The Human Element - Protecting Yourself Against Cybercrime on Social Media

It's easy to forget. Cybercrime is about more than sophisticated attacks and malicious software. Scam emails and malicious websites are not the only potential infection vectors.
There's more to staying safe online than guarding yourself against malware and avoiding ransomware. There's more to protecting yourself than shoring up your devices and using a virtual private network. There's also a human element to cybercrime, a human force behind the abuses and dangers you face online.
We already touched on this to an extent when we discussed how you can recognize the red flags of digital phishing and fraud. Today, we're going to explore that topic with a bit more depth as it pertains to keeping yourself safe on social media. We'll start with a bit of a refresher on fraud.
How to spot a social media scam

The anatomy of a social scam is incredibly similar to that of an email scam. The fraudster behind it uses a wide array of different tactics in an effort to get people to follow a particular course of action. Depending on the fraudulent activity the criminal is looking to commit, this may involve any of the following:
The good news is that if you understand how to spot fraudulent emails, you're already well-equipped to avoid the lion's share of social media scams. As we said, they use very similar tactics and often have ultimately the same goals. A little knowledge and mindfulness go a long way here.
If something looks too good to be true, it is
Don't trust third parties that claim they're giving away gift cards. Unless you're following an established, trusted brand that regularly hosts such giveaways, you're not getting a gift card or a vacation. You're getting scammed.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Be wary of clickbait
These social posts that attempt to grab your attention with a shocking headline. Check every link before you click it. The more outlandish an article appears, the warier you should be.
More often than not, the most unbelievable, spammy-sounding articles are digital fishhooks. They aren't designed to inform or entertain, but to defraud. On the rare occasion when there actually is an article on the other side of the link, it's an incoherent pile of word salad.
Government agencies and authority figures will almost never message you on social media. That incredibly attractive single who seems unusually interested in you is very likely a bot. That job offer you just got a LinkedIn message about - the one you never applied for - probably isn't legit.
We'll talk about how you can tweak your privacy settings to avoid messages like this later in the piece.

Is a friend messaging you asking for financial help? Did someone randomly send you a link they claim is about you? Do you have a family member who sent you an attachment with little warning and even less context?
Call them. Contact them outside the social network. At worst, you'll have verified they're still in control of their account and just acting a little out of sorts.
At best, you just let them know someone has either hacked their account or is posing as them.
If you're on Facebook, there are plenty of apps and games you can play with friends. Exercise caution. These often have blanket access to your profile and by association a ton of personal data. Worse yet, that Flash plugin required to watch the shocking video you just clicked installs a browser extension that has complete control of every page you visit.
Speaking of personal data, that's a perfect lead-in to our discussion on privacy settings.
Keeping your personal information private

By default, social networks don't tend to treat your privacy with a great deal of respect. Why should they? The more information you freely offer them, the easier it becomes for their advertising partners to understand you.
Thing is, a lack of privacy exposes you to more than creepily-relevant targeted content. It also opens you up to everything from fraudulent friend requests to outright cyberstalking. Now, we're going to assume that if you're reading this, you already have a fairly large online footprint.
You're probably logged into multiple websites via Facebook, you have an Instagram account, you're active on Twitter, and you maintain a LinkedIn profile. This is to be expected, and aside from manually editing a ton of content or outright deleting all your profiles, there's not much you can do to eliminate your online footprint at this stage.
You can, however, reduce it.
First, every major social network has a section in its settings for privacy and security. Ideally, you should review them all and make your security as high as possible. When you're done, everything should be fully locked down in the following way:
Second, moving forward, be careful what you share online.

Understand that the Internet is permanent. Every comment, every photo, every piece of personally identifiable information, every quiz can ultimately be traced back to you. To that end, it may be wise to disable location sharing.
Finally, you might want to consider using a tool like Tineye or Google Reverse Image search to periodically check your Facebook profile. You may also want to consider periodically searching your name, both on Facebook and via Google.
That way, if someone's trying to pose as you, you can potentially catch it sooner rather than later.
While they're usually more frequent on dating apps, catfish are still quite common on social media. These imposters create a fake persona for themselves online, posing as someone else in all their digital interactions. The motive varies with each individual catfish, and they aren't always nefarious.

While it's true that some catfish may play the part in an attempt to defraud lonely men and women, others are in it for the romance. Lonely, insecure, and often socially-awkward, they find it easier to pretend they're someone else when interacting with others. Others are a bit more malicious, and simply get a thrill out of manipulating people.
In some cases, such as what happened with Ashley Madison, they're in it for blackmail - to gather compromising images or information they can use to extort their hapless victim.
Whatever the motive, catfish usually share multiple traits in common. If romance is part of the equation, the relationship usually progresses unnaturally fast. They use their social media account either rarely, or excessively, and they're full of wild and elaborate stories.
Perhaps the biggest red flag of a catfish, however, is that they refuse to offer you any sort of proof of their identity. They always have some excuse for why they can't video chat, they aren't keen on sending you any pictures, and if they live nearby, it's never a good time for the two of you to meet.
Staying safe on social

