransomware silently starts encrypting many sorts of user files, including those created by Microsoft Office and Adobe Creative Suite software. (Windows and most applications will continue to operate normally.)
Because this encryption process can take a while, it's sometimes days before users are aware they've been infected by Cryptolocker.
CryptoLocker first appeared several months ago, but in recent weeks the criminals behind it stepped up their game. Because many victims preferred to lose their files rather than hand over credit-card information, the criminals added a Bitcoin option so that users could at least keep their financial information private.
How CryptoLocker works
Ransomware, or malware that holds your data hostage until you pay, has been around for more than two decades. CryptoLocker is the nastiest form of ransomware encountered, and the hardest to break.
Once CryptoLocker installs itself, it contacts a remotely operated server run by the criminals, called a command-and-control server. On that server, the criminals create a unique set of encryption keys for each individual machine using the RSA encryption algorithm —one key to encrypt the computer's data, and one key to decrypt it.
MORE: Best Anti-Virus Software Review
Only the encryption key is sent back to the infected computer. The decryption key never leaves the criminals' servers.
CryptoLocker uses the encryption key to encrypt user files found on the primary infected computer, as well as on all networked computers to which the first computer has access.
That means if you use an infected computer to connect to a work VPN, all the computers on that network could become infected as well.
Worst of all, there doesn't seem to be a way to decrypt files, aside from paying the criminals. Even if a user succeeds in removing the CryptoLocker ransomware itself, the user files remain in an inaccessible, encrypted state.
How to defend against CryptoLocker
The best way to defeat ransomware like this is through prevention. Make sure your anti-malware software is up-to-date, as most anti-virus solutions will catch and destroy the CryptoLocker Trojan before it can act.
Check to be sure you don't already have any other malware on your computer, as CryptoLocker can use previously installed backdoors.
Be extremely cautious about strange or suspicious emails in your inbox, and don't open any email attachments unless you absolutely trust the source. Even then, use anti-virus software to scan the attachments first.
Backing up your data, either on the cloud or on a physical device like an external hard drive, also protects you from CryptoLocker — at least in some cases.
Manual backups, either to a physical device like an external hard drive or to the cloud, will be safe so long as they don't auto-sync with an infected device.
Or, if you discover the infection before your auto-backup replaces your files with the encrypted versions from your computer you can simply delete the encrypted files, wipe the malware, and then restore your backups to your machine.
But if your backup processes run automatically, then backups stored on attached or networked storage drives will soon be encrypted by CryptoLocker as well, as will files shared with constantly updating cloud backup services such as Dropbox.
For CryptoLocker-specific defense, security blogger Brian Krebs recommends several different free services, among them CryptoPrevent by security consulting company Foolish IT. It's a free tool for home PC users that detects and blocks CryptoLocker from being installed.
For small businesses and networked devices, Krebs recommends the free CryptoLocker Prevention Kit from enterprise consulting firm Third Tier.
Email jscharr@techmedianetwork.com or follow her @JillScharr and Google+. Follow us @TomsGuide, on Facebook and on Google+.
Jill Scharr is a creative writer and narrative designer in the videogame industry. She's currently Project Lead Writer at the games studio Harebrained Schemes, and has also worked at Bungie. Prior to that she worked as a Staff Writer for Tom's Guide, covering video games, online security, 3D printing and tech innovation among many subjects.
-
seshysama This has become an increasing problem for our IT office. I've spoken with Symantec on it, and they say that Cryptolocker WILL NOT SPREAD THROUGH A NETWORK. it will encrypt every file the infected computer has access to, which includes network drives, so it WILL mess up shared server files, but it can't spread. (as per Symantec)Reply -
nevilence Wow I didnt even know this kind of malware existed, luckily I have always been anal about having antivirus on my PCs.Reply -
glasssplinter With everything the NSA tracks and whatever why are things like this not stopped? You would think that they would have a credit card and could enter the information in and see who picks it up on the other end. Chances are though this is probably made by the NSA to pad their coffers. Pretty nasty infection though, wonder what it will be like to tell your customer that you can't recover any of their data.Reply -
jimmysmitty Reply11862772 said:This has become an increasing problem for our IT office. I've spoken with Symantec on it, and they say that Cryptolocker WILL NOT SPREAD THROUGH A NETWORK. it will encrypt every file the infected computer has access to, which includes network drives, so it WILL mess up shared server files, but it can't spread. (as per Symantec)
It will not spread but it is nasty. We have dealt with it for two customer, one of them twice.
Had to restore their entire public share server (50-150GB) twice.
The best way to stop it is to block .exe and .zip attachments as it normally sends as a .zip and will be form_xxx.pdf.exe in the .zip folder. -
heero yuy and why does stuff like this work? because windows lets anything run without asking the userReply
and an admin account has access to every file on the computer (and I think normal accounts do as well :/)
if all my games were on Linux I would be using that right now but unfortunately they are not (but steam os and stuff might change that :D) -
littleleo Why can't the feds track the payment info and bust the criminals? They are a growing problem for all countries perhaps Interpol can track and arrest these criminals.Reply -
dimar User's just have to be extra careful. Think of using a computer just like driving a car. Basically, pay attention.Reply -
koga73 I have UAC in windows turned all the way up to prompt for credentials before allowing admin rights so I'm covered. No A/V just common sense and strong passwords.Reply -
pcichico I run a small computer store and we do on average $8500/month in computer repair which is mostly virus removal. Last week a customer brought their machine in with crytolocker and I figured its just like all the other fake av programs claiming doom and gloom. Pretty suprised to see something that was actually doing what it said. In 13 years of running this business this is the first time I've seen a virus/malware that actually lead to data loss. The timer had already run out when the dude brought it in. Had a ton of word docs and pdfs all toast. Pretty slick too how most cloud backups are worthless against it. Since the files aren't erased but slightly altered the cloud service sees it as a change and replaces the files with the "updated" ones. Best defense is something like Acronis that has weeks worth of incremental backups to choose from. Made me rethink the cloud backup service we provide to our own customers. Should be called the walking dead virus. Files still there but nobodies home.Reply -
virtualban And cops and lawyers go after file sharers and can't get real internet criminals? Like, really?!Reply
What are they being paid for?
While lawyers are being paid by the interested party, the the rest law system is being paid by taxpayers, so, judges should throw senseless cases out, and take this kind of cases in. Same going for law enforcement.