Protecting yourself and your privacy on social media requires mindfulness and a healthy dose of common sense. That's not the only thing you'll need, however. For those moments when your attention falters, it's important that you install proper security software - like the award-winning Bitdefender Total Security.
Through a series of sophisticated tools and components, it's a complete security package designed to protect your devices and data both online and off. In addition to advanced ransomware protection, threat detection, and antispam, Bitdefender Total Security also features social network protection to keep you safe from malicious links and other online threats that may unwittingly be passed to you by friends.
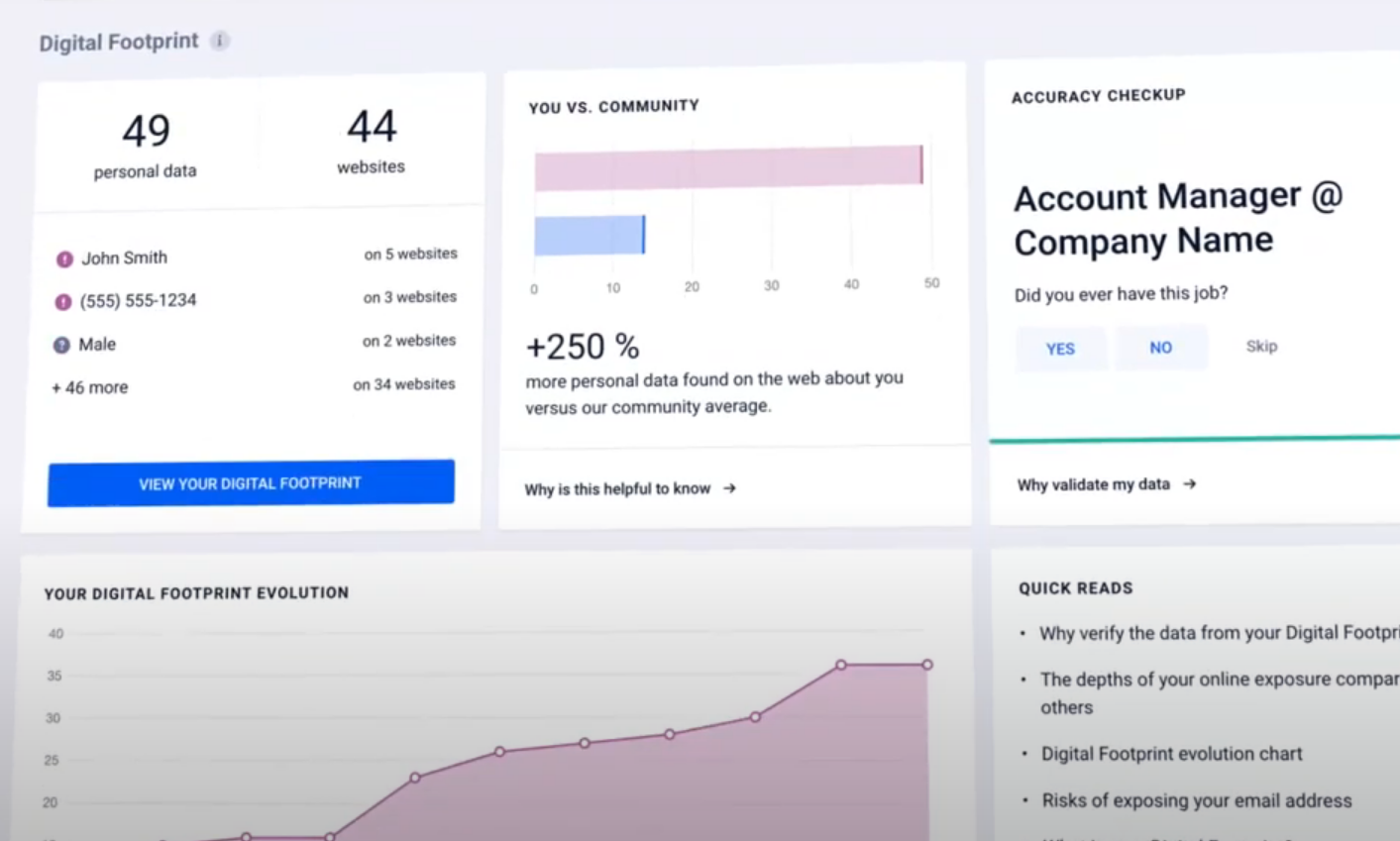
If you're particularly concerned about protecting your personal data, Bitdefender Digital Identity Protection is also an excellent choice. A powerful digital identity management tool, it continuously trawls both the Internet and the dark web for your information. If your personal data has been exposed or your reputation may be at risk - such as through someone impersonating you on Facebook - it immediately notifies you, empowering you to take action to protect yourself.
Now that we've discussed the vast array of threats on the web let's get a bit more specific and talk about your own system. Next time, we'll examine the ins and outs of file encryption, and why you should be using it if you aren't already doing so.
 Club Benefits
Club Benefits





